It can be the difference between maintaining a safe environment for your applications or a compromised machine running malicious code.
Misconfiguration of Docker API ports is one of the most common yet potentially deadly mistakes companies are making. An open API port can lead to an immediate compromise exposing your cloud environment to different types of attacks. One example is Doki, an advanced Linux malware that evaded all common anti-malware solutions in VirusTotal for over 6 months. That means even if you had the most up-to-date solution, the attack would have likely gone undetected.
The Danger of Having an Exposed Port
Misconfigured Docker API ports are constantly scanned for by attackers. A single misconfiguration can allow the attacker to access the Docker daemon or even the cloud server that runs the Docker platform.
Since the API is used to interact with and control the Docker daemon—commonly through CLI commands or libraries (the API offers SDKs for both Python and Golang)—it provides attackers with various capabilities such as:
- Check which containers exist on the server
- Manage containers
- Create and delete containers and container images
- Pull images from Docker hub
- Perform additional commands
Fix your Ports in 4 Simple Steps
The good news is that it takes just 4 simple steps to ensure your Docker API ports are not exposed to the public internet. Our guide lays them out for you.
Muhstik Botnet Targets Containers
The Muhstik botnet has been active since 2018. It’s known to target a wide range of compromised infrastructures such as routers, Oracle WebLogic application servers, Drupal and web servers hosting phpMyAdmin.
Known capabilities:
- Scans for other potential victims
- Conducts distributed denial-of-service (DDoS) attacks
- Runs cryptominers on victim machines
Now, Muhstik is targeting misconfigured Docker API ports, giving it an easy way to control the Docker daemon running on a victim’s machine. With this control, the attacker sets up a new container with an alpine Docker image and executes the botnet.
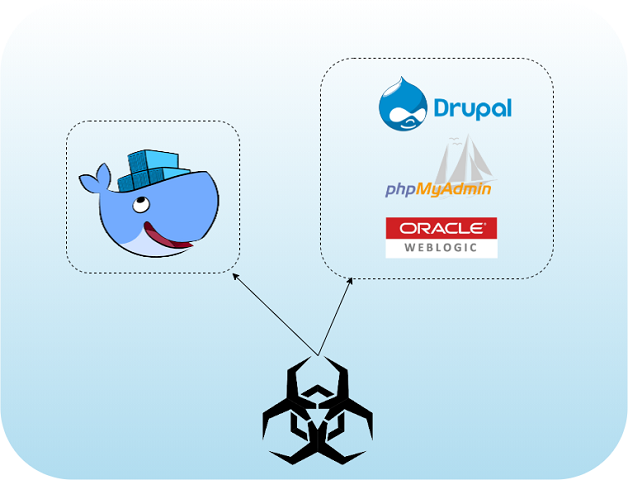
Exposed Docker API ports are a desirable entry vector for an attacker, not only because they are easy to identify, but also because they give the attacker full control over the server without having to perform too many actions. There are likely many potential victims out there, which is a motivating factor for attackers to scan for misconfigured ports, and why you should take the time to check your ports are not exposed. Our report also explains how you can open your ports safely when necessary, as there are ways you can do this without giving access to everyone.
Try the Intezer Protect Community Edition
Misconfigured Docker API ports to third-party vulnerabilities like SolarWinds have shown that attackers can enter your systems no matter how hard you work to reduce the attack surface. Protecting your cloud environments requires the ability to verify that all code running across your compute resources is trusted. Protect 10 runtime assets for free.
IoCs
UPX file
72b86cf168181480d745b27f57ef574c8d6208daf36c898eddd0700f41f8a03d
Muhstik
F5912e8444c502b3143cb331d556e24e519b9c9e84c4329396687805a324d744





