This month’s community highlights span a variety of file formats — APK, ELF and PE.
1) Anubis [Link to Analysis]
Anubis is an Android banking trojan designed to take control of mobile devices and steal credentials or hold data for ransom. The malware has been deployed as part of several cybercrime campaigns in recent years, mostly through phishing emails containing a malicious APK file. The file is automatically downloaded and executed, asking for permissions to enable Google Play Protect — however, it’s actually gaining full permissions on the device.
Once installed, Anubis can use keylogging and access all data on the infected device.
In the analysis below we can see a Dex file located within the malicious APK. The file is classified by our system as Anubis, based on shared code with previous Anubis samples.
Intezer Analyze now supports Genetic Malware Analysis for Android applications
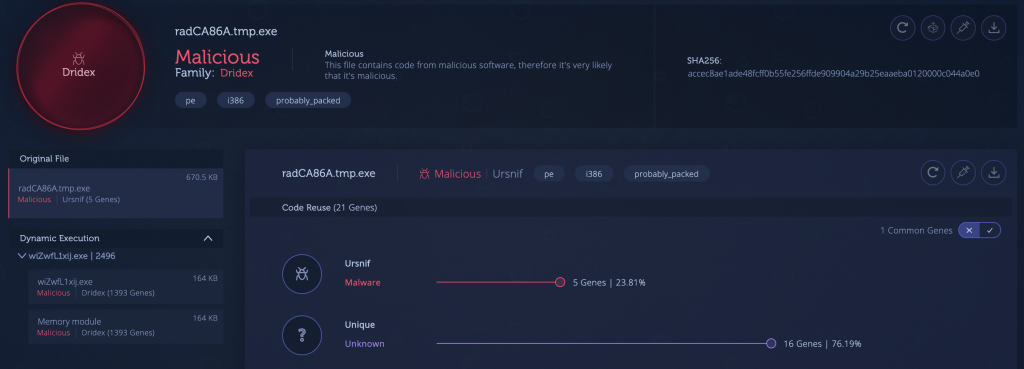
2) Dridex [Link to Analysis]
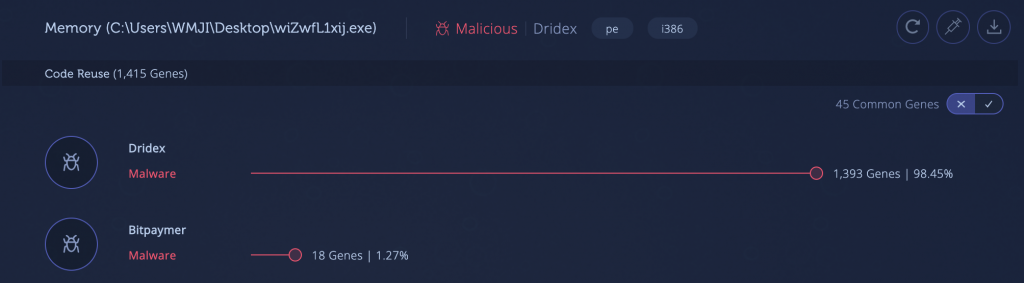
Dridex is a popular information stealing malware known to be active in various versions since 2012. This threat usually arrives via malspam campaigns with some packing, utilizing evasion techniques to avoid detection. The analysis below demonstrates one of the packing techniques used by Dridex. Interestingly, the sample shares code with Ursnif, which suggests this packer has been used by both threats. We can also see small code connections (18 genes) to the Bitpaymer ransomware, a more recent information stealer which is believed to have evolved from Dridex.
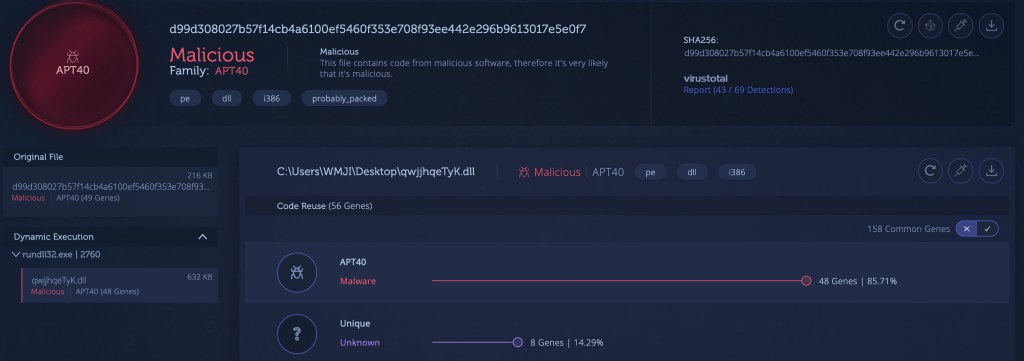
3) APT40 [Link to Analysis]
APT40 — also known as Leviathan — is a nation-state sponsored threat group with alleged Chinese origins. This group has been active since at least 2014, and has been known to target maritime agencies, naval defense contractors and research institutions in the United States and western Europe.
These targeted attacks usually begin with spearphishing specific targets, to deliver their tools and infect a machine. The initial stage is often a Microsoft Office document with VB macro scripts which can download additional malware onto the host.
In the analysis below, we can see a DLL file which shares over 85% of its code with APT40.
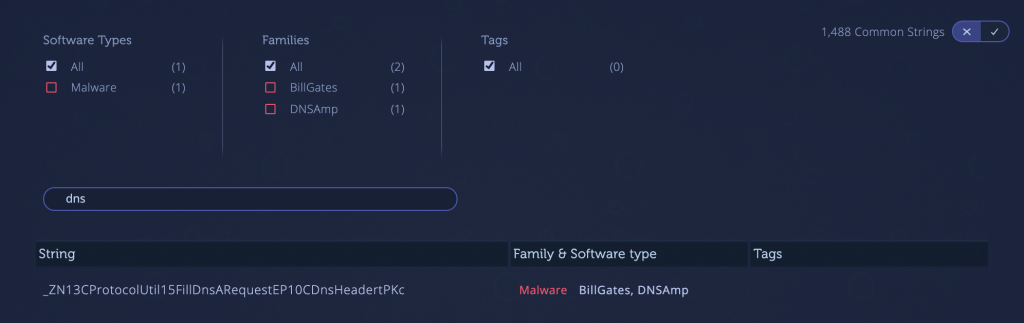
4) DNSAmp [Link to Analysis]
The sample below is a Linux DDoS tool which uses DNS amplification to target servers and disrupt their normal operations. As we see in most Linux malware, shared code exists between many malware families. This community sample has genetic connections to other DDoS malware, such as BillGates, DDOS.TF and DDoS.Manager.
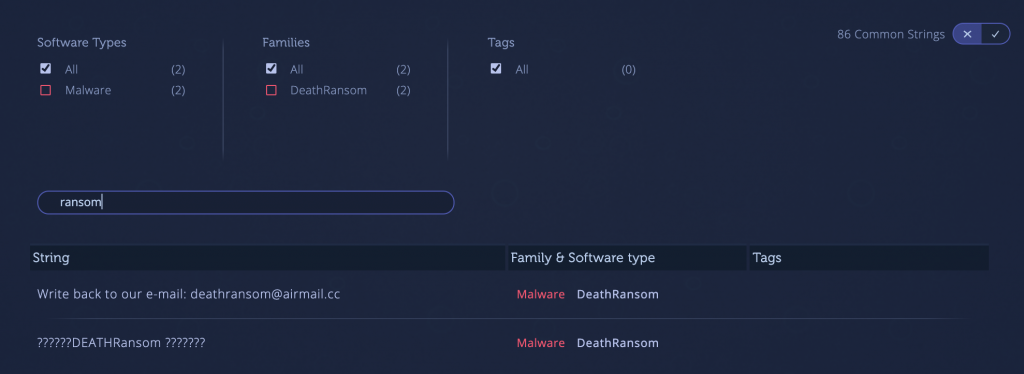
Using the string reuse feature in Intezer Analyze, you can search for and identify strings that tell you more about the nature of the threat:
5) DeathRansom [Link to Analysis]
As its name implies, DeathRansom is a ransomware used for encrypting data on infected machines. DeathRansom isn’t a new threat, but it has made news recently with its latest version, first reported in late 2019. While the ransomware wasn’t taken seriously in the beginning — it was largely unsuccessful encrypting files — the latest versions of this malware are using complex encryption methods.
This ransomware doesn’t attempt to conceal its identity, evidenced by revealing strings. Try it now by searching for ‘ransom’ in the string reuse section of the below analysis.
Join the Intezer Analyze Community Today
Join the thousands of members using Intezer Analyze to aid in their malware investigations. Quickly analyze files and devices to detect Android, Linux and other cyber threats. Sign up for free and get results within seconds.