TL;DR Intezer users can now view comprehensive triage assessments for alerts that Intezer ingests directly in the console, combining insights from multiple sources under one roof.
At Intezer, we constantly strive to empower SOC teams to get better and focus on the serious threats that really matter. That’s why we are thrilled to announce the launch of our latest feature: the all-new Alert Report.
Merging Alert Source Data for Better Visibility
Our new Alert Report brings you undifferentiated triage like never before. Seamlessly merging ingested alert data from your existing alerting tools with Intezer’s automated evidence collection and comprehensive analysis, we provide a consolidated view that equips you with the context and visibility you need to conduct effective investigations.
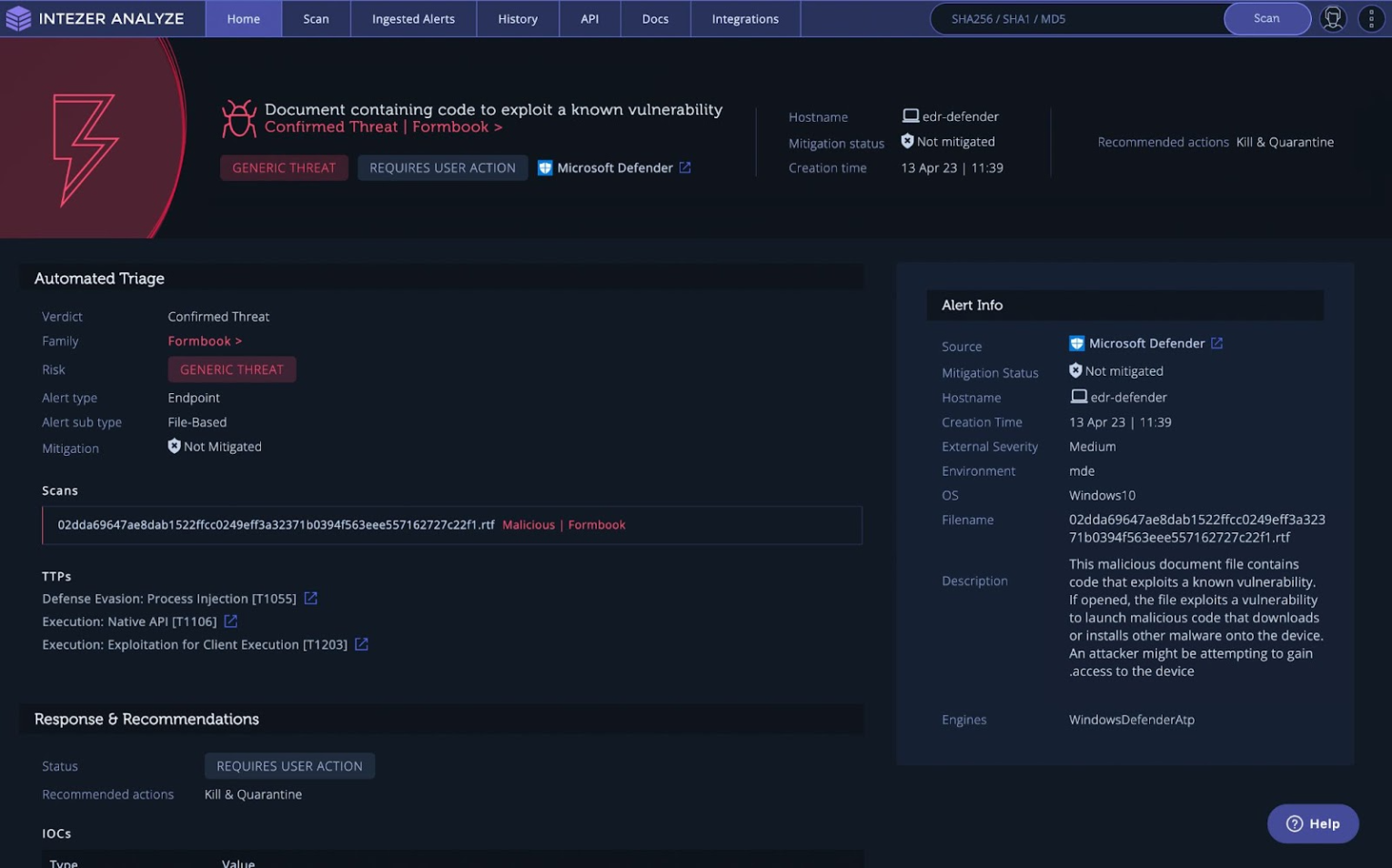
Once an alert is automatically triaged, Intezer generates an extensive alert report that arms you with the following critical information:
- Alert Triage Verdict: Indicates the triaged verdict based on code reuse and analysis of other artifacts.
- Classification (Malware Family): Specifies the threat classification based on code reuse findings.
- Alert Triage Risk: We assign a risk level to each ingested alert, enabling you to prioritize your actions and allocate resources accordingly.
- Recommended Actions: Specifies the recommended actions for your team to remediate.
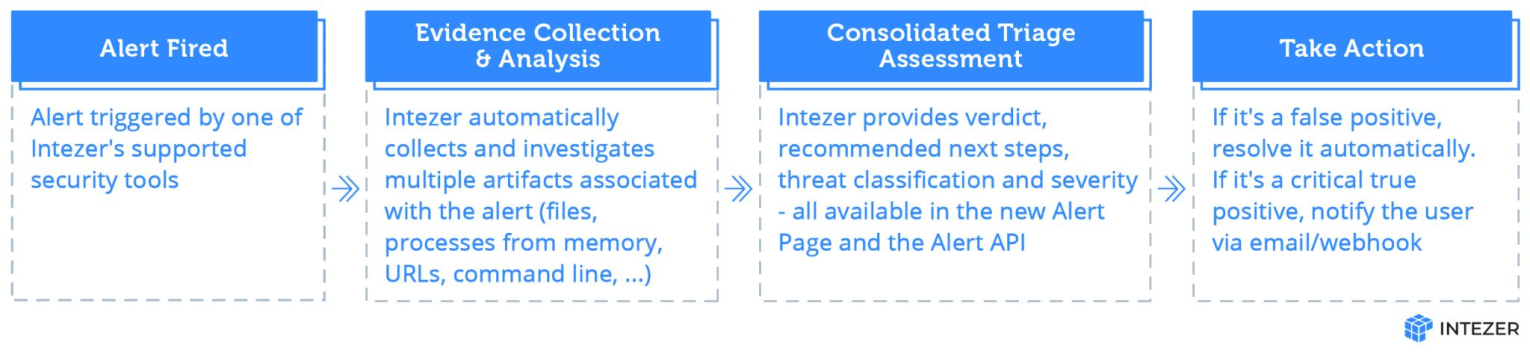
In addition, the Alert Report aggregates all the evidence that was collected and analyzed as part of triaging a certain ingested alert and presents it under one roof. For example, a CrowdStrike alert can result in Intezer collecting a suspicious file, a URL that was seen in the command line in that alert, and even a live memory scan of the machine. All those artifacts and their associated analysis would be easily accessible on the Alert Report of that CrowdStrike alert.
Furthermore, the Alert Report effortlessly combines this information with the data retrieved from your alerting tools, such as endpoint security, email security, and more. Critical details like mitigation status, OS version, process command line, and others are seamlessly integrated, offering you a complete and accurate detection and triage experience.
This capability is particularly advantageous when it comes to detecting memory-based threats, PowerShell, and LoTL (Living-off-the-Land) threats. Threats that lack files can be elusive, hiding within scripts or command lines. However, with our new triage and Alert Report, you can accurately identify and handle these evasive threats with ease.
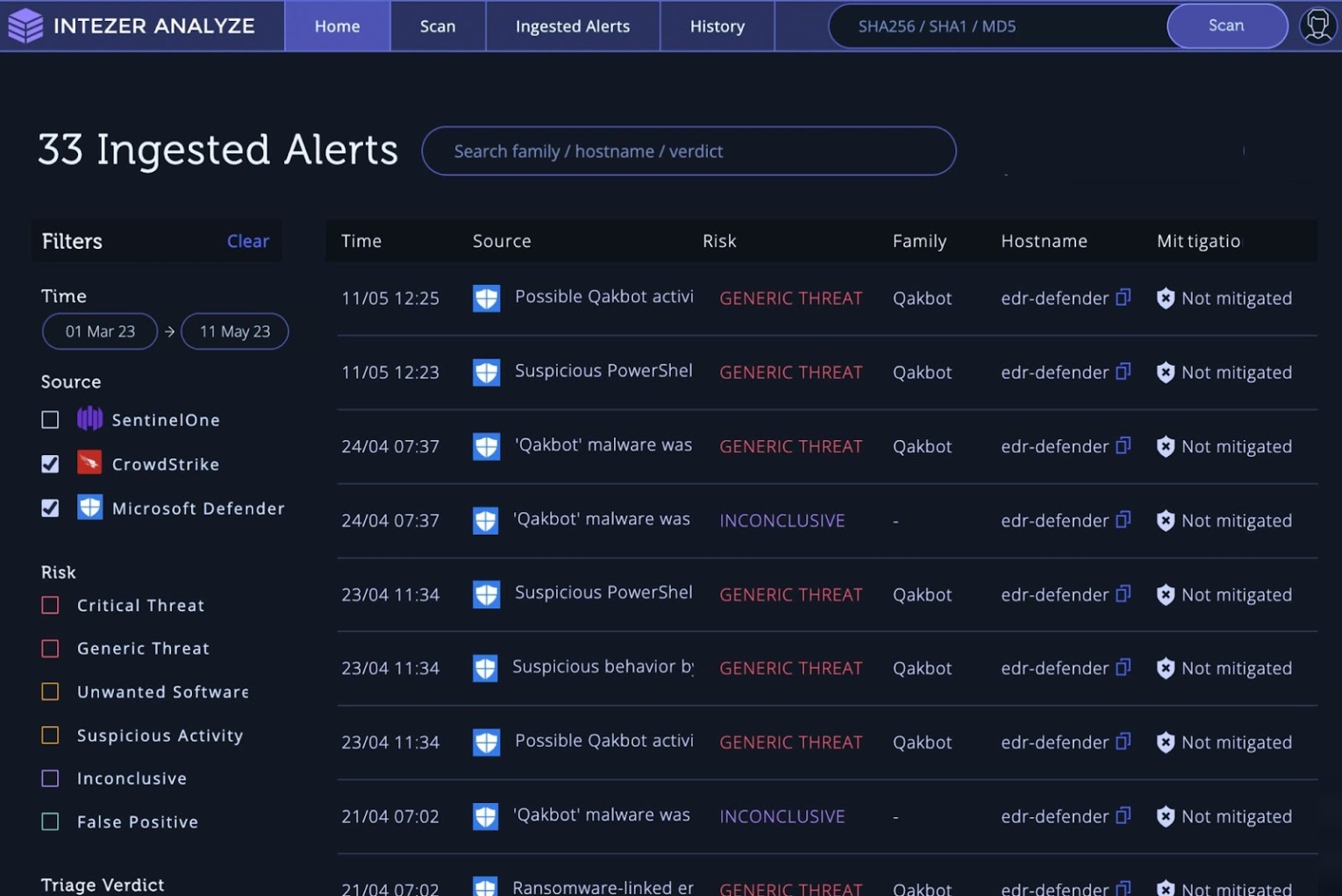
Integrate Smart Alert Triage Assessments with Your Preferred Security Tools
Excitingly, the complete alert triage assessment that you find in the new Alert Report is also available through our API, allowing security teams to seamlessly connect Intezer’s automated decision making and analysis with your preferred tools. While so far the Intezer API only provided ways to leverage Intezer for individual analysis of files and other artifacts, now, you can enjoy the same comprehensive insights for an entire incident or alert, directly within your tool of choice, integrating smart decision making seamlessly with your day-to-day workflows.
For example, you can use the Intezer API to get the verdict (false/true positive) and recommended actions for a specific SentinelOne alert ID, to build a playbook that runs custom actions based on the response.
Refer to our API documentation for detailed information about how to interact with this capability.
Get started
By delivering accurate and in-depth triage, Intezer fulfills its promise of equipping SOC teams with the tools they need to save precious time and prioritize what matters most.
To get started, connect your EDR to Intezer’s platform. Once connected, you can access the “Ingested Alerts” page via the menu or directly in your EDR alert note. We invite you to get a tailored demo. Simply click here to schedule your demo, and our dedicated team will promptly assist you.