1) Pirpi (APT3) [Link to Analysis]
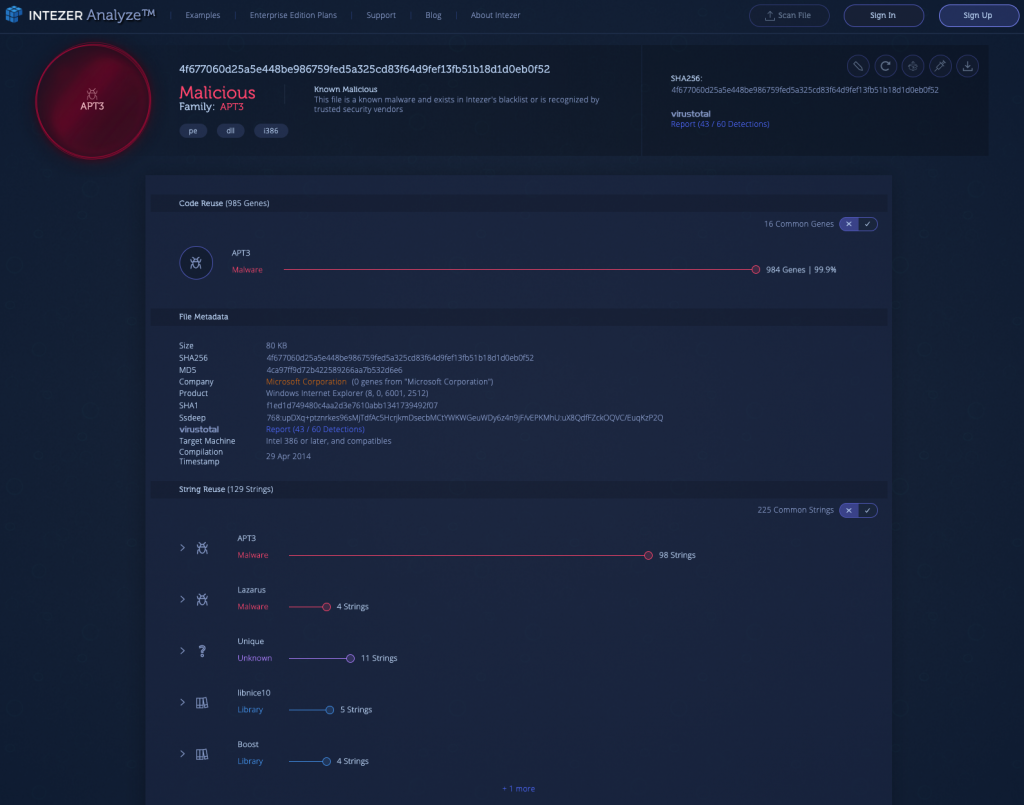
APT3, commonly referred to as Gothic Panda, TG-0110 and Buckeye, is a Chinese cyber espionage group linked to the Chinese Ministry of State Security (MSS). At its inception, the group targeted government organizations in the United States but since March 2016 it has targeted primarily Hong Kong government agencies.
This is a sample of Pirpi, a backdoor which is used to steal information from infected organizations. The malware has the ability to connect to a remote server and then receives commands through encrypted GIF files. The backdoor will provide information about the infected endpoint and actively execute various commands to exfiltrate information. It will also download or upload files, such as additional malicious tools, to the endpoint. As can be seen in the analysis below, the sample shares 99.9% of its code with previous instances of APT3.
2) ChinaZ [Link to Analysis]
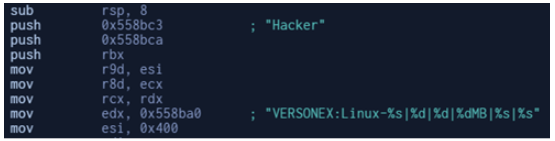
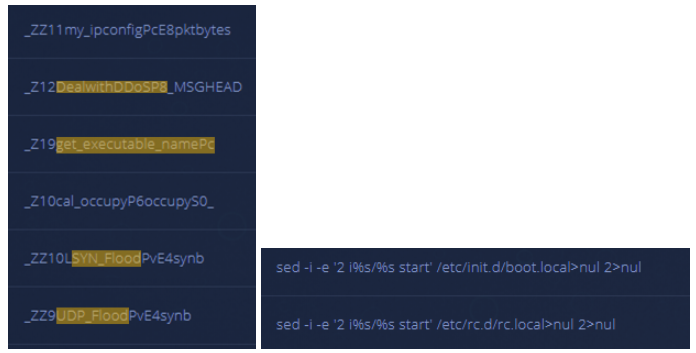
ChinaZ is a Chinese threat actor group notorious for targeting Windows and Linux systems with DDoS botnets since November 2014. In January 2019, Intezer researchers published an in-depth analysis of the group and its code connections to other threat actors in the Chinese DDoS threat landscape.
In this particular community upload, we have observed indicative strings which poses the question, “how is this campaign so successful at avoiding detection while utilizing relatively simple tools in order to take control of infected machines and create botnets?”. As you can see in the following screenshots, ChinaZ does not employ evasion techniques.
This is not a sophisticated malware. In reality, many linux malware go undetected because there is less emphasis placed on detecting these threats in the current information security landscape. While linux threats are typically not detected by classic methods, leveraging code similarity analysis (or, “Genetic Malware Analysis”) can enable defenders to quickly and easily track them down.
3) Ursnif [Link to Analysis]
Ursnif, also known as Gozi, is a trojan which will perform web injections and steal credentials and banking information from infected users.
Since its resurgence in 2013, Ursnif continues to become more sophisticated in its infection and evasion techniques. In a blog post published by Cisco Talos in January 2019, the researchers found that the malware was able to infect an endpoint and achieve persistence without leaving any trace on the disk. This is significant because the majority of security solutions focus mainly on the file system, while largely ignoring in-memory threats.
It is not a coincidence that we see many code connections to other banking trojans in the analysis below. Code reuse between threat actors can be a result of source code being leaked or collaboration between the threat actors. This is what makes Genetic Malware Analysis so important. Continuing to identify code similarities between malware and the adversaries who employ them will enable defenders to detect a greater number of future variants of these threats.
4) ChChes (APT10) [Link to Analysis]
ChChes is a trojan used by APT10, also known as the menuPass Group or Stone Panda. APT10 is a Chinese threat actor group which has targeted a broad range of industries and government agencies in Europe, Japan and the United States, since approximately 2009.
ChChes is one of the trojans used by this campaign but as opposed to trojans like PlugX and Poison Ivy, the tool appears to be unique to APT10.
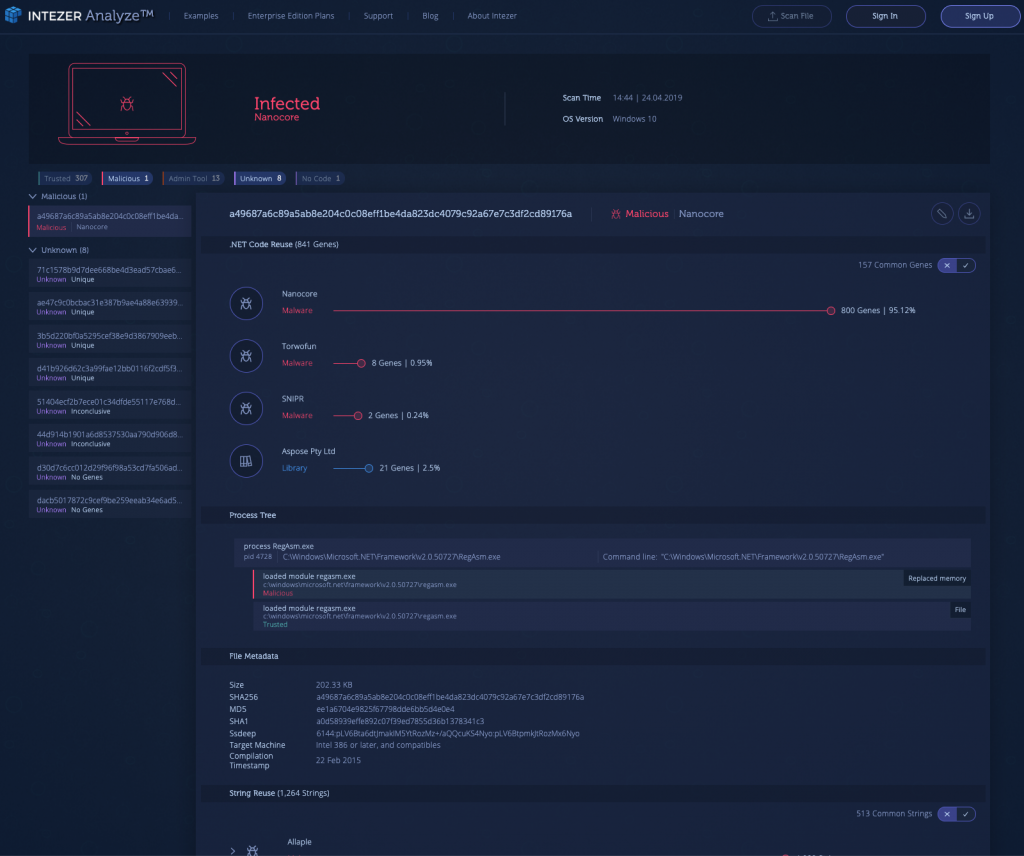
5) Endpoint Infected with Nanocore [Link to Analysis]
Nanocore is widely considered to be one of the more sophisticated remote access trojans (RATs) in the wild and the analysis below can attest to that. When Nanocore was first released in 2013, it was up for sale for twenty US dollars a piece, with options to upgrade the RAT with additional functionalities including ransomware capabilities, full surveillance and using the infected computer as a bot for DDoS attacks.
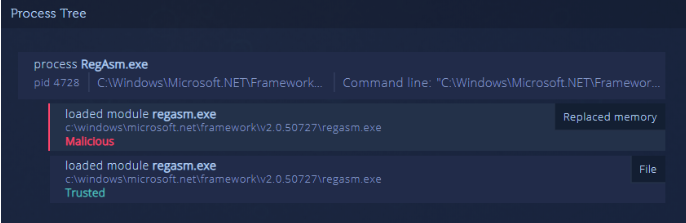
The analysis below shows the evasive nature of Nanocore, using process hollowing to hijack a legitimate process.
In the process tree section, we can observe the legitimate RegAsm.exe process, including its path as a trusted file, while a replaced memory module is detected as malicious. This technique means that we would not be able to trace this process back to Nanocore unless we specifically analyze its code in memory, which is done automatically with Intezer Analyze’s endpoint analysis feature.