We are excited to share that we now support Genetic Malware Analysis for Android applications!
Intezer Analyze community and enterprise users can now detect code reuse in Android file formats. Supported formats include APK files such as ARM executables (32 and 64 bit) and Dalvik-based modules.
Increasing Adoption of Android Devices
The increasing adoption of Android devices over the last few years, keeping in mind the sensitive information that is stored there, makes this operating system an attractive platform for cyber attacks. Android threats are rising and there are still many malicious apps on the app stores. We wanted to provide the industry with a more effective way to identify threats in this space.
Lazarus Embedded within an Android Application
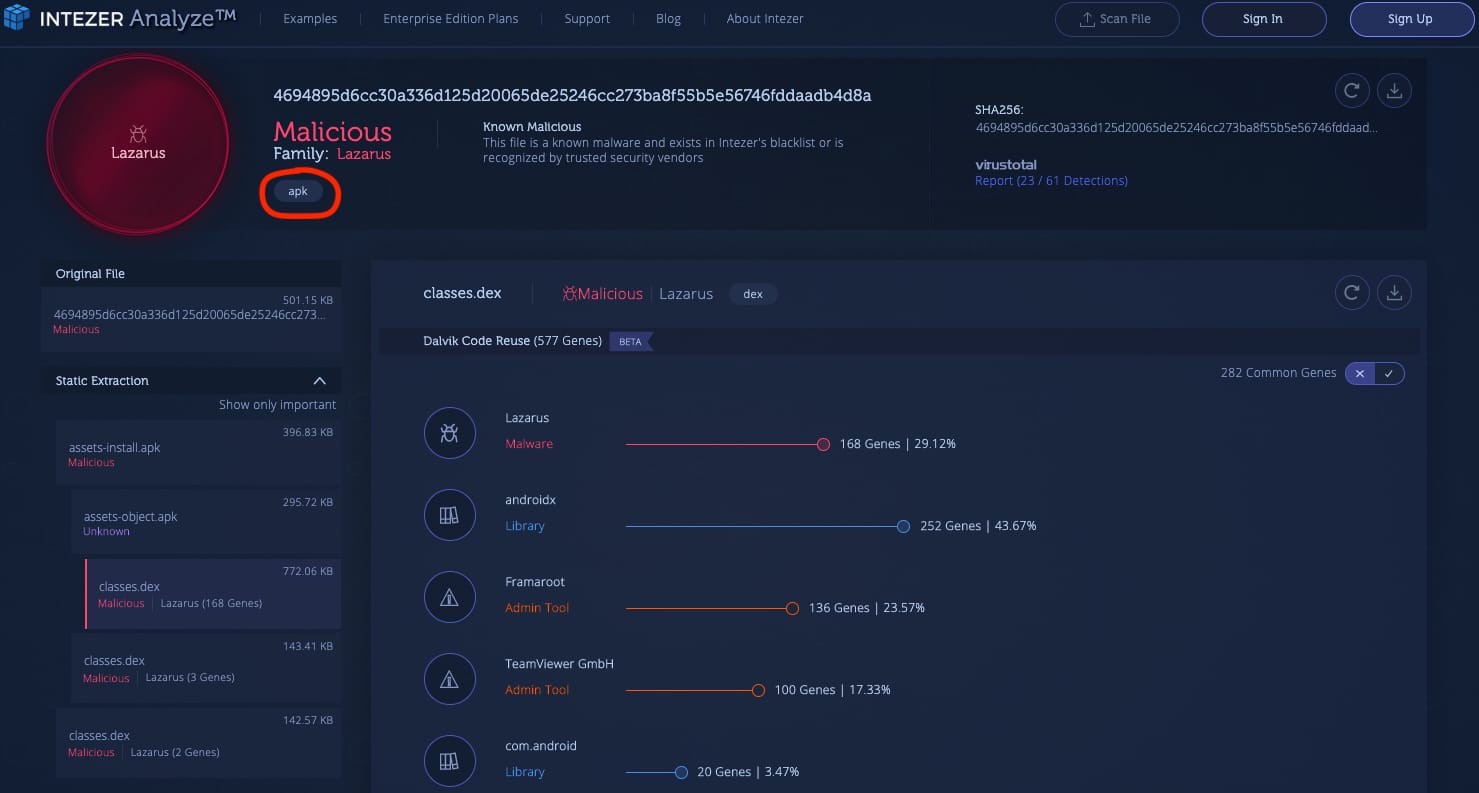
We recently detected a malware campaign launched by the cyber group Lazarus, which has alleged ties to the North Korean government, embedded within an Android application. After automatically unpacking the APK file, Intezer Analyze identified three embedded dex files which contain code from previous Lazarus variants. View the genetic analysis:
Intezer Analyze now proudly supports genetic analysis for Windows and Linux executables, in addition to Android APK files.
To get started genetically analyzing your own files and Android APKs, visit analyze.intezer.com or contact us.