As manager of the free Intezer Analyze community edition I witness first hand the interesting samples our users upload on a daily basis. Among these uploads users will discover unique samples such as previously undetected malware or new variants. As part of a recurring theme and in the spirit of information sharing, I would like to highlight five notable uploads made to the Intezer Analyze community this month and explain why I believe they are significant.
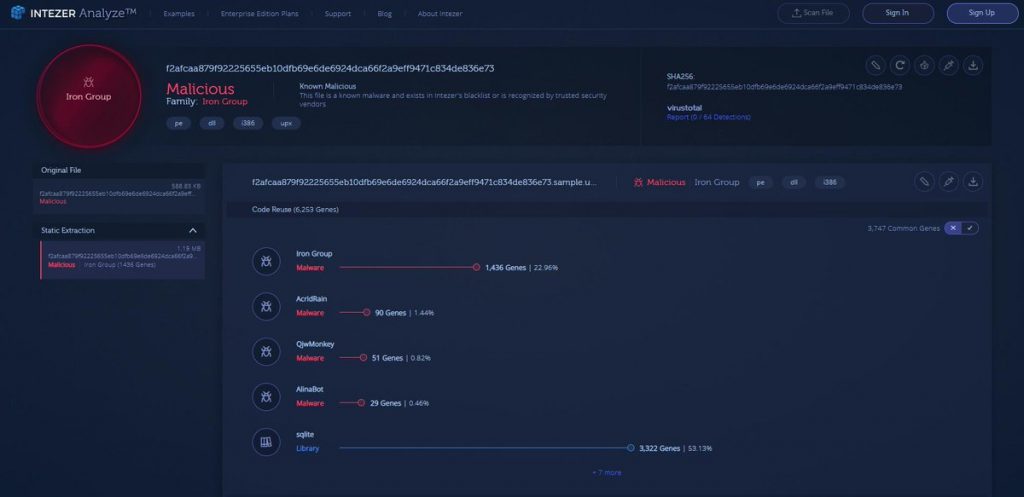
1) Unpacked Malware Sample by the Iron Group [Link to the Analysis]
This is an undetected malware sample by the Iron Group, packed by UPX. The Iron Group has developed several types of malware (backdoors, crypto miners and ransomware) for Windows, Linux and Android platforms. They have used their malware to successfully infect at least a few thousand victims.
More about the Iron Group here.
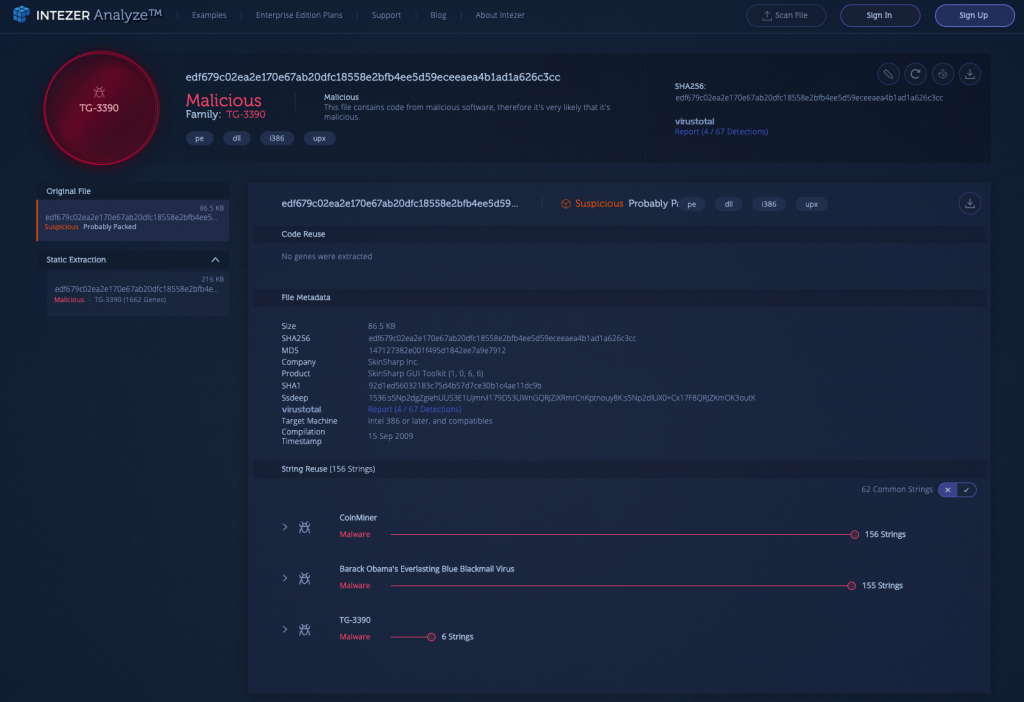
2) Payload Classified as TG-3390 [Link to Analysis]
This sample was packed by UPX. It was automatically unpacked by Intezer Analyze and the payload was classified as TG-3390, also known as APT27, a Chinese threat actor.
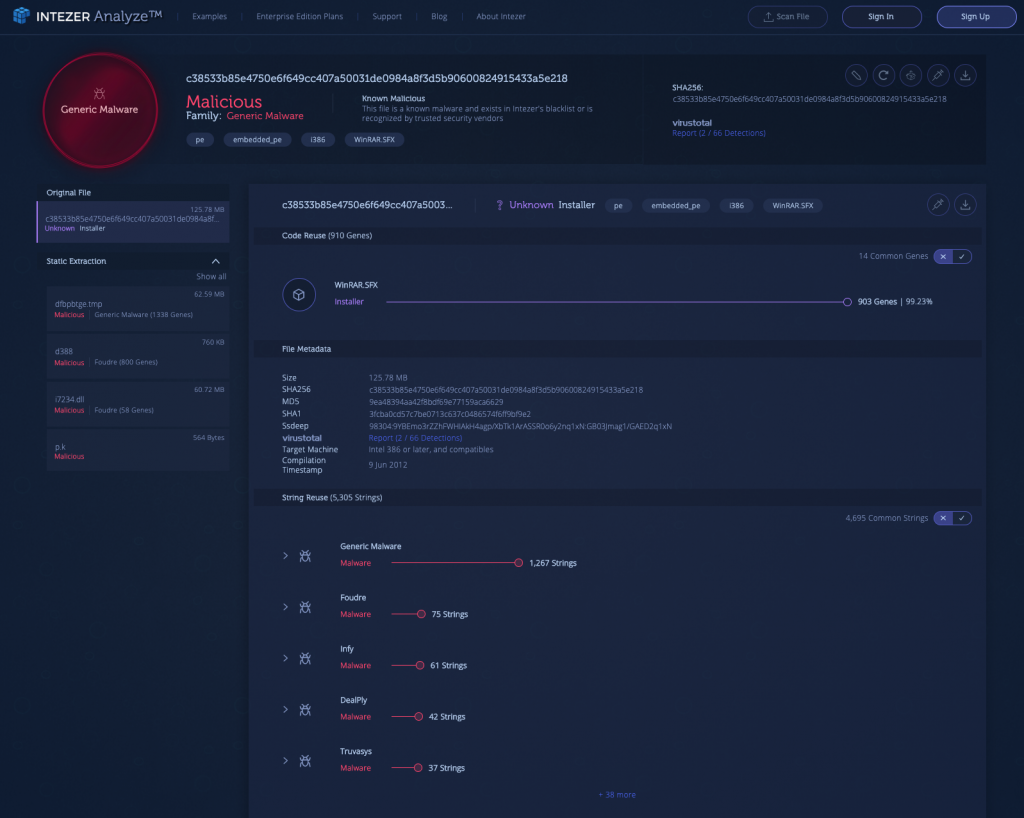
3) Malicious Installer Drops Payloads Related to Foudre [Link to Analysis]
This is a malicious installer which drops payloads related to Foudre, an upgraded version of Infy, also known as Prince of Persia. This malware is part of a campaign which is believed to be of Iranian origin and ongoing for more than 10 years.
Read more in our blog post on the subject.
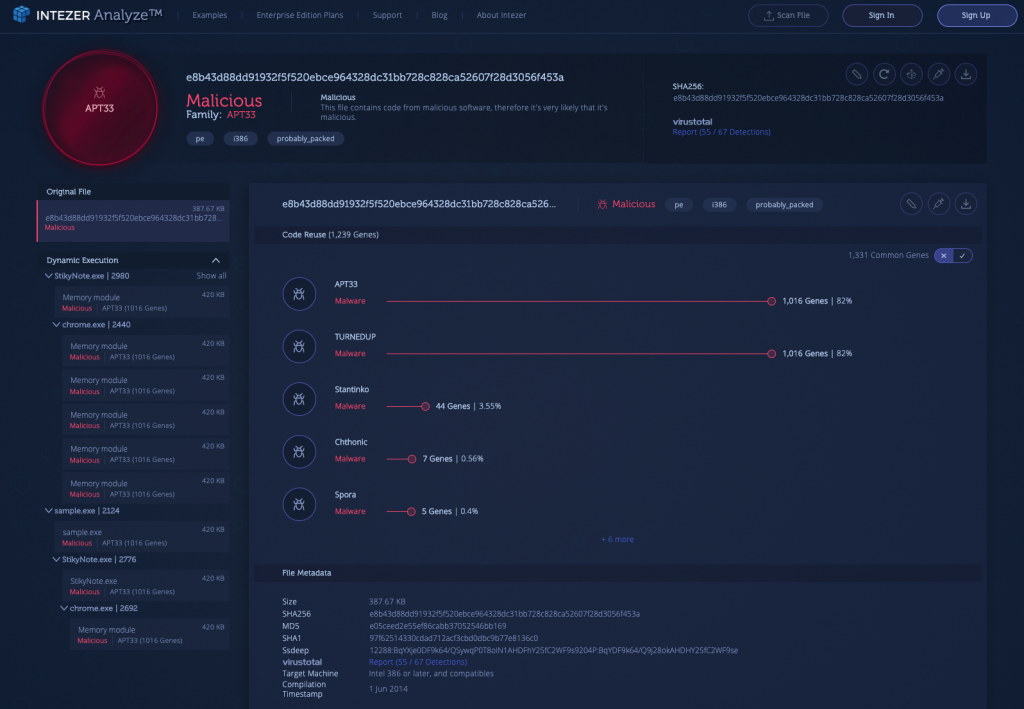
4) APT 33, Dynamic Unpacking [Link to Analysis]
The following is an analysis related to APT33. Note the process tree which was spawned during dynamic unpacking. You can see processes like StikyNote.exe and chrome.exe which were injected with malicious code.
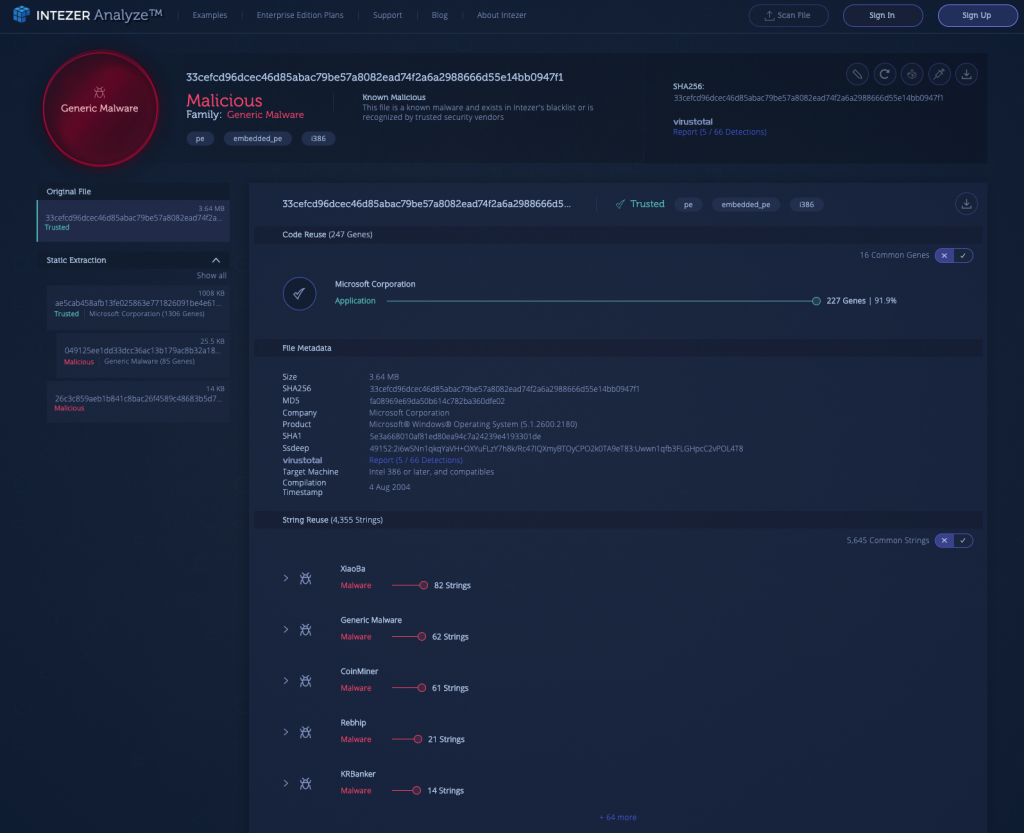
5) Malicious Payload Hiding within Trusted Software [Link to Analysis]
This sample initially seems trusted, but it contains an embedded malicious PE, extracted by static unpacking. It’s not uncommon to see a malicious payload hiding within a seemingly trusted piece of software, which is why Intezer Analyze provides automatic unpacking capabilities.
Not an Intezer Analyze community member? Sign up for free here: https://intezer.com//intezer-analyze/.