Product Tour
Take a spin through Intezer’s AI SOC to see how to automatically triage, investigate and respond to every alert at unmatched speed and accuracy.
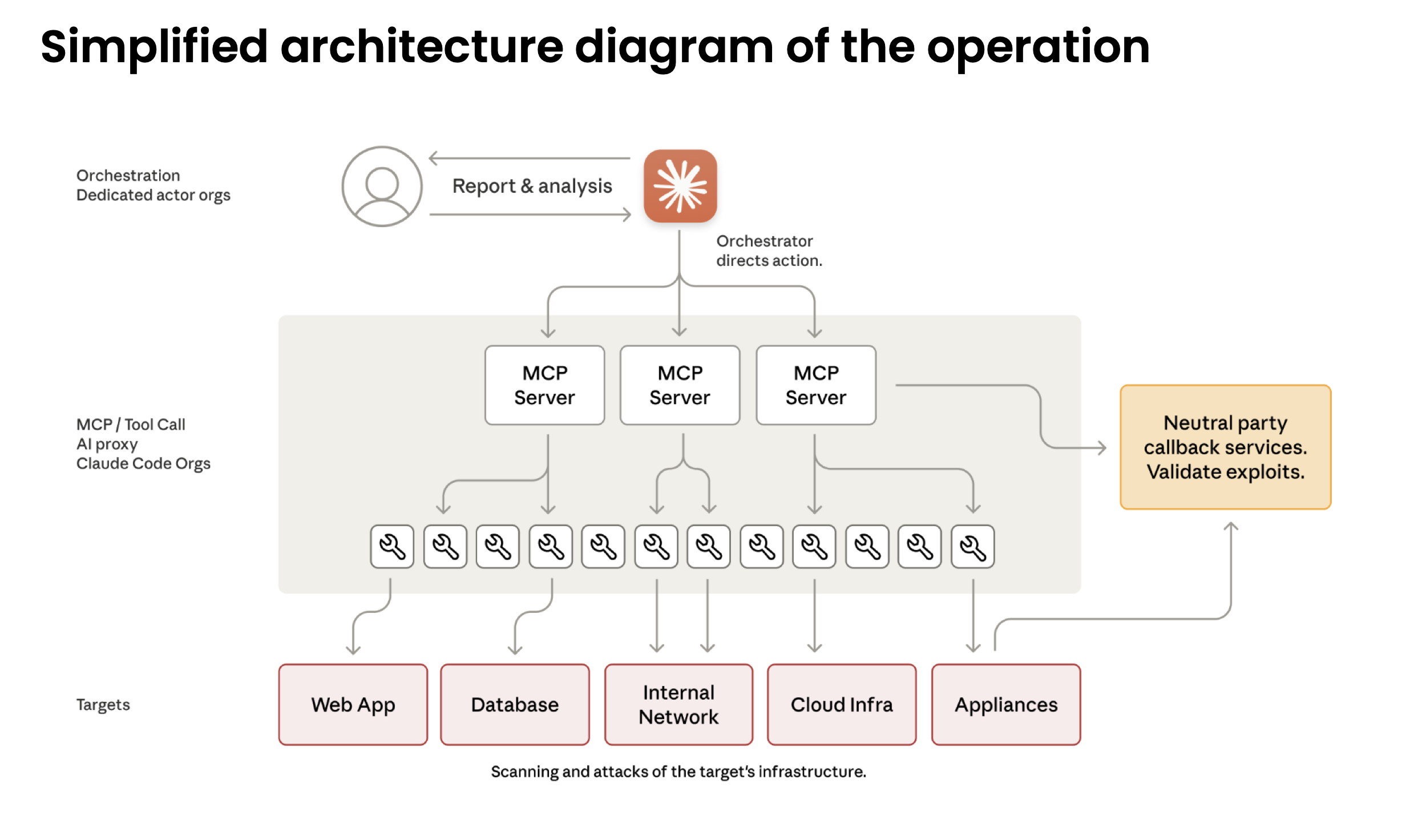
What security leaders can learn from the Anthropic report on the recent AI espionage.

The article introduces a flexible and practical approach to malware analysis for beginners and experts alike.



Discover advanced phishing techniques bypassing email security—Intezer reveals threats hidden in SVGs, PDFs, OneDrive, and OpenXML files.