Learn more about how Intezer works here and its automated incident response process, which provides you with TTPs and so much more.
Classifying a threat is just one step in a SOC analyst’s investigation. You know it’s malicious but what does it do?
Steal credentials? Exfiltrate data? Lateral movement? These are just some examples. As a SOC analyst, it’s important to understand what the file is capable of in order to craft your response.
To help with this, thrilled to launch our latest Intezer feature: Tactics, Techniques, and Procedures (TTPs)! This feature helps SOC analysts quickly understand malware behavior and capabilities, to assess the risk and better tailor the response. When faced with simultaneous threats, TTPs also provide tips on which to prioritize first based on potential impact to the company. We’re helping security teams answer all the questions they need to automate end-to-end malware investigations, under one platform.
Automatically Mapping TTPs to MITRE ATT&CK
This feature is powered with CAPA, the open-source library by Mandiant. CAPA works statically on the assembly level, identifying recognizable patterns and API calls in executable files to explain what they are trying to do.
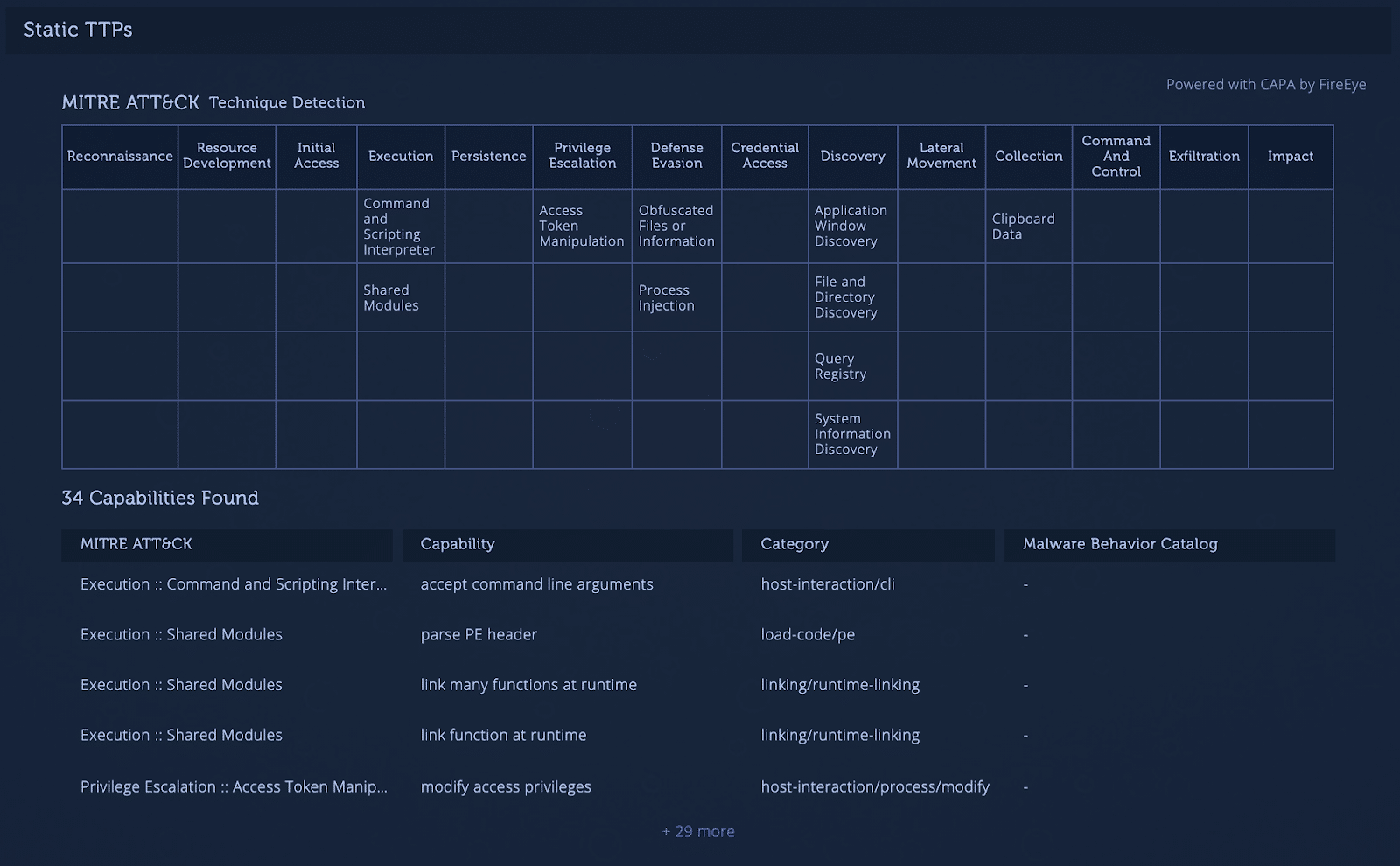
Intezer Analyze detects TTPs by scanning files statically with CAPA and matching the assembly to a collection of predefined rules covering the MITRE ATT&CK framework. For example, it might suggest the malicious file is a backdoor capable of installing services or that it relies on HTTP to communicate. Static TTPs are available for files including automatically unpacked files, endpoint analysis for memory forensics, and memory dump analysis. As part of utilizing CAPA, our research team will also be contributing to the project by adding community rules based on our unique genetic code analysis insights.
Let’s look at an example.
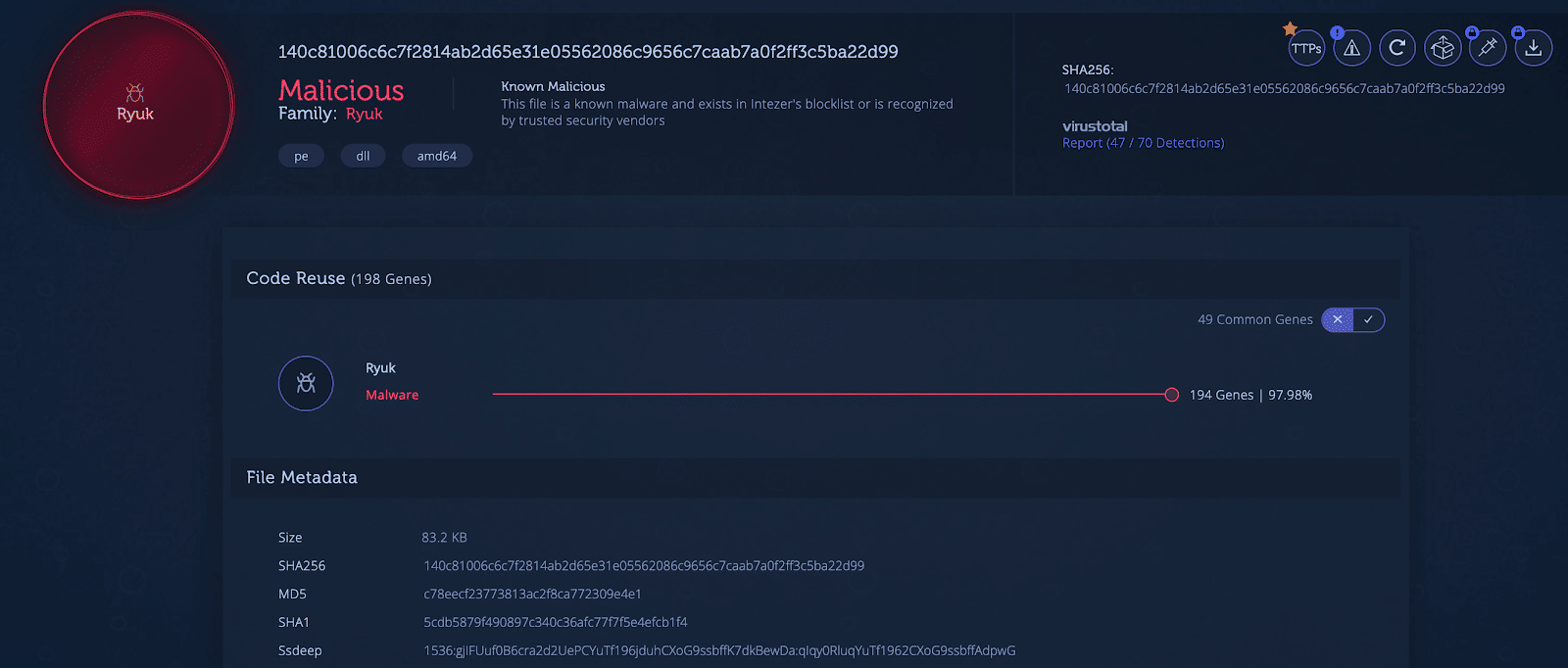
1. Intezer Analyze detects this Ryuk ransomware sample.
2. Click on TTPs. A list of capabilities and the relevant TTPs are returned telling you what this program can do based on the MITRE ATT&CK Matrix. Intezer found 34 capabilities. The malware can perform actions such as process injection to remain hidden in the network, collect data from the clipboard, or query the registry to collect info about the victim’s machine.
3. That’s it. You have relevant insights about the TTPs to assess the risk and potential impact. I encourage you to give this new feature a try. If you don’t have a file to analyze at the moment, visiting the Intezer Analyze homepage is a great place to start. You can choose from the latest top community uploads, or type a malware family in the search engine and grab a file from its related samples detected by code reuse.
TTPs for Fast Incident Response
TTPs are supported for PE files and other files collected and analyzed by Intezer:
- Users can see TTPs linked to specific/relevant parts of the code.
- Intezer’s genetic analysis shows which malware family a capability was previously seen, if it’s borrowed from a library, or part of unique code.