Product Tour
Take a spin through Intezer’s Forensic AI SOC to see how to automatically triage, investigate and respond to every alert at unmatched speed and accuracy.
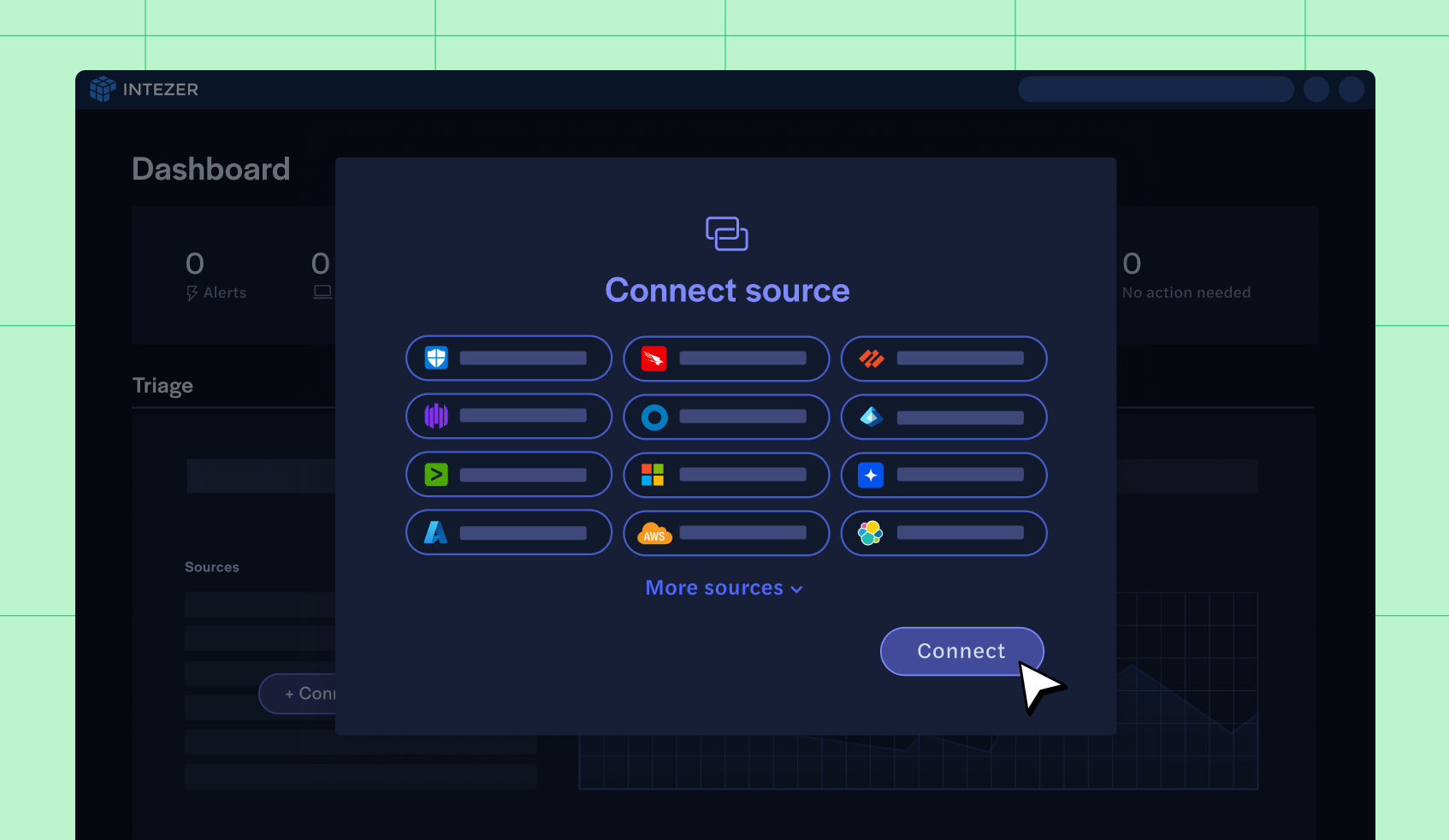
Intezer integrates with leading SOARs to empower your security team to automate tasks that would traditionally need complicated playbooks and human intervention.
Intezer Forensic AI SOC automates triage and response, resolving common threats and escalating only what matters, cutting investigation times from hours to minutes.
Analyzes alerts in real-time, correlating threat intelligence, malware origins, memory analysis, and forensic artifacts, pairing with your SOAR to significantly reduce workloads.
Integrates a comprehensive scanning toolkit into your SOAR to validate threats, triage false positives, and escalate only critical incidents with full investigative details.
Reduces mean time to resolution (MTTR) by auto-resolving low-risk alerts and providing deep forensic insights for escalated threats, cutting hours of investigation time for your analysts.
Connect your security products so you can triage and investigate all your alerts with Intezer Forensic AI SOC.





Intezer Forensic AI SOC investigates every alert in seconds, taking action through your SOAR before threats escalate.
Integrate with Palo Alto Cortex, Splunk SOAR, Tines, and more, enriching them with real-time threat intelligence.
Fully investigates every alert, gathering evidence such as process execution traces, memory snapshots, file artifacts, IPs, URLs, behavioral indicators, and more.
Detects attack techniques, lateral movement, and novel malware strains using genetic threat analysis and deep security event correlations.
Classifies threats by severity, eliminating false positives and escalating only legitimate risks for human review.
Triggers SOAR automations or provides in-depth, human-readable analysis for SOC analysts to take action.





Implementing Intezer Forensic AI SOC for SOAR playbooks yields tangible benefits:
Of Alerts Escalated
Minimizes false positives so SOC teams can focus on real threats.
Event Investigation Coverage
Every alert is deeply analyzed with memory forensics, threat intelligence, and AI-driven analysis.
Tuning or Manual Playbook Creation
Deploy in minutes with robust, pre-built integrations, providing instant value with complex configuration.