2024 was a transformative year as we focused on capturing what makes security analysts exceptional and integrating those skills into our Autonomous SOC solution. This included delivering precise outcomes through AI-driven analysis that mirrors human expertise. By equipping our AI SOC Analyst with access to comprehensive evidence, cutting-edge analysis capabilities, high-quality threat intelligence, and the ability to learn and adapt, we ensured impactful results for the SOC professionals who rely on our solution.
Here’s a summary of the key areas where our R&D made significant progress, reshaping how SOC teams triage alerts.
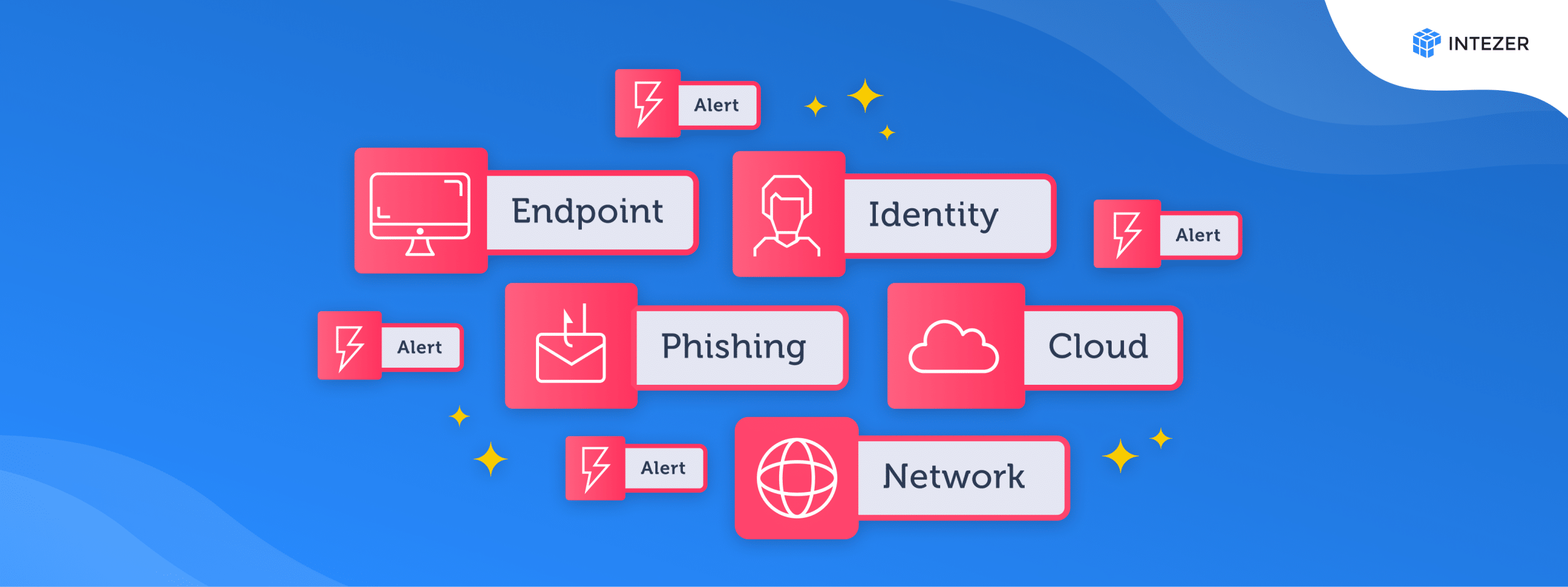
Expanded AI SOC Coverage Across Alert Types
We prioritized broadening our AI-driven platform’s ability to handle diverse alert types. From endpoint and phishing alerts to phishing, identity, and cloud-based threats, our expanded coverage ensures comprehensive security monitoring. Across 500+ customer environments, our platform processed over 5.4 million alerts (not logs, alerts!) in 2024.
Here’s how these alerts were distributed across categories:

| Category | Share of Alerts |
| Endpoint | 47.33% |
| Cloud | 26.96% |
| Identity | 8.56% |
| Network | 6.94% |
| Custom | 5.56% |
| Email/Phishing | 2.77% |
| DLP | 1.87% |
This evolution allows our customers to manage their full alert landscape efficiently and effectively.
Strengthened Integrations and Partnerships
Our platform’s interoperability grew with new and enhanced integrations, making security operations easier by connecting tools and streamlining workflows. These integrations address common challenges like siloed data, inefficient manual processes, and lack of visibility, ensuring unified and actionable insights.
- SIEM Integrations: We added SIEM integrations this year, with native support for Splunk, Microsoft Sentinel, Microsoft Defender XDR, Elastic, CrowdStrike Falcon LogScale, IBM QRadar, Sumo Logic, Devo, Stellar Cyber, Rapid7 InsightIDR, Wazuh, and more coming soon!
- Identity Integrations: New integrations with identity providers such as Microsoft Entra ID and Okta deliver enriched user data and login activity analysis.
- Microsoft Partnership: Extended our partnership with Microsoft by integrating with the entire Defender Suite, including Microsoft Defender for Endpoint, Microsoft Defender for Cloud, Microsoft Defender for Office 365, Microsoft Entra ID, Microsoft Sentinel, and Microsoft Defender XDR, and making Intezer available in the Azure marketplace.
Improved AI Triage and Analysis Quality
Ensuring and elevating the quality of triage and analysis is a core focus for the Intezer team. Our AI and decision-making accuracy are directly influenced by the quality of data and analysis capabilities it accesses. This is why we invested heavily in this area to ensure we provide the best possible results. We introduced:
- Advanced Evidence Collection: Automated evidence collection includes anything from files, network, memory, logs, email, identity data, cloud, and even collecting feedback directly from end users about unusual activities.
- Analysis Tools and Threat Intelligence: Upgrades to our file scanning, memory scanning, endpoint forensics, network analysis, and expanding quality threat intelligence we collect from partners and internally by Intezer’s research team.
- AI Infrastructure Enhancements: Upgrades to our underlying AI models, with better tuning options, with new AI-based triage use-cases, tested in scale, and now running successfully in production.
Tailored AI Solutions for MSSPs
We enhanced our capabilities for MSSP clients to enable better subtenant management, allowing seamless operations for multi-client environments. MSSPs can now connect numerous clients with maximum flexibility, integrating directly into their workflows. This includes direct integrations, a detailed API, and webhook notifications that enable MSSPs to send Intezer’s triage data and recommended actions to SOARs or custom platforms to take action.
AI SOC Results and Verification
In 2024, we introduced a rigorous accuracy testing process to validate the results produced by the Autonomous SOC platform. This process involves:
- Manual Alert Review: Approximately 5% of all alerts are manually reviewed by Intezer analysts and users.
- Random Sampling: Intezer’s expert analysts evaluate a random sample of alerts for performance.
- User Feedback: Security professionals approve or reject triage verdicts, adding a real-world validation layer.
This dual human-in-the-loop approach ensures reliable and trustworthy results, calculated with a 95% confidence level and a margin of error below 2%.
2024 Data: AI Results That Matter for SOC Teams
Our testing revealed outstanding outcomes:
- Definitive Classification: 80.93% of alerts were confidently classified as confirmed threats or false positives. (Other alerts received suspicious or inconclusive verdicts, along with evidence collected and recommendations for further analysis.)
- Fast Investigations: Alerts were processed in an average of 2 minutes and 21 seconds.
- Escalated Alerts: Only 3.81% required escalation, with a 93.45% accuracy rate.
- No Action Needed Alerts: 68.40% were resolved without further action, achieving a 97.68% accuracy rate.
These metrics underscore the reliability and effectiveness of Intezer’s Autonomous SOC solution, providing measurable impact and giving security teams the confidence to focus on critical priorities. Our commitment to accuracy and transparency ensures that new customers can trust Intezer’s technology to deliver consistent, actionable results.
Closing 2024 with Confidence
This year, our platform proved that “AI SOC” is not a distant dream but a reality, delivering measurable outcomes and reshaping cybersecurity operations. From expanding coverage and integrations to refining triage and MSSP support, we’ve built a stronger foundation for our customers to succeed.
Looking ahead to 2025, we’re just getting started. We have great plans to deliver even smarter, faster, and more impactful security operations. This is only the beginning.
I’m very excited about what’s coming next!