Detecting Reused Ransomware
Whether we’re dealing with a criminal threat actor looking to steal money from their victims using ransomware or malware sponsored by a nation state, we can consistently see the reuse of code. In this specific case, we have observed a variant of a well-known ransomware, via a new version of Hermes from what may have originated from a nation state threat actor.
According to reports by researchers at McAfee and BAE Systems, a ransomware named Hermes was used as a diversion in an attack involving a bank heist in Taiwan. The ransomware is thought to have originated from the Lazarus group, a threat actor known to be affiliated with North Korea. (You can be read about them in this blog post about the Blockbuster campaign.). Security researcher @demonslay335 tweeted about the existence of a new sample Hermes 2.1, so our team decided to take a deeper look.
New sample of #Hermes 2.1 #Ransomware spotted by @malwrhunterteam. Using a new filemarker at the end of the file with an encrypted AES-256 key blob per file. https://t.co/JOtgGGwGn3 pic.twitter.com/Atw2hxKjTj
— Michael Gillespie (@demonslay335) February 5, 2018
Code Reuse Analysis of Hermes 2.1
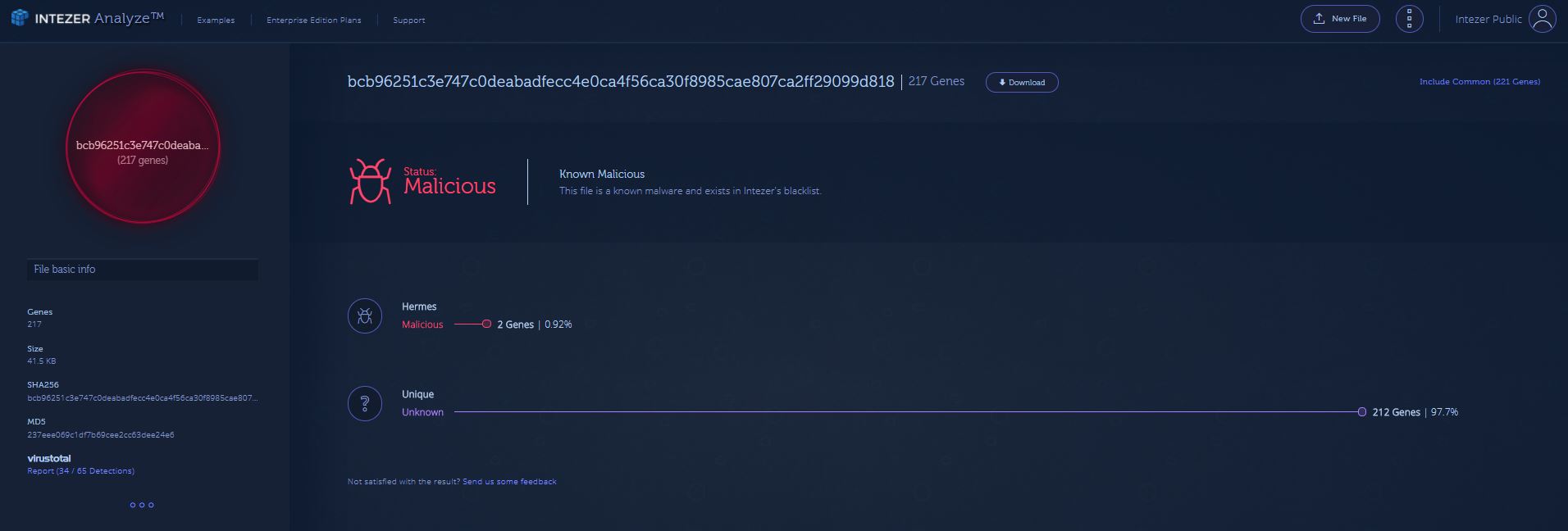
When examining new binaries, the first step we take in our research is to take the binary and upload it to our Intezer Analyze™ system in order to identify code reuse.
(https://analyze.intezer.com/#/analyses/da695d59-d98f-433f-8725-b15217e82348)
Here we can see some code reuse between the Hermes samples that were originally discovered as well as the latest sample. Since the sample came out mostly unique — indicating that much of the binary has changed — we were still able to catch some key parts that clearly reuse code.
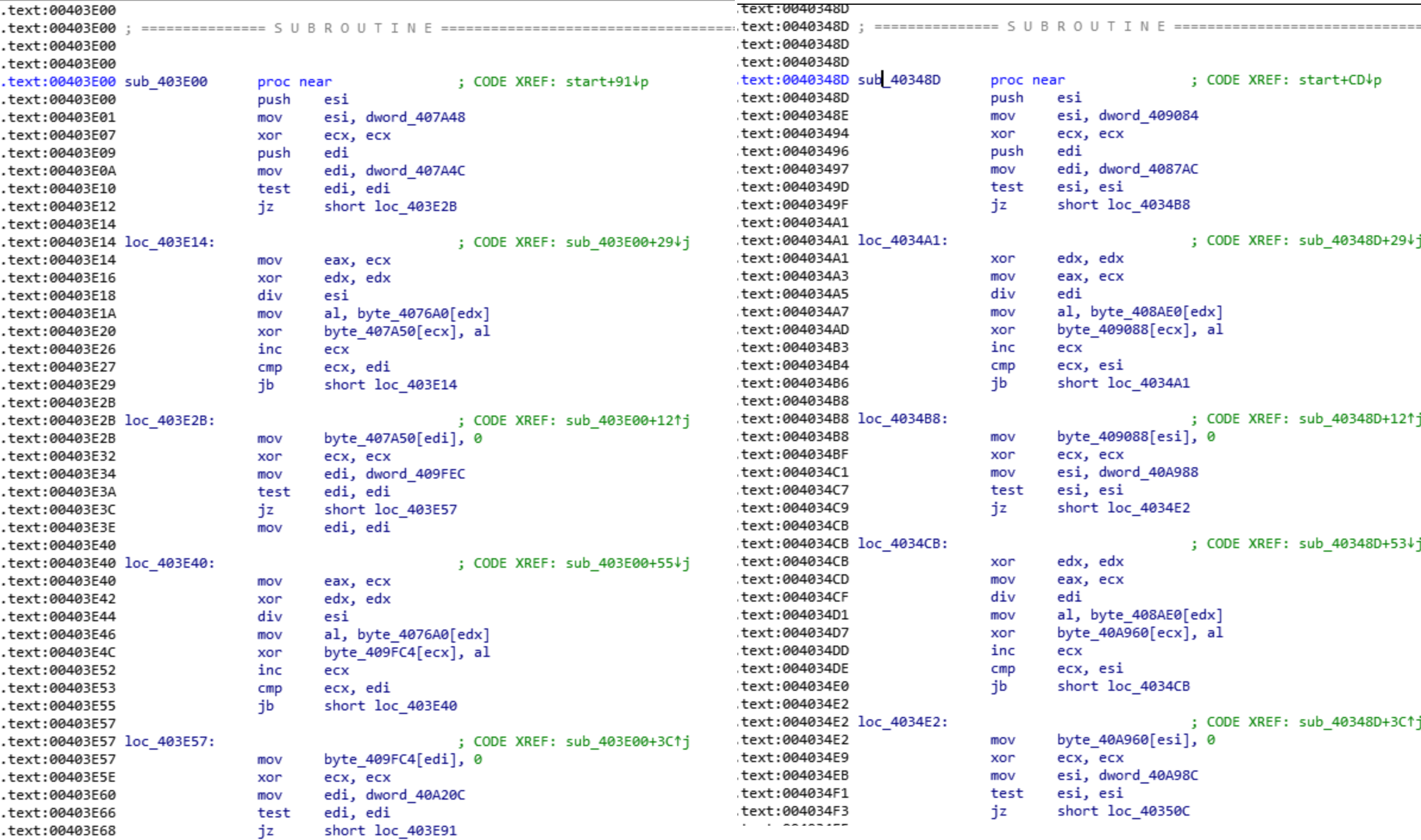
New sample of #Hermes 2.1 #Ransomware spotted by @malwrhunterteam, shares this code with the previous versions, sub_403E00 & sub_40348D at the following sampleshttps://t.co/d2Je6mAR7S pic.twitter.com/CJuNuI9Z0J
— Ari Eitan (@arieitan) February 6, 2018
Intezer Analyze™ caught these fragments, and with a deeper look into IDA Pro, we find an exact function-for-function match:
In other places, although the code is not exactly the same, we can see very similar code to the original Hermes and techniques known to be used by Lazarus.
An Evolving Threat
The last time this ransomware appeared there was a bank heist affiliated with it, and now it is possible that this new sample was used in an attack where the infected target was unaware of the intended result. It may have been used to cover up intellectual property theft, bank fraud, or something even more nefarious. At this moment in time, there is not enough information to make definitive conclusions about the specific intent of the Lazarus group; however, with the reappearance of Hermes, we can be confident that this likely won’t be the last time this code will be used in an attack.
IOCs
New Sample – bcb96251c3e747c0deabadfecc4e0ca4f56ca30f8985cae807ca2ff29099d818
Related Sample – 851032eb03bc8ee05c381f7614a0cbf13b9a13293dfe5e4d4b7cd230970105e3