Just after the publication of this post the US-CERT released an alert about Emotet.
Evolution is the result of adaptations that take place over generations, where only the strongest survive. In the case of malware, where the strongest evade detection.
Emotet, the popular banking trojan spread primarily through spam email campaigns, is constantly evolving and polymorphic, meaning it exists in different forms. Polymorphic also means the malware frequently changes its identifiable characteristics, such as strings and API imports to become unrecognizable to many detection techniques. This has seemingly worked well for Emotet. Despite being operative since 2014, new adaptations or variants of the malware continue to evade most signature-based detections.
Emotet stripped down to its genetic core, however, reveals its code remains largely the same from generation to generation. When you analyze code as a DNA equivalent, detecting code reuse and similarities can effectively trace a variant back to its original malware family.
In the News
Cybersecurity agencies from France, Japan, and New Zealand have reported spikes in Emotet attacks since the start of September. In France the malware succeeded infecting computers on the network of the Paris court system.
At Intezer we are also seeing this increase in Emotet activity reflected in Intezer Analyze. 40 percent of the samples analyzed last month by both our enterprise customers and community users were classified as Emotet. In August, our researchers tweeted about a few sparsely detected Emotet samples.
August 11, 2020
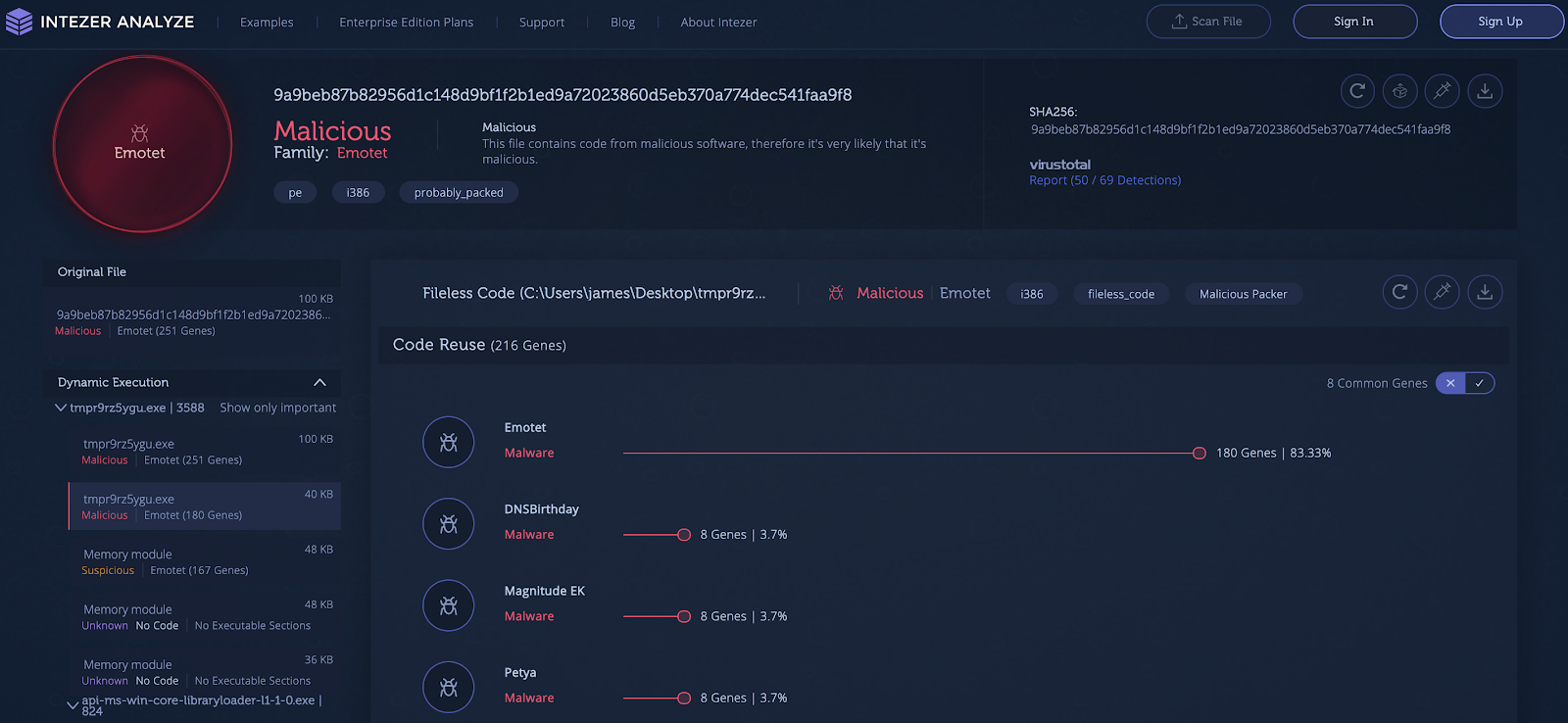
New Emotet sample uploaded from Canada and the United States was originally detected by 4 out of 70 engines in VirusTotal. After unpacking the sample contains a fileless payload that shares code with previous Emotet payloads.
August 23, 2020
Another new Emotet sample, uploaded from Japan and Canada, also originally with just 4 detections in VirusTotal. The file is packed and shares code with previous Emotet versions.
Emotet remains one of the most frequent threats classified by the Intezer Analyze community, along with Trickbot, another banking trojan. These malware often work in tandem, where the initial infection begins with Emotet, followed by further malware downloaded onto the endpoint such as Trickbot and Ryuk ransomware.
Emotet Up To Its Old Tricks
A spike in Emotet activity is not out of the ordinary. The malware was first identified in 2014 as a relatively simple banking trojan with the aim of stealing financial data. Over time it has evolved into a modular malware, operating in a Malware-as-a-Service model and taking advantage of its vast infrastructure to deliver additional malware payloads. This article sums up the evolution of Emotet over the years.
Emotet is a polymorphic malware. Polymorphic is defined as “occurring in several different forms, in particular with reference to species or genetic variation.” Applied to the world of malware development, Emotet’s main stealthiness comes from the heavy use of different packers that hide everything including all code for every sample, to avoid detection. In the analyses above, Intezer Analyze unpacked these payloads automatically and quickly detected code reuse between the payloads and previous Emotet payloads.
Our Michael Kajiloti documented some of the tricks Emotet employs to evade detection, namely fileless and malformed headers, in this Fantastic Beasts-themed article.
Detect Emotet Payloads Post Infection
I suspect that my machine is infected with Emotet.
If you or someone you know has opened a suspicious attachment, we recommend using our free endpoint scanner tool to check for a possible infection by Emotet in memory. The scanner will analyze all memory modules to identify Emotet payloads as well as any other payloads the malware may have downloaded.
For similar reading, check out this article, Detect malware associated with the most exploited CVEs.
As an alternative approach, due to the fact that Emotet resides in memory, you can also search for a YARA signature across the network. For that, you will need a relevant YARA rule that detects Emotet payloads, as well as a YARA memory scanner.
We recommend checking out Loki, an open-source YARA scanner from Florian Roth (Florian’s Twitter handle is @cyb3rops), that can scan endpoints across your network. For YARA rules to detect Emotet, you can use this one which is part of the CAPE project.
Keep in mind that signature-based detection such as YARA may sometimes result in false positives, especially in memory, so it’s always a good practice to reconfirm.
This white paper explains why code-based YARA signatures are often stronger than signature-based strings which can be easily manipulated by the attacker. Intezer Analyze enterprise users can automatically produce code-based YARA signatures for any classified threat by clicking on the vaccine icon in the upper right corner of the analysis.
Conclusion
Emotet and other banking trojans can be a huge pain for enterprise organizations and end users alike. Usually, these types of malware are highly evasive and polymorphic, which poses a challenge for many security solutions to protect against them. We continue to observe a large number of Emotet samples uploaded to Intezer Analyze daily. Time and time again code reuse detection has proven to be an effective way to identify these threats.
In a world where everything is seemingly unpredictable, it does seem we can count on Emotet to keep us on our toes. That shouldn’t stop us from being more strategic in how we adapt our approach to make it easier to identify this threat.
Intezer Analyze provides clear classification beyond just Trojan.Generic. Use the free community edition to get clear classification for threats like Emotet and other banking trojans in seconds.