Checklist for protecting your Linux cloud servers against cyber attacks
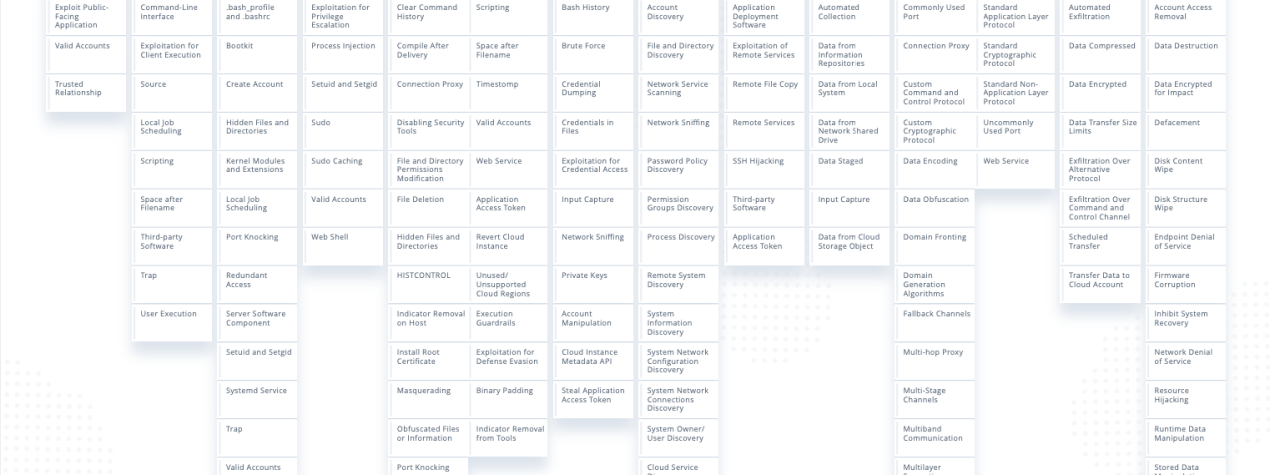
Taking inspiration from the MITRE ATT&CK® framework, we have developed a matrix categorizing adversary tactics and techniques for Linux cloud servers. We believe this is significant because Linux cloud servers are common in modern production environments.
The MITRE Corporation is doing tremendous work assembling a global knowledge base of adversary tactics and techniques. ATT&CK is used by threat hunters, red teamers, and defenders alike to classify attacks and better assess an organization’s risk. Security teams use these matrices to describe attacks on different platforms by explaining adversary techniques, methods, and attack flow.
While there are enterprise matrices for both Linux and the cloud, there is no matrix representing adversary tactics and techniques for Linux cloud servers.
For example, the Linux Matrix includes techniques such as spear phishing link and credentials from web browsers but there are no browsers on servers. The Cloud Matrix covers techniques for attacking the cloud platform—such as abusing cloud instance metadata API and cloud service dashboard—but it does not address attacks on servers themselves.
Increase in cyber attacks targeting cloud servers
In 2019 our researchers observed an increase in the number of cyber attacks targeting Linux servers. According to CBT Nuggets, nearly 90 percent of all public cloud servers are developed on the Linux platform. We foresee the number of attacks targeting Linux cloud servers to increase as businesses transition to the cloud due to COVID-19.
It is our recommendation that security teams use the TTPs matrix for Linux cloud servers as a checklist to protect their infrastructure against adversary tactics spanning initial access, lateral movement, and more.
Download the TTPs matrix for securing your Linux cloud servers
This resource is not affiliated with, sponsored by, or endorsed by MITRE ATT&CK®, nor does it represent the views and opinions of The MITRE Corporation or MITRE personnel.