ELF SUPPORT
We would like to proudly announce that Intezer Analyze™ now supports genetic malware analysis for ELF binaries! You may now upload ELF files to our system and find code reuse. We have already indexed the genes of millions of different files into our ELF genome database, classified into both malicious, trusted, and neutral (libraries) software. The support extends to ELF binaries that have been compiled in either the x86 or x86_64 architectures.
INTEZER ANALYZE™ ELF FEATURES
Here are the features that are currently available for ELF files:
- Code Reuse
- View Related Samples
- String Reuse
- View Shared Code / Unique Code
- Vaccination (Enterprise)
- IDA Plugin (Enterprise)
VAST WORLD OF ELF MALWARE
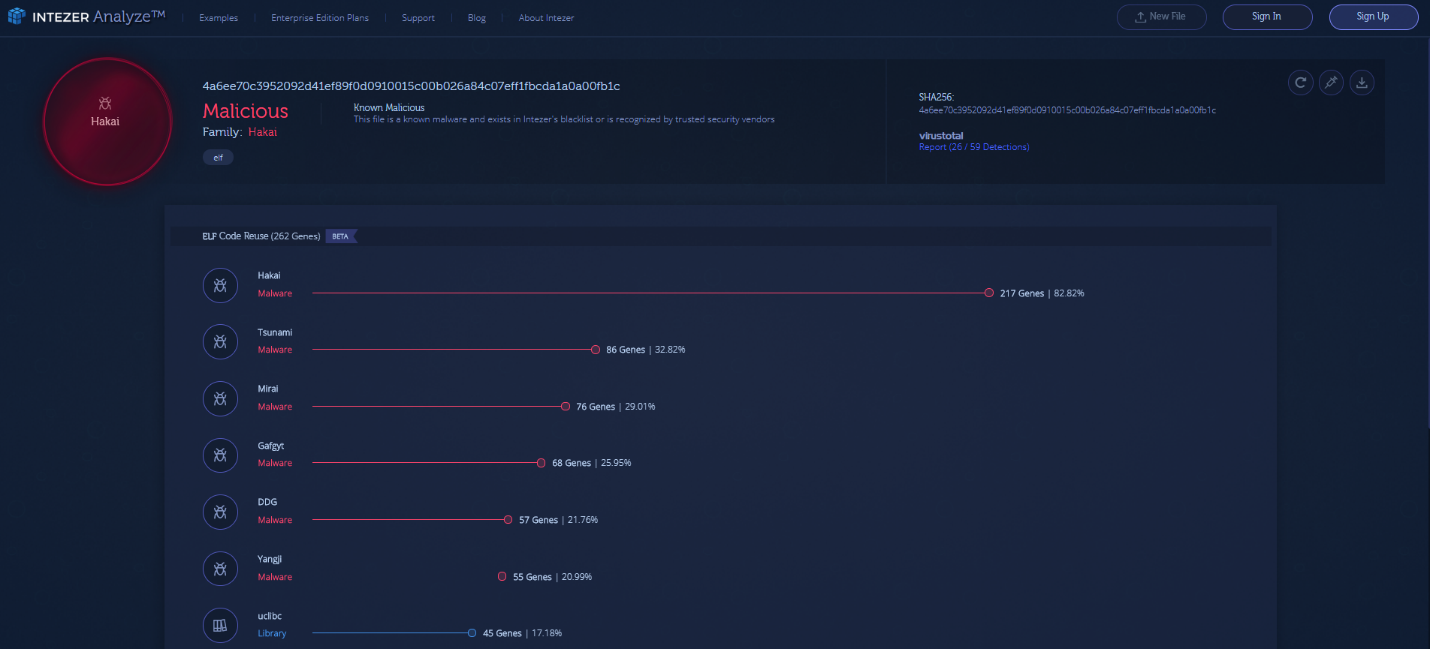
A lot of malware created for Linux flies completely under the radar when it comes to detection. There are many different types of malware we have seen, from cryptominers to APTs, and much more to be discovered. We would like to show you an example of an ELF analysis in our system by using Hakai (based off Mirai) and its direct variants.
https://analyze.intezer.com/#/analyses/10cf5913-9b2d-455b-9187-14115b9dff4f
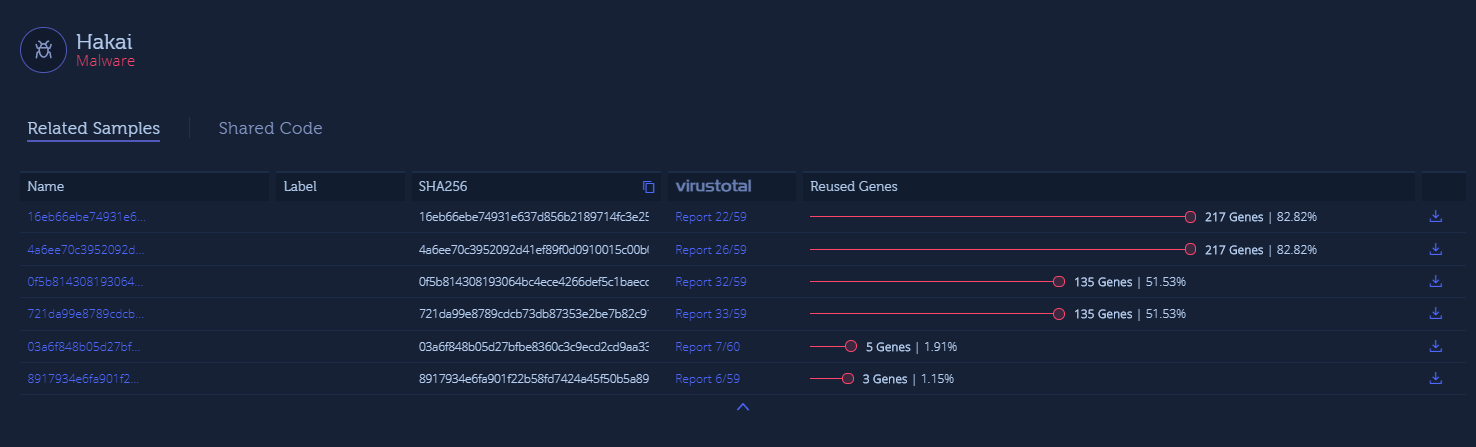
If we dive in to the related Hakai sample, we can see an evolution of code from other variants.
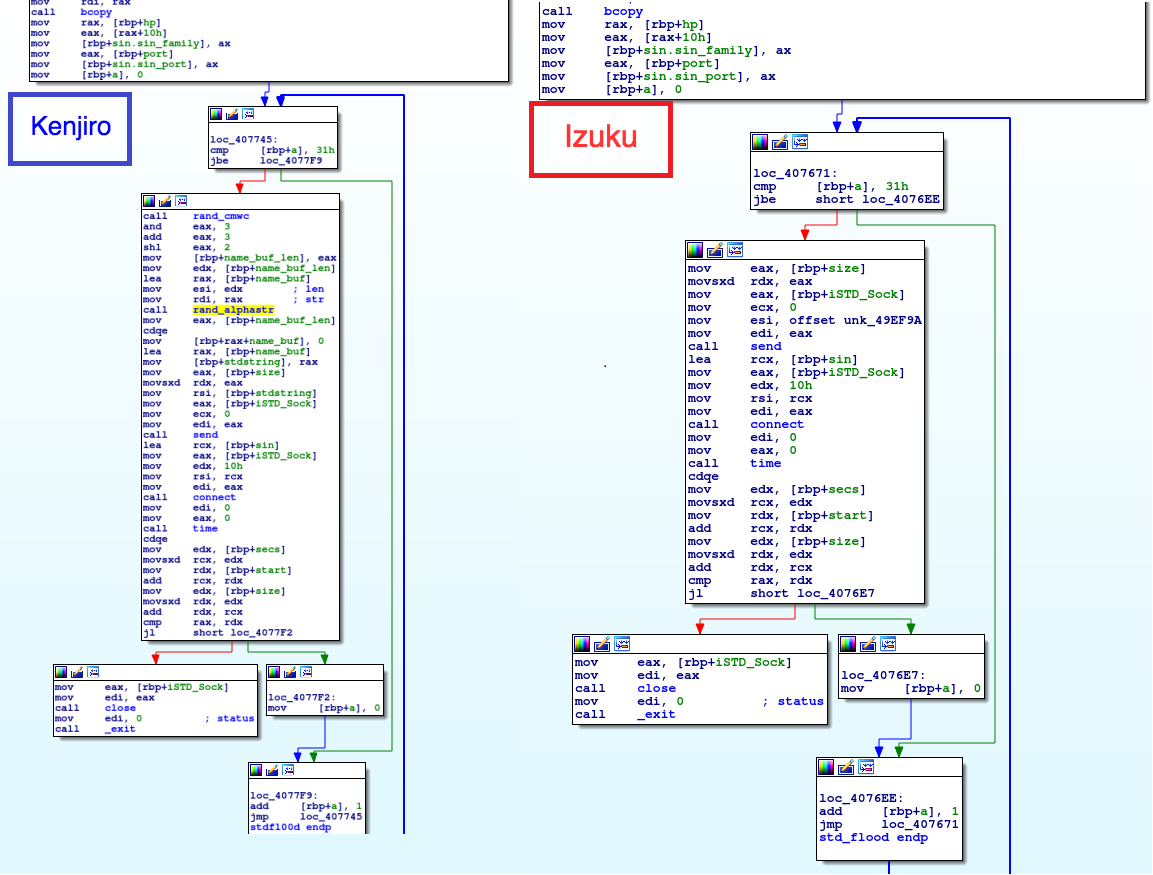
HAKAI VARIANTS: KENJIRO & IZUKU
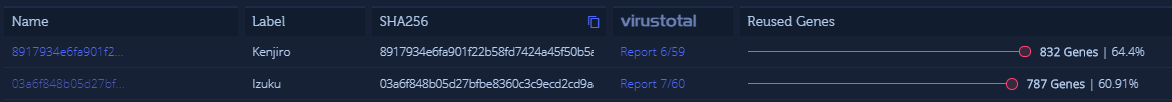
We would like to demonstrate an example of malware that shows how useful looking for code reuse is by showcasing variants off Hakai with low detections on VirusTotal, Kenjiro (6/60), and Izuku (7/60). According to Intezer Analyze™, the code base is almost exactly the same for both Kenjiro and Izuku, but the C&Cs are different and also the strings the malware seems to use to name itself.
We decided to dive a bit deeper to see the small changes in the code. After further investigation, we could see Kenjiro seems to be an upgraded version of Izuku. One of the differences between Kenjiro and Izuku is that it changes its UDP flood algorithm to add some randomization to the buffer, where Izuku’s flood algorithm uses the same string.
We can also see in the code that these Hakai variants use 4 exploits to spread:
- D-Link DSL-2750B – OS Command Injection (https://www.exploit-db.com/exploits/44760/)
- CVE-2015-2051 (https://www.exploit-db.com/exploits/37171/)
- CVE-2017-17215 (https://www.exploit-db.com/exploits/43414/)
- CVE-2014-8361 (https://www.exploit-db.com/exploits/37169/)
TRY IT OUT
We invite you to try out our new support of ELF binaries by registering to our free community edition of Intezer Analyze™. We are still working on adding more data to our system in order to give you better results on your upload. Stay tuned for new features and blog posts that will include future ELF malware research!
IoCs
Kenjiro 8917934e6fa901f22b58fd7424a45f50b5a89f9daa871a69b45d6a39191c9f1b
Izuku 03a6f848b05d27bfbe8360c3c9ecd2cd9aa33d43702186c62c4a115e23383983
Hakai Variants:
16eb66ebe74931e637d856b2189714fc3e25baf8af5ba41bb75f976ca56ee307
4a6ee70c3952092d41ef89f0d0910015c00b026a84c07eff1fbcda1a0a00fb1c
0f5b814308193064bc4ece4266def5c1baecc491117f07650c5117762648d4c5
721da99e8789cdcb73db87353e2be7b82c9158e2929b9eaa7d5b4660b6d4d1e2
C&Cs:
46[.]166[.]185[.]42
77[.]87[.]77[.]250
178[.]128[.]185[.]250
148[.]72[.]176[.]78
hakaiboatnet[.]pw