Developers are not the only ones that have adopted Go.
Malware written in Go has been steadily increasing. In the last few years, almost an increase of 2000% new malware written in Go has been found in the wild. We have seen both nation state-backed and non-nation state threat actors adopt Go into their toolset.
Our new report outlines the uses of Go malware by threat actors during 2020. It includes an analysis of code connections and IoCs for malware that has been active for years and malware that has never been reported publicly on before. Get your copy.
Nation State-Backed
Before 2020, a Russian nation state-backed threat actor had been using its Go variant of Zebrocy. In 2020, we saw a return of this malware in targeted attacks against Eastern European countries. The samples had overlapping code with older Go Zebrocy samples.
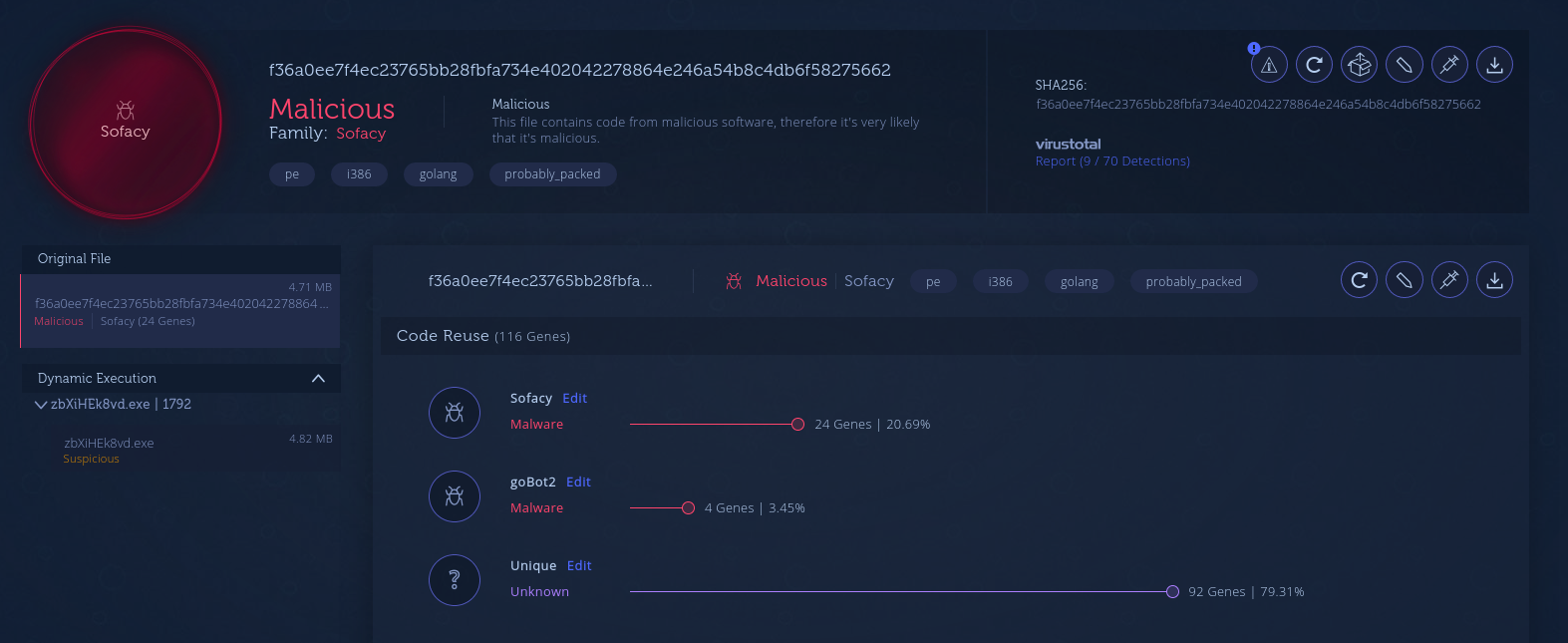
Code similarities between the new Zebrocy sample and older samples
Another Russian nation state-backed threat actor was attributed to a malware called WellMess that is written in Go. According to the UK’s National Cyber Security Centre (NCSC), it was used in attacks against organizations that were part of COVID-19 vaccine research. WellMess has been around for a couple of years but before the NCSC’s report, no attribution to a known threat actor had been made in the public.
A Chinese nation state-backed threat actor utilized a new loader written in Go to execute their malware in some campaigns, and a new threat actor included two malware written in Go in attacks against Tibetan individuals.
Non-Nation State-Backed
On the non-nation state-backed front, crypters, stealers, remote access trojans (RATs), botnets and ransomware were used. Some botnets active before 2020 were still active while some new ones emerged. Some started to target Linux cloud environments.
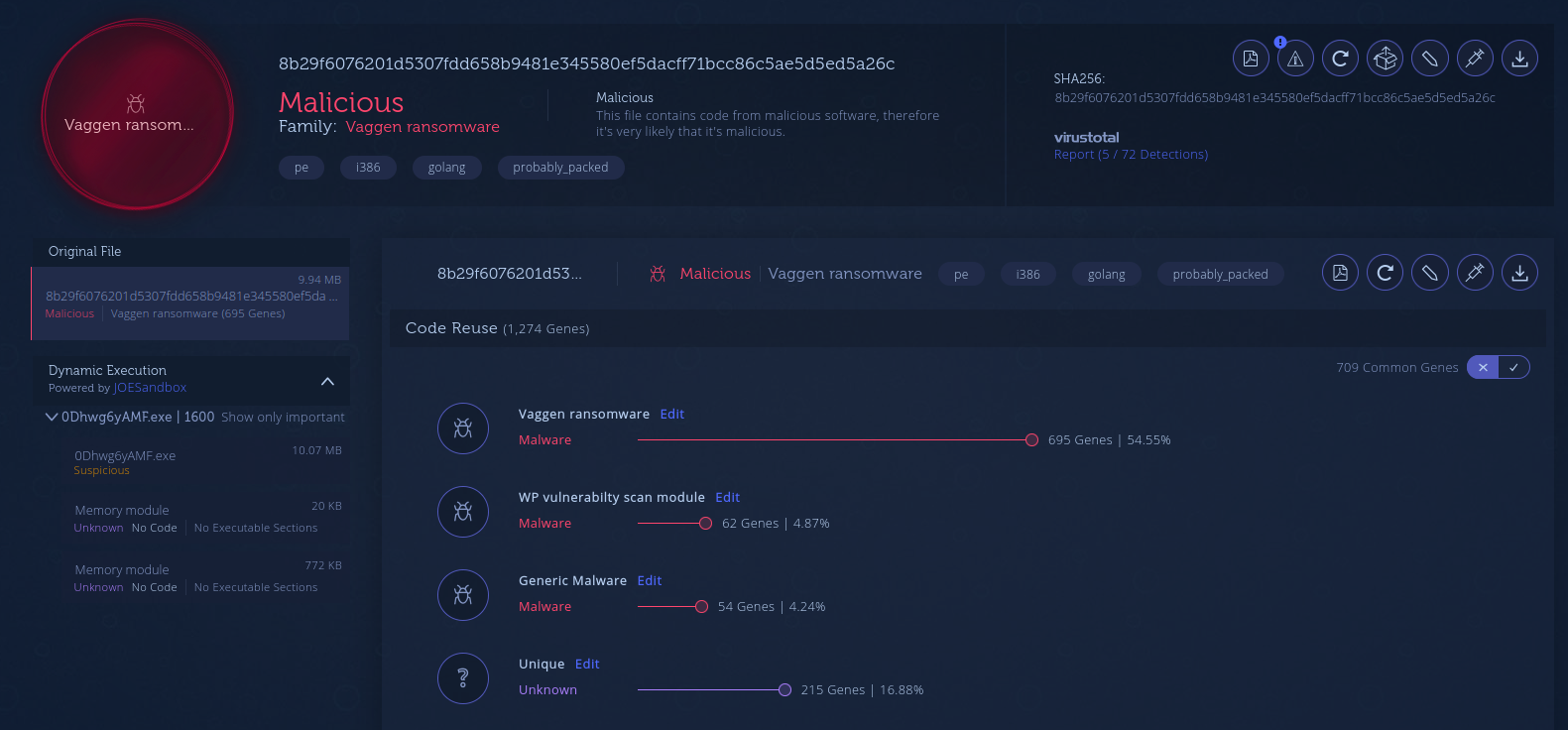
Genetic analysis between Vaggen ransomware and another malware written by the same threat actor
New samples of IPStorm were discovered attacking Linux machines instead of Windows ones. The majority of botnets targeting Linux machines installed cryptominers or commandeered the machine to take part in distributed denial of service (DDoS) botnets.
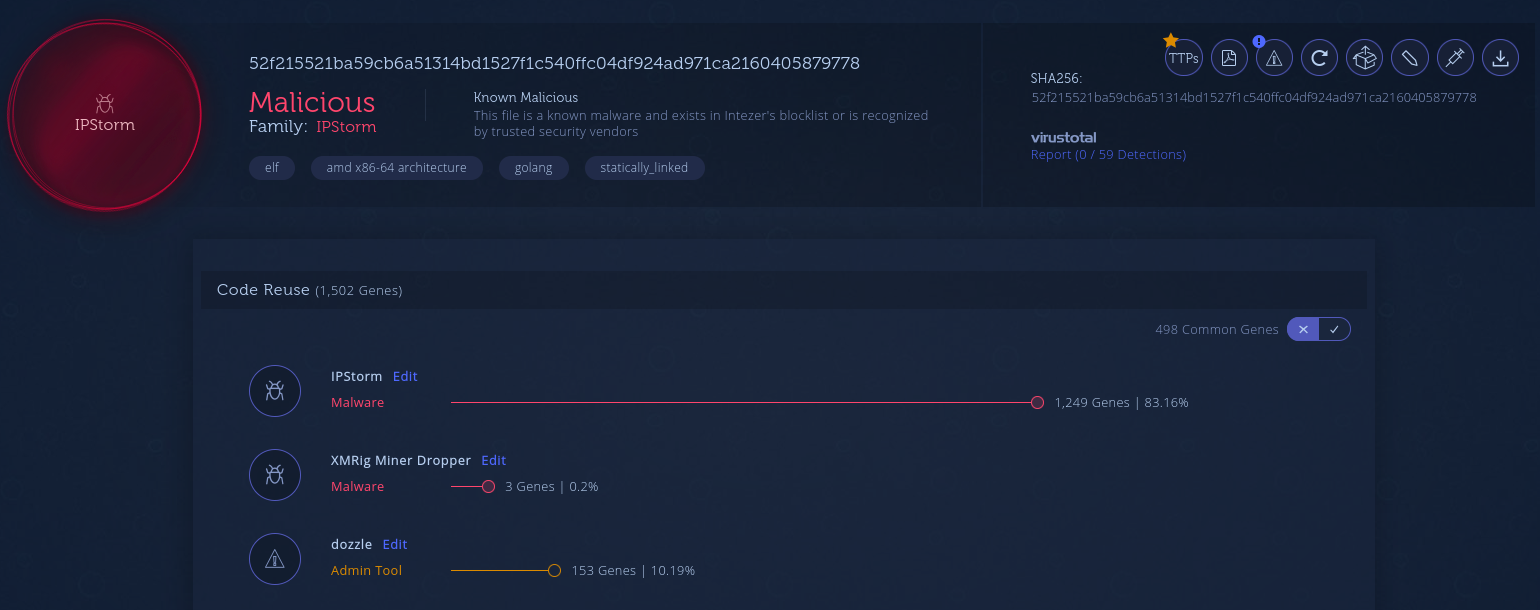
Linux variant of IPStorm
Windows machines were targeted by ransomware written in Go. During the year, some new ransomware was used in so-called Big Game Hunting attacks. Nefilim and EKANS infected Whirlpool and Honda respectively.

Future Predictions
It’s likely that the number of Go malware will continue to increase. We have seen threat actors targeting multiple operating systems with malware from the same Go codebase. Traditional Antivirus programs have had a hard time identifying Go malware due to many factors. A detection method based on code reuse has shown to be effective, especially when it comes to detecting when malware families are targeting new platforms.
It’s also likely that attacks from Go malware against cloud environments will increase as more valuable assets are moved to the cloud. Using the security features provided by the hosting providers will not be enough and specialized runtime protection solutions like Intezer Protect will be needed.
2020 Go Malware Round-Up. Go download the report.
Shoutout to our colleagues at the following companies whose public reports made it possible for us to produce this round-up.
- Alibaba Cloud
- Anomali
- Antiy
- Barracuda
- Bitdefender
- Broadcom
- CCN-CERT
- Carbon Black
- Cisco Talos
- CrowdStrike
- Dragos
- FireEye
- Guardicore Labs
- JPCERT>
- Kaspersky Labs
- LAC
- Malwarebytes
- NCSC (UK)
- Netlab at 360
- Palo Alto Networks Unit 42
- Proofpoint
- PwC
- RSA
- Sentinel Labs
- Sophos
- Trend Micro
- Volexity






