Emotet, Trickbot, and Lazarus were the most common threats detected by the community in 2019. Linux threats, with code connections to Mirai, were also a recurring theme.
The Intezer Analyze community became a go-to source for detecting, classifying, and responding to cyber threats in 2019. Regardless of platform or architecture, binary code reuse is prevalent in every malware family. As long as you have the malware’s code indexed, you will be able to detect any variant or new threat which uses even tiny portions of the same code. I will demonstrate this fact on the most popular malware families our users encountered in 2019.
Emotet
Emotet has become one of the most prolific banking trojans, designed to steal valuable information from its victims. The threat is usually spread via malspam campaigns, including malicious attachments which drop the malware onto an infected machine.
Emotet is a polymorphic malware, which means it’s constantly changing its evasion techniques to avoid detection. Emotet also has the ability to download additional malware onto a victim’s machine after infection. This was seen in a recent attack against a local government in Florida. After an employee inadvertently downloaded Emotet onto the city’s network, the malware downloaded Trickbot, which led to the deployment of the Ryuk ransomware. The city paid $460,000 in ransom.
While Emotet has many variants utilizing different C2 servers and evasion techniques, code reuse is extremely prevalent among Emotet samples. This is evidenced by the following cluster graph, which maps code connections between all of the Emotet samples detected by our community in 2019. Side note, you can create this graph using our API. More info here!
This result is significant in that we can see at least four to five different clusters of Emotet, some that share code with other clusters and one that shares code only with samples in its own cluster. Despite efforts by Emotet to evade detection, Genetic Malware Analysis is effectively able to detect this malware by identifying code similarities, regardless of variants that form as new evasion techniques are used.
Trickbot
Trickbot is another banking trojan, which I’ve previously written about in our Halloween edition. It’s not surprising that Emotet and Trickbot were the most common malware families detected by the community last year, because as we saw in the previous example, these malware typically work in tandem. The initial infection begins with Emotet, followed by malware such as Trickbot or Ryuk.
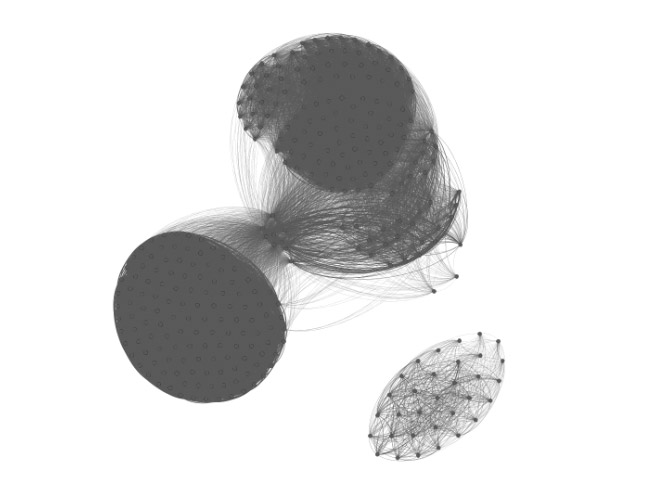
Trickbot is known for its modularity, adding new capabilities such as credential harvesting through server side injection, worm-like network propagation, and network reconnaissance. While many expect this malware family to be drastically different from variant to variant, the graph below reveals the Trickbot samples are quite similar if you are analyzing them based on code reuse. This makes it much easier to detect and classify these threats.
Lazarus
Lazarus is a nation-state sponsored threat actor with ties to North Korea. As opposed to Emotet and Trickbot, Lazarus is not a specific malicious tool. Rather, it’s a group possessing an arsenal of different malware.
The Lazarus group has been involved in many attacks since 2009, including DDoS, ransomware, and cyber espionage targeting countries globally. Notable attacks attributed to Lazarus include the Sony breach (2014), Operation Blockbuster (2016), and the WannaCry ransomware attack (2017).
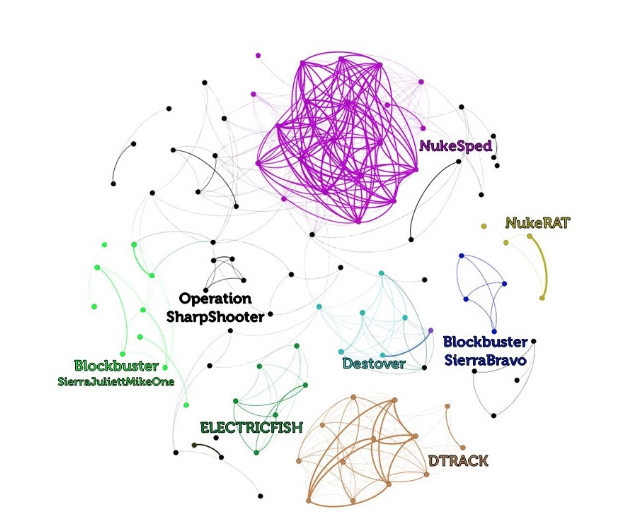
In the below graph, I have included all 2019 malware samples from the Intezer Analyze community which share code with Lazarus. Since Lazarus is a group which has used many tools in various operations over time, you can see clusters of those tools, rather than several main clusters of the malware family:
For more information about North Korean threats and their code connections, check out our joint research with McAfee.
Linux Malware
The aforementioned threats are typically seen on the Windows platform, but that doesn’t mean the community didn’t detect threats on other platforms. In fact, 2019 was the year of Linux threats, evidenced by over 20 of our research publications related to Linux-based threats. Genetic Malware Analysis was the first to detect Linux threats such as crypto-mining campaigns, botnets, ransomware, and nation-state sponsored threats, largely due to the continued reuse of code between threat actors on this platform.
Being an open source platform, the malware targeting Linux users are often open-sourced themselves. The best example of this is Mirai. Mirai is by far the most common threat we have seen in the Linux threat ecosystem, likely since its source code became publicly available in 2016. Since its release, Mirai has evolved into countless other variants, but its core remains mostly the same. The following graph contains all Linux malware detected by the community last year, and Mirai’s dominance is quite clear:
Here we can see two main clusters of Mirai: one is native ELF and the other is in the ARM architecture. We can also observe genetic connections between Mirai and Gafgyt (see the green color located in the bottom Mirai cluster). Gafgyt is a common Mirai variant.
Start the new year off with an advanced tool for detecting and classifying malware such as Emotet, Trickbot, and Lazarus. Sign up for the free Intezer Analyze community edition at analyze.intezer.com and get results within seconds.