Malware threats come in many forms. You can now analyze more of them with Intezer Analyze
We have made a major expansion to the types of files that can be analyzed in Intezer Analyze. In addition to our multi-platform support for executable files, you can now investigate and classify non-executable files such as Microsoft Office documents, PDF files, and scripts such as PowerShell and VBS.
The ability to quickly and effectively analyze these files can be valuable for several reasons:
- Very common: These are the file formats most commonly used as malicious email attachments during email phishing attacks.
- Valuable for analysis: These “dropper” files initiate the infection chain, serving as an optimal starting point for an investigation.
- Practical: In many cases, these files can be the only artifact available for analysis. While attackers tend to hide or even remove their traces from infected machines, the malicious attachment file can often be easily obtained for analysis from the email itself.
Analyzing these files can also be complicated. Existing malware analysis tools provide vague results and require deep technical skills to get the most out of them. With Intezer Analyze you can easily understand the type of threat and malware family you are dealing with, and get full genetic and behavioral context for when the investigation requires you to take a deeper dive.
Catching Infections Where They Start
Malware attacks usually occur in stages. They are often composed of several, separate components working together through the various infection stages, forming what is referred to as the “infection chain.” Due to the nature of some of the most popular malware delivery mechanisms today, such as phishing emails, the initial component of a typical malware infection chain is usually a document file (Microsoft Word, Excel, PDF) with an embedded (macro) script or exploit.
Another scenario that is becoming more common in today’s malware threat landscape is the use of script languages such as PowerShell and VBS for malware components further along the infection chain. A good example is this ransomware payload written fully in PowerShell.
Intezer’s Approach
In order to properly analyze these file formats, we have developed and integrated a new detection engine that analyzes the file’s behavior and complements our existing genetic analysis capabilities. As part of this engine we utilize the open-source CAPE sandbox for our new dynamic execution module. We are excited to use this awesome project and contribute with any valuable improvements we make.
Examining what the file does when executed while also analyzing every piece of binary code loaded to memory or disk, you can better detect and classify any malware threat, particularly malicious documents and scripts. These insights also give users more context about the file through the new TTPs screen.
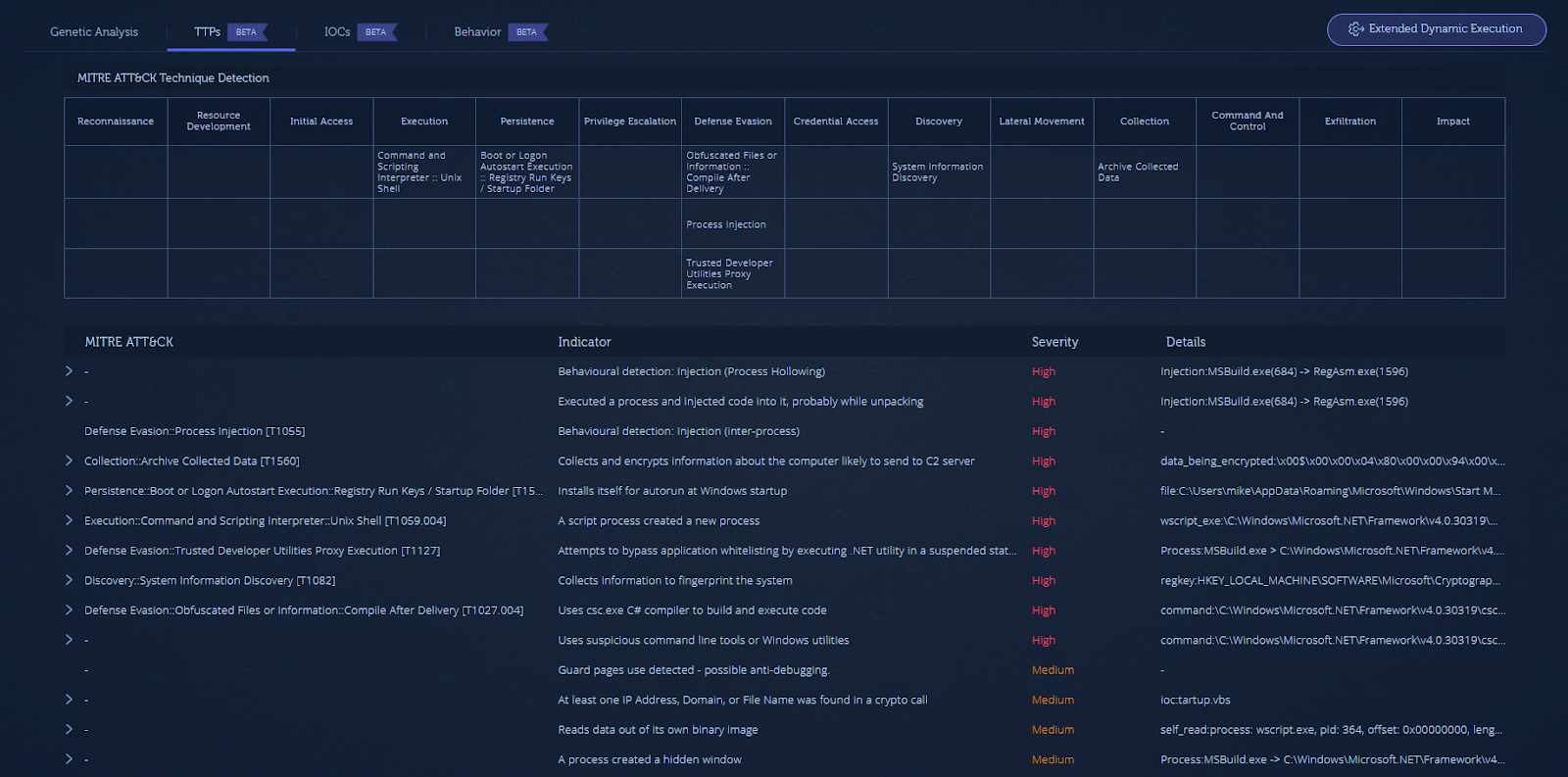
The TTPs screen highlights all of the characteristics and capabilities (indicators) observed about a file, organized in a MITRE ATT&CK-style table format. This allows you to see how the malware behaves and what it is capable of in order to quickly assess risk.
See it in Action
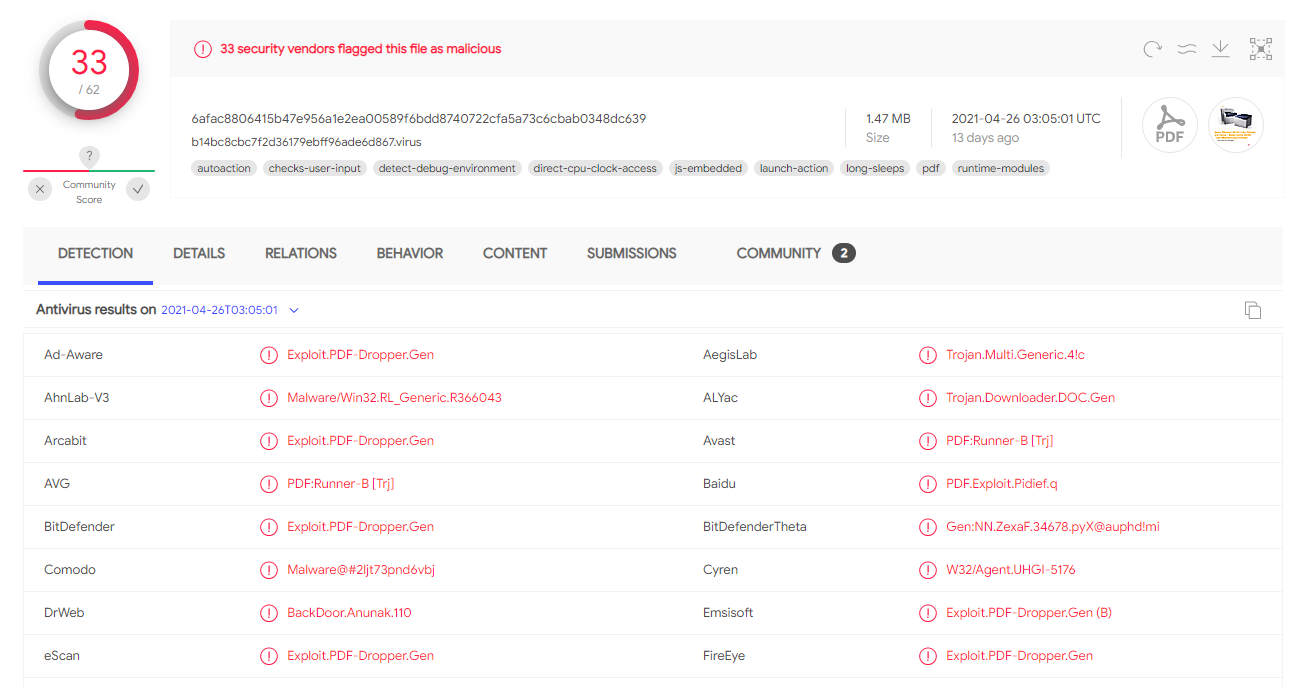
To demonstrate the value of using Intezer Analyze for malicious documents let’s take a look at the genetic analysis of this PDF file. The five-year old file, hosted on VirusTotal, is a malicious dropper, yet the results on VirusTotal do not exactly provide a clear indication of what malicious executable is dropped.
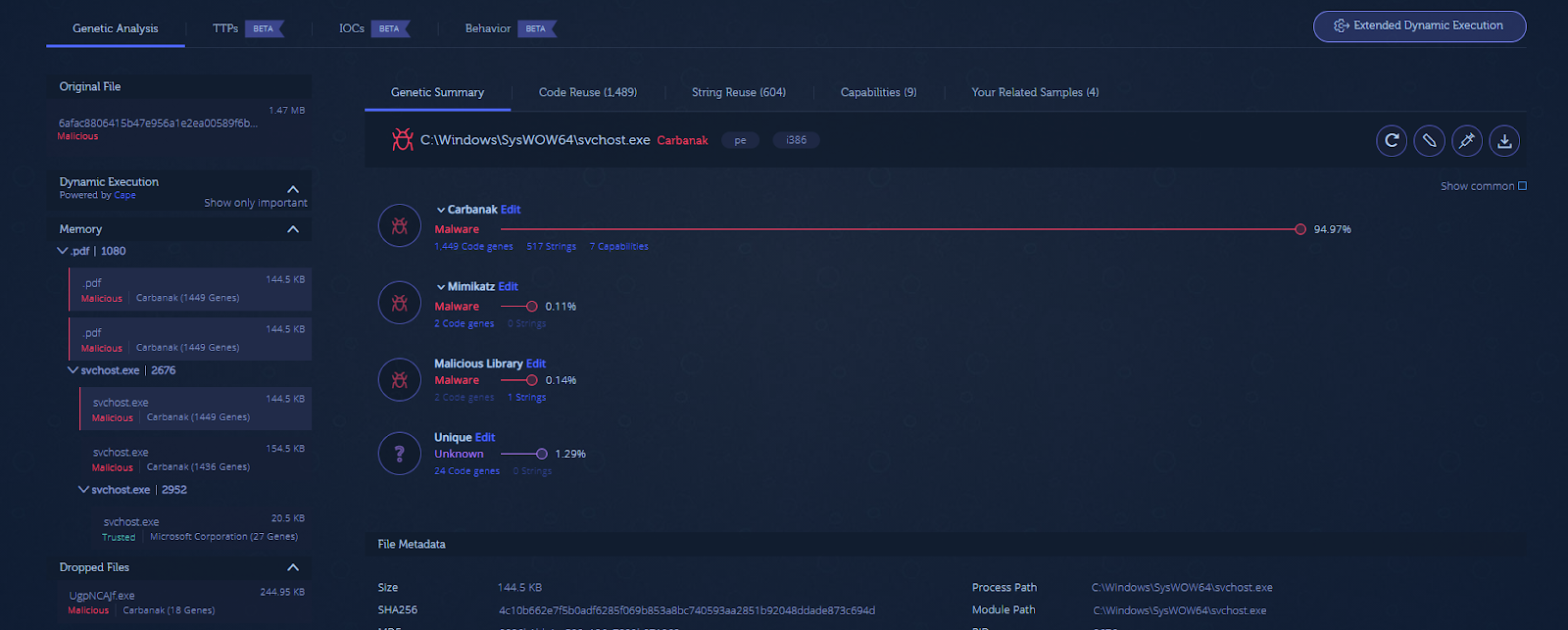
Analyzing the file with Intezer Analyze immediately reveals that this file is related to the Carbanak cybercrime group.
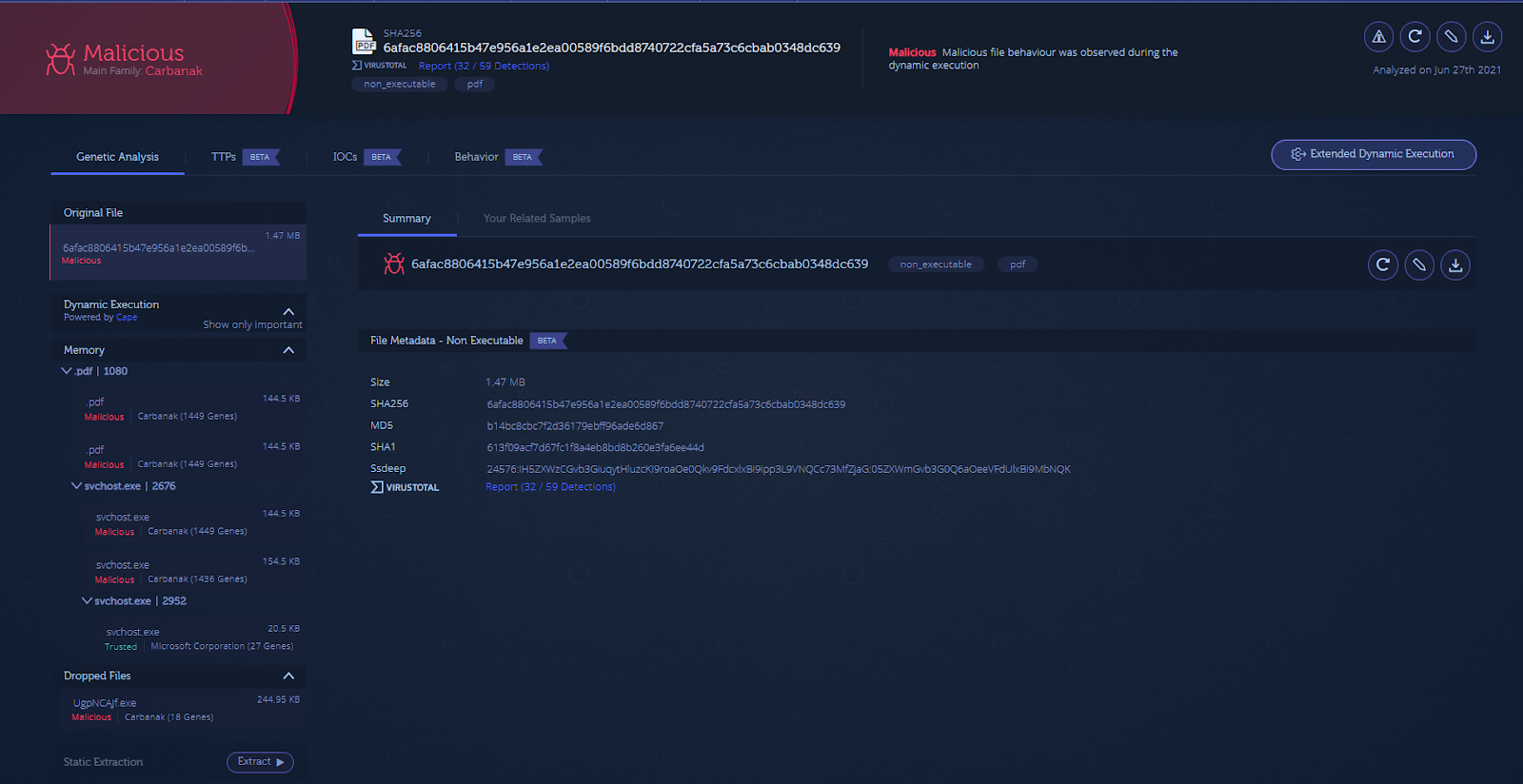
The Dynamic Execution tree on the left-hand side of the report shows the malicious payloads used further down the infection chain. Under the ‘Dropped Files’ subsection, you will see a small binary payload (with 18 code genes) written to disk.

Looking at the ‘Memory’ subsection, which shows code extracted from memory, there are several copies of the main malware payload (containing more than 1,400 code genes).
The TTPs section also discloses the techniques that this malware uses.
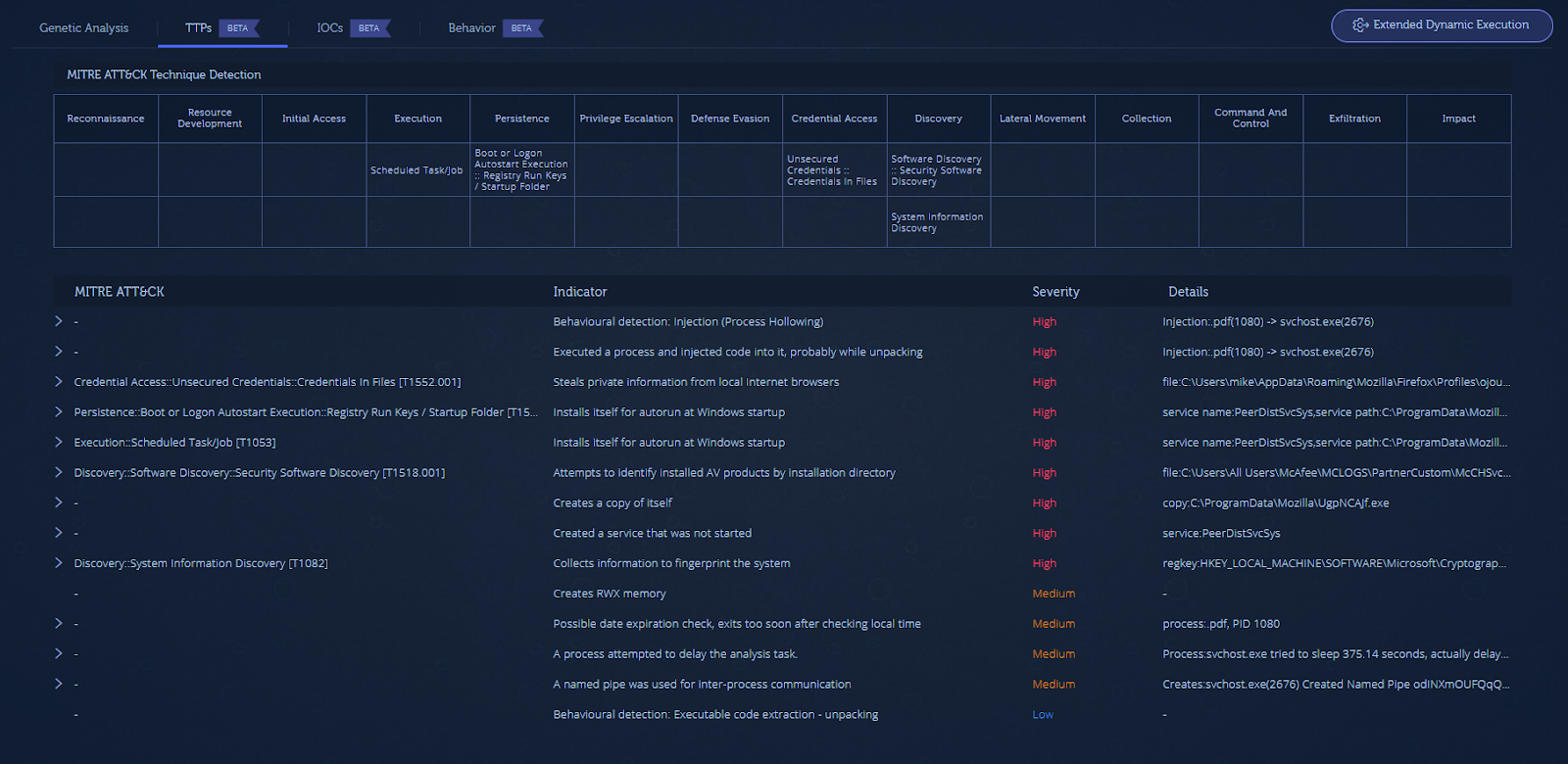
The malware uses a persistence mechanism by installing itself to autorun, performs software discovery on security products as an evasion attempt, and leverages the process hollowing technique in order to inject its payload into memory.
Part of the Plan
These new capabilities are yet another step towards our mission to help users easily investigate any malware incident. Intezer Analyze now covers analysis of binary files, documents and scripts, endpoints and memory dumps. Stay tuned for more updates coming soon.
Try it Yourself
Start analyzing suspicious files and endpoints today with the Intezer Analyze free version or check out our pricing plans.