In addition to highlighting five notable file uploads and endpoint scans made by our community users each month, I thought it was important to visualize the code reuse connections between the malware detected and their respective malware families.
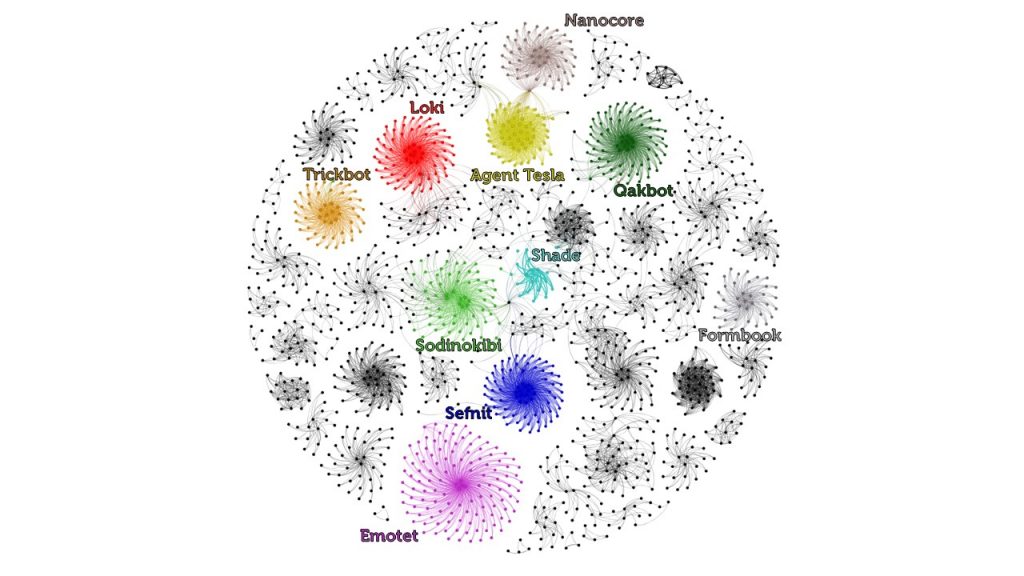
The following graphic represents a mapping of file uploads made to the Intezer Analyze community in June 2019. Each cluster is comprised of nodes representing individual files that were detected as malicious and classified to a specific malware family, based on code reuse and similarities.
The mapping demonstrates genetic, aka code reuse, connections between the malware samples, in addition to correlations between 10 different malware families.
Connections Between Malware Samples
Using Emotet as an example, each dot or node in the purple spiral represents a community sample that shares at least some code with Emotet, which is a very common banking trojan. The Emotet cluster is the largest spiral in the graphic, which signifies that Emotet had the highest percentage of code reuse between the various malware samples detected by the Intezer Analyze community in June.
Connections Between Malware Families
The gray and black clusters represent other malware families, however, for the sake of this analysis we have chosen to highlight 10 malware families.
The strength of the connection between different malware families—measured by the percentage of shared genes—can be determined based on the width of the connecting line between two clusters. In this instance, we can see that there are not many connecting lines between the labeled malware families. This is significant in that it means these 10 particular malware families are not well connected.
For example, while there is a strong connection between different Nanocore payloads, Nanocore displays a weak connection to Agent Tesla. Notably, there is one file located in the center between Nanocore and Agent Tesla, which means this particular sample shares code with both malware families. However, this is only one file, and the strong code connection is not representative of the main Nanocore and Agent Tesla clusters.
Recent Trends:
-
- The importance of code reuse. The mapping further supports the idea that malware authors reuse code. Different malware samples can often be connected to the same malware family or threat actor based on code reuse. This is why it is crucial to index an attacker’s code. Once you have detected and indexed an attacker’s code, even if he or she employs small portions of the code again, defenders will be able to detect and classify any future variant of the malware.
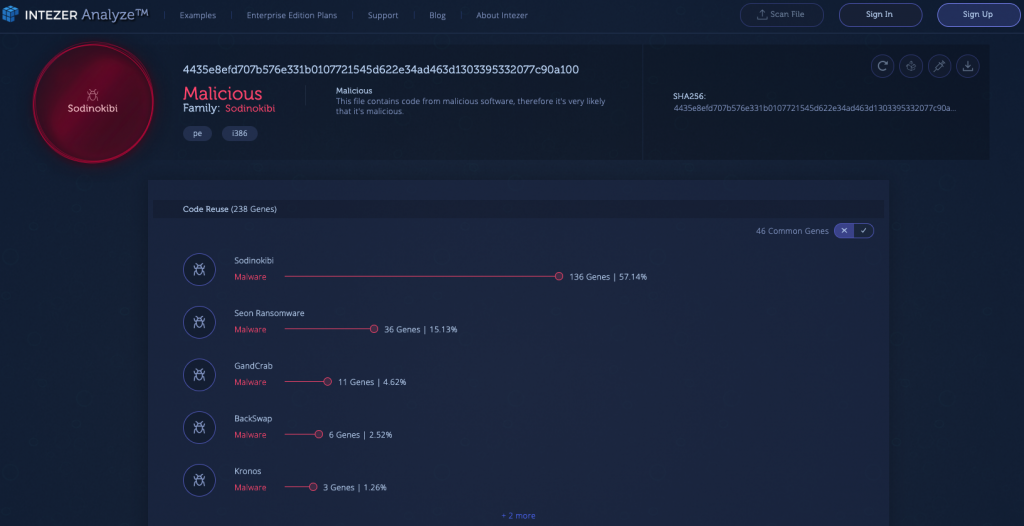
- Connections between Sodinokibi and GandCrab. One of the malware families highlighted in the graphic is the Sodinokibi ransomware. Sodinokibi is a ransomware as a service (RaaS), similar to GandCrab’s model, which offers monetary packages for distributing and managing ransomware campaigns. In recent news, researchers at Trend Micro published an article pointing to a potential link between Sodinokibi and the GandCrab ransomware. This connection is further supported by the analysis of a recent community upload (below), which was classified as Sodinokibi and shares 11 genes with GandCrab.
- Emotet persists. Emotet continues to be one of the most common banking trojans leveraged by attackers. While many Emotet samples utilize customized packing mechanisms in order to evade detection, by unpacking Emotet automatically in Intezer Analyze we can identify code reuse between the different malware samples. More about Emotet and mitigating this threat, in two of our recent blog posts:
Going forward, we will be analyzing the genetic connections between the various malware samples and their malware families detected and classified by the Intezer Analyze community. This information will be posted on our social media feeds on a monthly basis. For more information, follow us on Twitter and LinkedIn at @IntezerLabs.
If you are not already an Intezer Analyze community user, I encourage you to sign up for free at https://analyze.intezer.com/#/. Registration takes only a few minutes and you will immediately be able to determine if your suspicious file or endpoint contains malicious code.