APTs are targeting Linux systems more than they ever have.
Linux Attacks are on the Rise
The research community continues to witness an increase in the number of active campaigns targeting Linux systems. This coincides with the increasing adoption of Linux, which has become the predominant operating system for IoT devices, web servers, and cloud servers.
Naturally, the discovery of new and sophisticated Linux malware that are different from traditional threats that reside in this ecosystem (namely DDoS botnets and cryptominers) is happening more frequently.
Attackers are adapting to the rapidly changing IT infrastructure of their targets by porting their existing Windows tools to Linux or developing new tools that support both platforms. More about this in a later section.
Below we look back on the previous decade of Linux APT attacks to get a better understanding of the trends that might shape the current decade.
Looking Back on the Last Decade of Linux APT Attacks
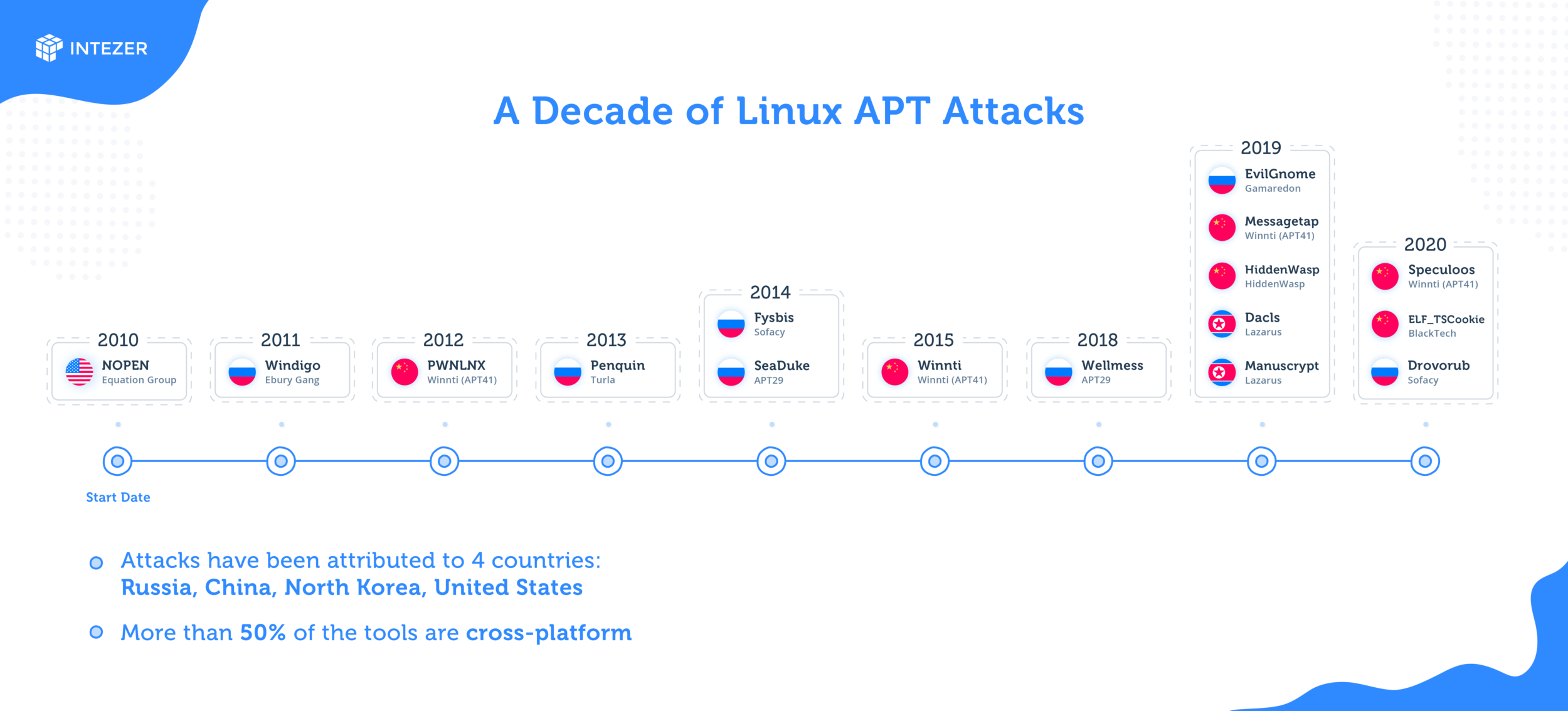
In the previous decade researchers discovered several large APT campaigns targeting Linux systems, as well as unique Linux malware tools tailored for espionage operations. Most of these campaigns and tools have been attributed to well known APTs, which to date continue to expand their arsenal with new tools to target Linux, as well as make updates following detected incidents.
More recently there has been a noticeable increase of such discoveries. In addition to the many espionage tools that were recently uncovered (HiddenWasp, Dacls, and MessageTap to name some), older tools such as Penquin Turla have reemerged in new versions. In another high profile example, BlackBerry recently uncovered a decade-long campaign attributed to the Winniti Group (China), where the attackers utilized multiple cross-platform RATs to target Linux, Windows, and Android platforms.
Most of the Linux APT attacks that were documented in the past decade have been attributed to 4 countries in particular: China, Russia, North Korea, and the United States.
The illustration below depicts the major APT campaigns involving Linux tools that have been reported since 2010. The year refers to the estimated start date of the campaign or the first known use of the malware. Most of these campaigns should be considered active, since new incidents are still being reported since their initial discovery, often with upgraded versions of these tools.
Does your Malware Support Linux?
The majority of malware used in these attacks were either multiplatform or ported to Linux directly from a Windows malware. Adapting existing Windows tools is likely faster and more cost effective for attackers than writing them from scratch.
This is starting to hold true for the Linux threat landscape altogether, as it’s becoming more common to see Linux malware which share code with their Windows counterparts. One explanation for this is attackers are starting to embrace Golang as their programming language of choice to develop cross-platform malware and target both Windows and Linux systems.
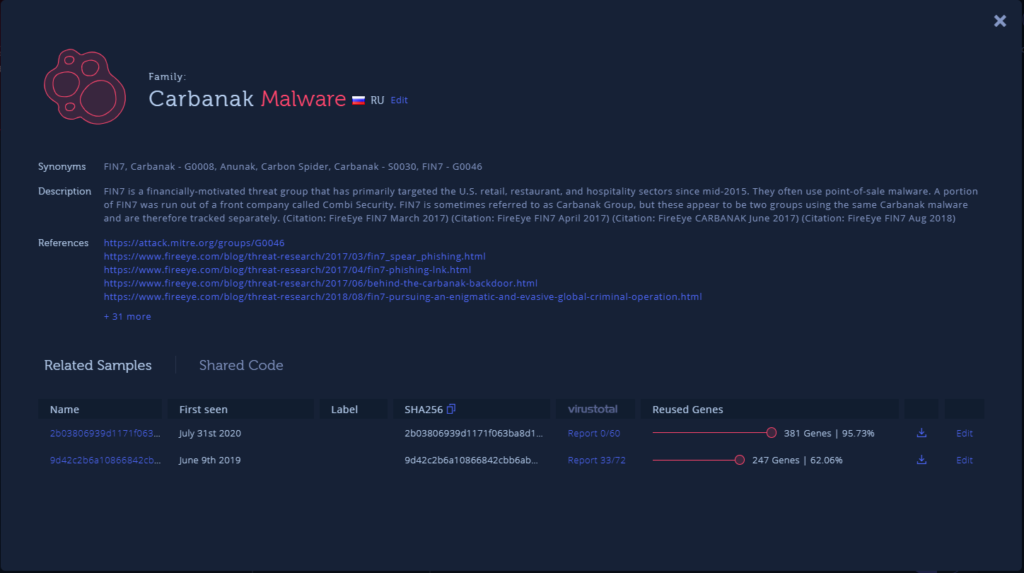
Carbanak, one of the largest cybercrime groups ever reported, is one example of an adversary shifting its tools from Windows to Linux environments. Here is a new Linux sample, written in Golang, which at the time of its discovery was fully undetected by all engines in VirusTotal. With the help of the cross-platform code reuse feature for Golang in Intezer Analyze, we were able to identify that this file shares code with a Carbanak Windows sample from 2019.
Another group that is moving to Linux by embracing Golang is APT29, a Russian hacker group that was accused by western agencies earlier this Summer of stealing COVID-19 vaccine research. Intezer Analyze was also able to identify this previously undetected APT29 WellMail Linux variant because it shares code with the IOC of WellMail that appeared in the National Cyber Security Centre’s July 2020 report.
Conclusion
Linux APT attacks are becoming more frequent. Some of the most prominent nation-state actors are incorporating offensive Linux capabilities into their arsenal and it’s expected that both the number and sophistication of such attacks will increase over time.
Detecting these attacks is going to continue to take a concerted effort. Code reuse is a good start given its proven ability to classify many previously undetected Linux threats.
IT security personnel should focus on increasing visibility of Linux systems, while keeping in mind that if you want to detect Linux threats, you will need a security solution designed to protect Linux, not a migration or adaptation of a Windows endpoint detection platform.
As a starting point, we encourage you to access our weekly threat feed containing the latest low-detected Linux threat hashes. Add these hashes to your blocklist to protect your systems and use this intel to prepare your organization for future incidents.
Our free community edition defends your Linux cloud servers and containers in runtime against the latest threats. Learn more