TL;DR: You can now extract IOCs and behavioral indicators to a hunting rule format for your endpoint security system. This enables you to:
- Easily create hunting rules from any threat or alert uploaded to Intezer’s database.
- Automate the threat hunting process by tracking threat actors and getting a continuous feed of detection rules to hunt for in your endpoint security solution.
See it in action –> try now at analyze.intezer.com
Background on our approach to threat hunting rules
In July, we showcased our approach in helping security teams go beyond individual file analysis by automating their security operations.
We went over the repeating patterns we see within security teams across the field and presented the next evolution of SecOps, as we launched our Autonomous SecOps offering along with our new endpoint protect integrations for CrowdStrike and SentinelOne.
Among these is the Detect & Hunt capability which gives you the opportunity to further dive into our unique classification abilities and to present high-quality detection content. This allows analysts to quickly create effective hunting rules, with high accuracy and low false-positive rate.
In this blog, we’ll dive into one of the key features in the new offering – Curated Threat Hunting, AKA ”Rule Extraction.” We’ll look into some use cases and show how we tackle them with Intezer.
Who am I: Matan Eli Matalon, Information Security Manager at Intezer. In charge of Corporate Security, Compliance, Incident Response and Internal Product Implementations.
What is the Hunting Rule Extraction feature?
Intezer provides out-of-the-box detection content and threat hunting queries that can be used within SentinelOne, CrowdStrike (coming soon) and SIGMA (coming soon). This blog will focus on the SentinelOne integration, but most will be relevant for the other systems as well, so stick around. 😉

Use case #1: Hunting as part of Incident Response
Let’s say we’ve encountered malware. Whether we got an alert from our endpoint detection and response (EDR) solution, or scanned it in Intezer – we know it’s malicious, But we need more information. We want to hunt for additional infections in case it has spreaded across our network, or maybe it gained some sort of persistency on the machine.
We’ll start by uploading the file to Intezer (this can be done manually for an individual, or via the EDR integration for large volumes of files).
Once we get the malicious verdict, we’ll browse to the Detect & Hunt page for additional IOCs and behaviors related to the malware or its family.
Now, we’ll select the IOCs we wish to hunt in our environment (could be all of them, up to you).
The pyramid on the left side can help us select the most effective detection opportunity. Each level represents a different Artifact Effectiveness. Effectiveness level is per artifact type. It is determined by the expected potential of detection accuracy and average lifespan the artifact type has.

We’ll click on the “Extract Rules” drop down and select the relevant system to generate the rules for.
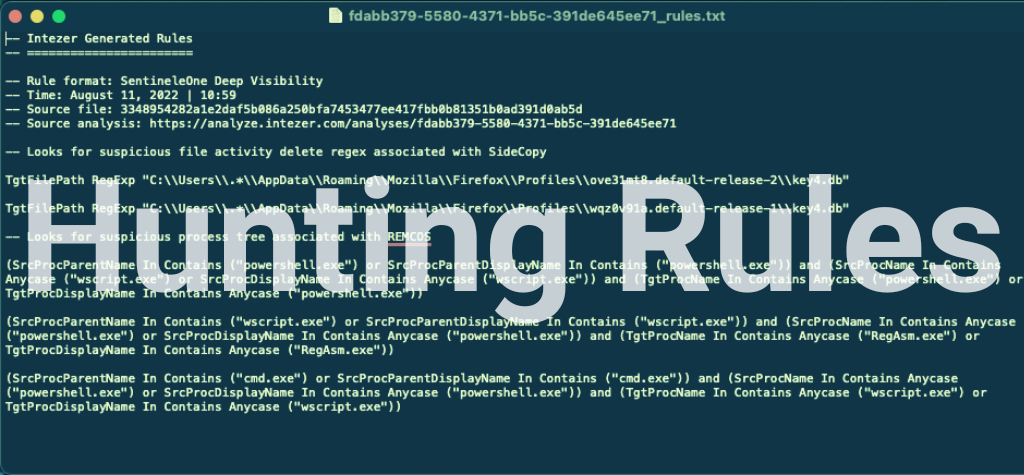
After completing this process, a text file containing the rules for the selected indicators is downloaded to our machine.
There are two paths we can take from here and they both depend on our needs. If the malware is an immediate threat to our environment, We’d copy the rules, paste them into SentinelOne Deep Visibility as a hunting query and see if the indicators currently exist:

In cases which the threat to the environment is probable, we’d like to hunt for the indicators over time, and have the EDR alert us on any changes. We’ll copy the rules from the text file, but instead of pasting them in the hunting queries tab, We’ll create a custom rule.
*Note: We recommend to test the query before creating the rule, to avoid any false positives.
Custom Rules allow you to create a query that runs over a specific time period or permanently, and has the capability of remediating the threats you’re hunting for.

Here you can see the workflow for this use case for extracting custom hunting rules:
Use case #2: Continuous proactive hunting for threats of interest
In addition to file scanning, Intezer offers the ability to track certain malware families and threat actors. Once you are subscribed to a threat, you get email notifications about any new detection opportunities for that threat.
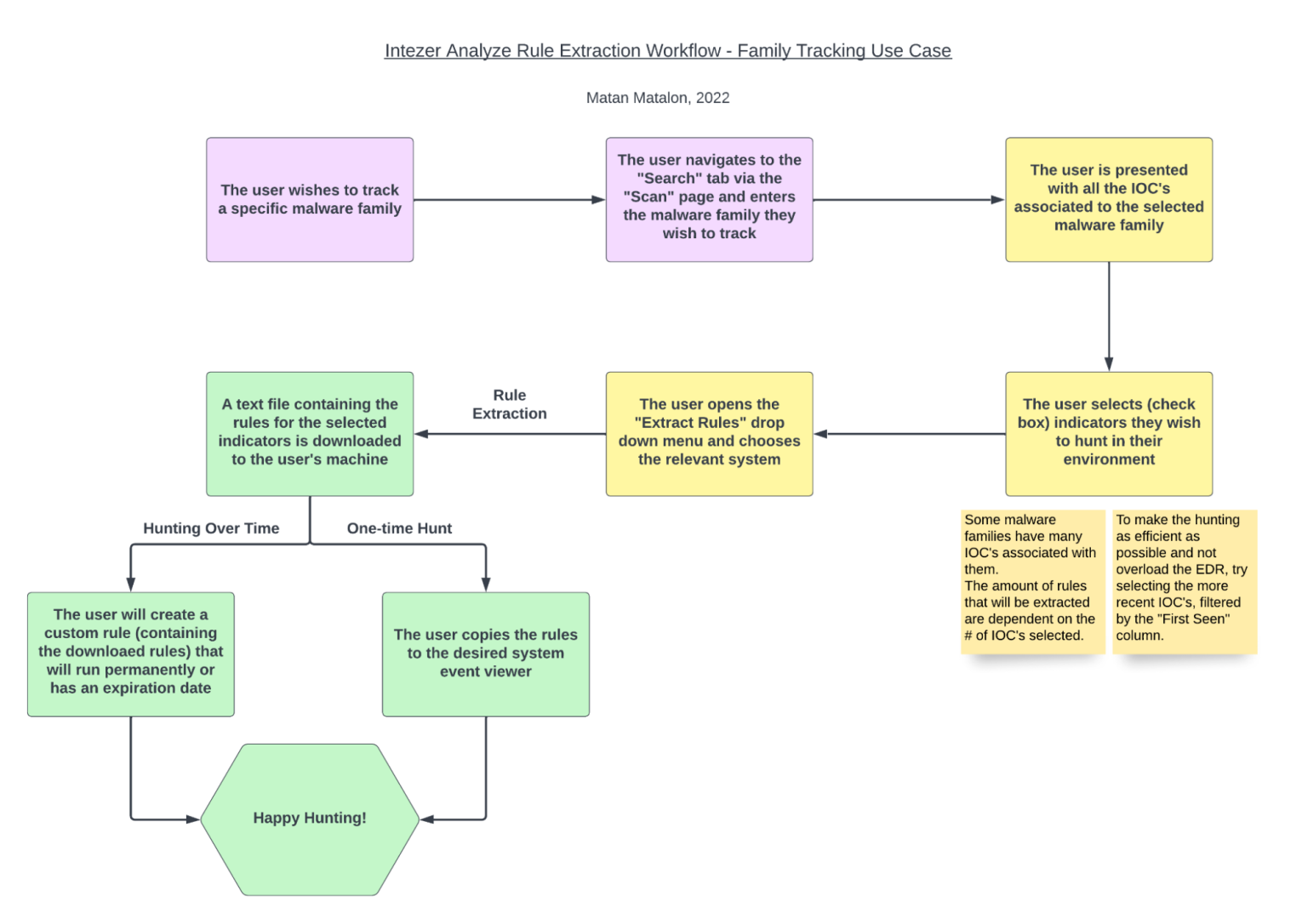
The workflow for this use case is quite similar. The Detect & Hunt tab will be visible from the main family page and this page shows aggregated detection opportunities from all observed samples of the family.
Like in the previous use case, we’ll select the IOCs we wish to hunt in our environment, extract the rules using the dedicated drop down and select the relevant system to generate the rules to. A text file containing the queries will be downloaded to our machine.
In this proactive use case, the more reasonable approach would be tracking these threats over time (rather than hunting for them only once), because the family as a whole is less likely to appear together at the same time. So like in the previous use case, we’ll test the queries prior to creating the custom rules for them, and if we deem it valid, we’ll create them immediately from the search bar.

*Note: Some malware families have many IOCs associated with them. The amount of rules that will be extracted are dependent on the # of IOCs selected. To make the hunting as efficient as possible and not overload the EDR, try selecting the more recent IOCs, filtered by the “First Seen” column, and of course use the pyramid on the left side.
Here you can see the workflow for tracking threat actors and malware families, to enable proactive hunting as threats evolve:
Happy Hunting!