Adversaries are highly motivated, constantly expanding and improving their tools and techniques. On the other side of the fight, security teams are facing a severe resource shortage. There are more open positions than people to staff, and on top of that, it is difficult to find talent with the required skills.
Although there are many signals for improving detection and scaling the efficiency of triage, security teams are overwhelmed with data, causing a bottleneck on the opportunity to scale the decision-making process. This leads to low performance reflected in measurements such as MTTD (Mean Time To Detect) and MTTR (Mean Time To Respond).
Here at Intezer, we have a goal to tackle this challenge by providing solutions for SOC and incident response teams’ pain points. In this post we will explain the need for scaling up detection and the solutions available with the new Detect & Hunt feature in our enterprise edition of Intezer.
What is Detection Engineering?
As time goes by, cyber attacks are rising, the attack surface is growing, and security teams’ difficulties are becoming even more painful. From this challenge, the detection engineering approach has arisen.
Detection engineering is a discipline that stands for constantly evolving and staying relevant by embracing an automation-first mindset. Bottom line – be in control.
A great example of this concept can be found in this meme created by Florian Roth. The meme emphasizes the old-school-traditional-manual mindset, versus progressive automation-first mindset.
Another great example by Florian Roth for the detection engineering concept is this Tweet below. In the Tweet, he explains how to break down a malware sample into different layers of detection opportunities rather than just looking into given IOCs (hashes and C2s) at the bottom of the report.

Want To Learn More About Detection Engineering?
Check out “The Future is Now: Embracing Detection Engineering for Incident Response“ on YouTube, a recorded webinar we did together with SANS’ Jake Williams.
Pyramid of Pain: Hash out the Hash
Hash values and basic network artifacts are not enough for creating quality rules. They are short lived and can be easily manipulated. With that being said, security teams still base their detection and hunting rules on these artifacts as they are easy to get and to implement.
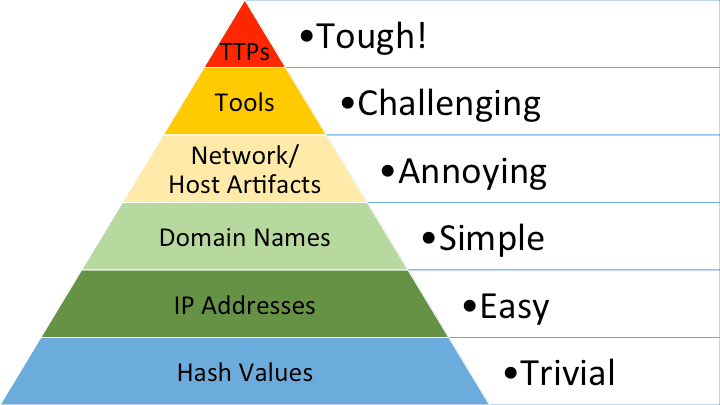
It is needless to say that detecting and hunting for just file hashes is not enough. Intezer’s goal with our new Detect & Hunt feature is to help you and your team create better rules, fast.
Intezer’s Detect & Hunt: Creating Effective Detection Rules
Creating detection and hunting rules are an essential part of cybersecurity teams’ responsibilities.
Many times, the rules creation process will include the use of sandbox behavioral reports. These reports are often overwhelming, containing a large amount of non-relevant data, causing a situation where analysts have to “fish” relevant artifacts to create effective rules. Not a simple task for entry-level analysts.
A good rule should also not be too wide in order to avoid high false positives rate, but not be too narrow to avoid miss detections.
Intezer’s new Detect & Hunt feature combines our unique classification abilities with sandboxing, to present high-quality detection content. By matching the malware behavior against a huge database of malware and benign software behavior, we filter out non-relevant artifacts and present those that are unique to the studied sample or that have been previously seen in other malware samples. This allows analysts to quickly create effective rules, with high accuracy and low false-positive rate.
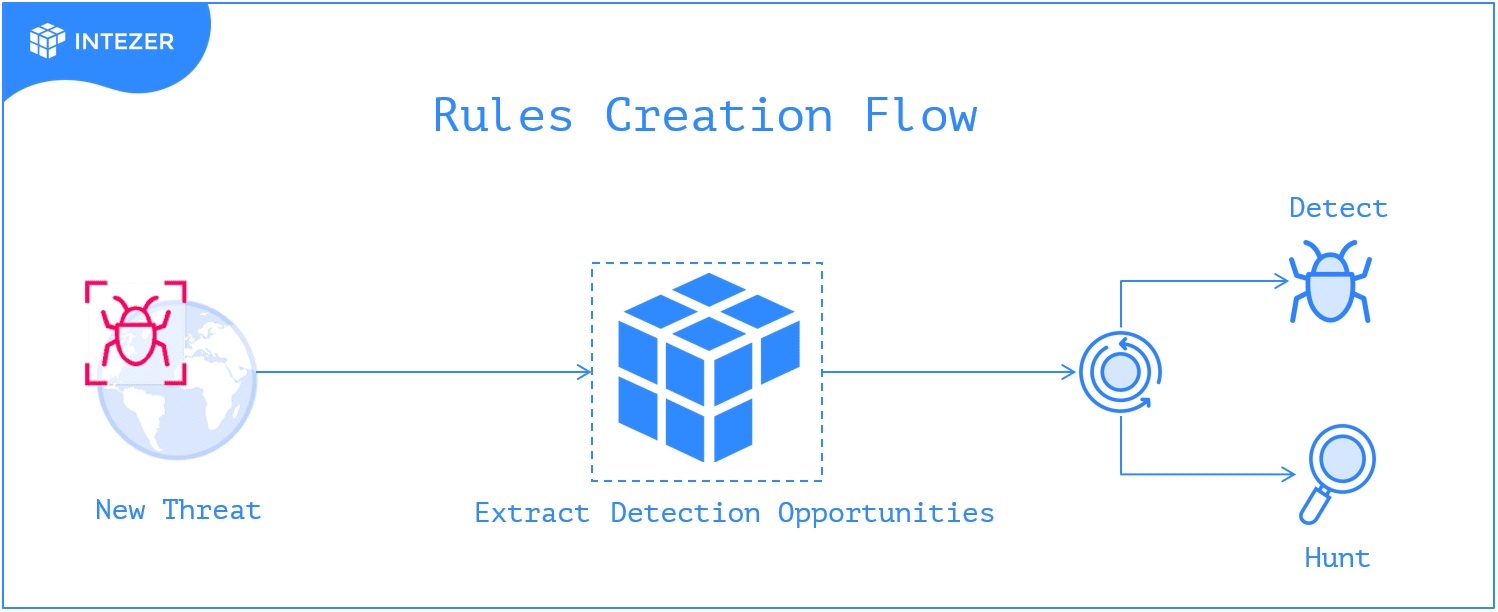
Real-Life Example: Extracting Detection Opportunities
Let’s take a look at the analysis of the recently reported SysJoker malware.
The Detect & Hunt feature is divided into two tabs:
- Activity-based
- File-based
Activity-based tab
The activity-based artifacts are extracted after executing the sample in our sandbox. These can be divided into categories:
- Process tree
- File activity
- Registry activity
- Network activity
The screenshot below shows the activity-based artifacts tab:
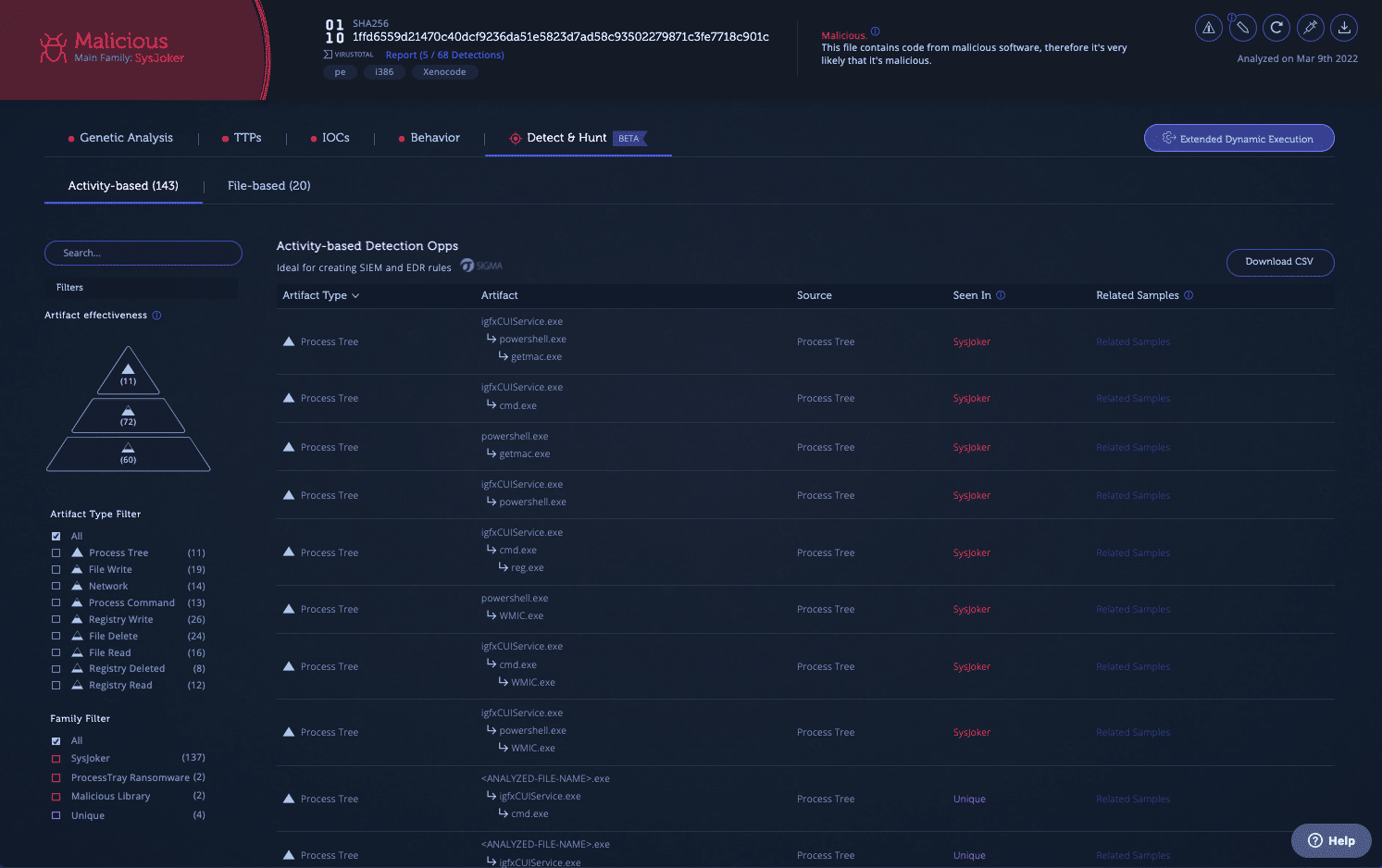
On the left side of the page we can see filters. Artifacts can be filtered via:
- Artifact Effectiveness Filter: This is a simplified visual inspired by David Bianco’s Pyramid of Pain, which we showed above. Effectiveness level is per artifact type. It is determined by the expected potential of detection accuracy and the average lifespan the artifact type has.
- Artifact Type Filter: This lets you filter by what kind of artifact it is, such as showing only file write, process tree, or network artifacts.
- Family Filter: This allows you to select artifacts associated with specific malware families, or identify unique artifacts that haven’t been seen in a known malware family before.
From here, you’ll have what you need to create rules, to be implemented within your EDR or SIEM. We have another post here that dives into how to write Sigma rules for your detection opportunities.
File based tab
This tab helps you to create YARA rules for hunting samples in the wild or within your organization. There are three artifacts:
- Main file
- Memory module
- Dropped file
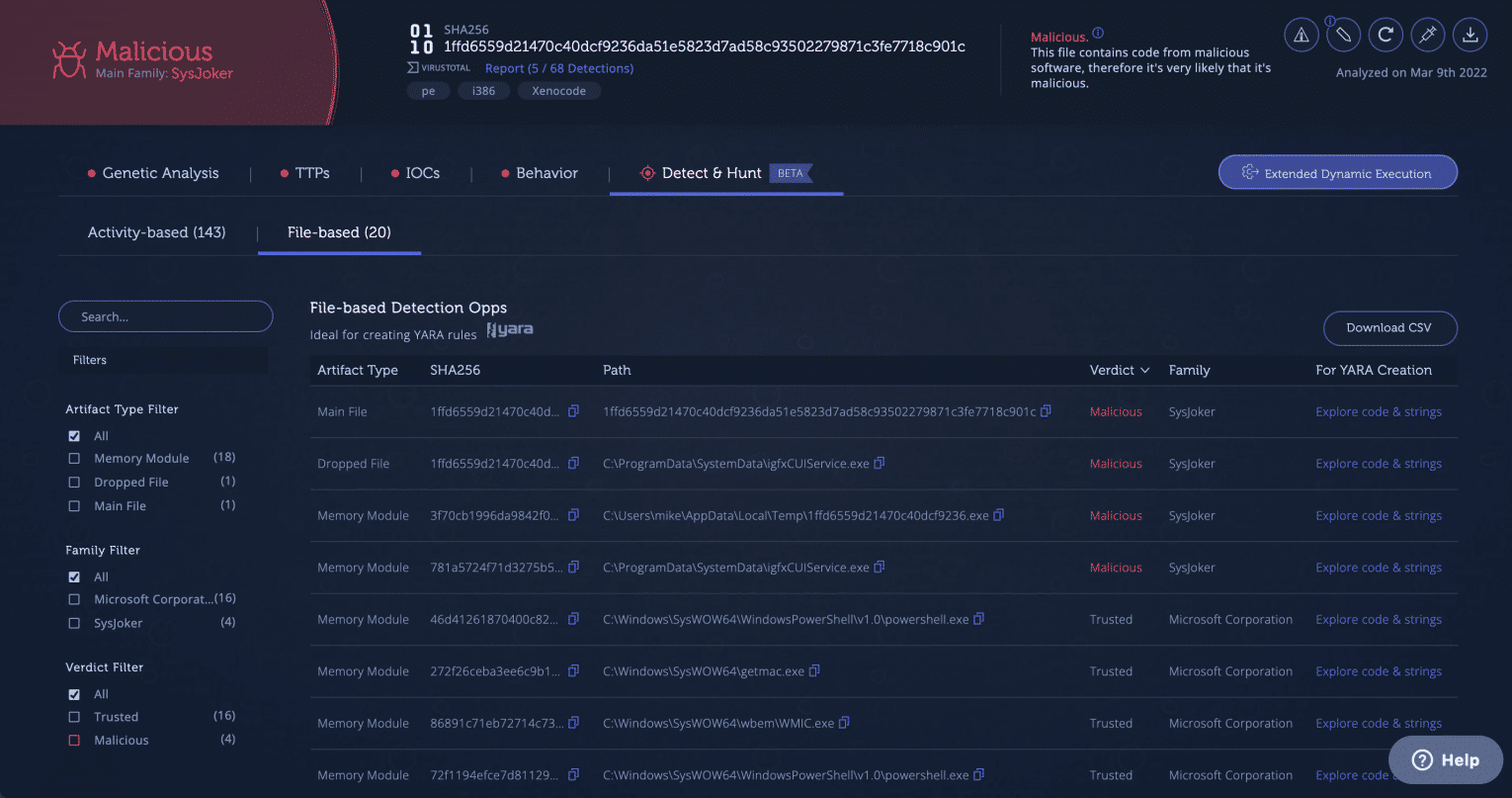
On the left side of this screen, you can see the filters. In this case, there are three different filters:
- Artifact type
- Family name
- Verdict
This screen provides two main actions. The first is a direct link to the relevant strings of the artifact. Clicking on the strings link will take you to the strings view of the artifact, to help you create YARA rules without wasting time on searching for strings that are unique for the sample.

The second action is “generate vaccine.” This feature allows you to generate:
- Code-based YARA
- STIX format of the hash
- OpenIOC format of the hash
What will you need
You need to collect relevant logs from endpoints within your organization to be able to run rules against them using your EDR or SIEM.
Accelerate Incident Response with Automation-First Mindset
Our Detect & Hunt feature has a full API, allowing you to automate detection opportunities to save incident response time. This can be done by:
- Integrating Intezer within your TIP processes or any other threat intelligence feed to go beyond the hash and enrich extracted detection opportunities.
- Integrating Intezer with your EDR (see Intezer EDR Connect) and automatically getting detection opportunities for alerts.
What’s next in our pipe?
The Detect & Hunt feature is in beta and we are continuously working on improving our data. We also have many more exciting additions planned as upcoming milestones, including:
- Extracting all detection content per malware family / APT group
- Track a specific threat to stay on top of latest detection opportunities
- Pivoting from artifact to related samples
- Adding TTPs as artifacts
Detect & Hunt is available now for Intezer’s enterprise customers. Reach us to book a demo or try it yourself with our 14-day online trial (to create a trial account you should first create a free community account and then register for the online trial).






