TL;DR Make sure your team immediately gets Intezer’s investigation findings about confirmed, critical threats, by sending automatic notifications via email or tickets in any webhook-supported system your team uses like ServiceNow.
At Intezer, we’re always looking for ways to make your security operations more efficient and function like a real extension of your team. One of our key features so your team knows about incidents that require human intervention: Automated Threat Escalations.
The Challenge of Cutting Through The Alert Noise
Every security team dreams of focusing their efforts on serious incidents, rather than spending their valuable time “chasing ghosts.” However, achieving this dream is often easier said than done.
The sheer volume of alerts can be overwhelming and the lack of contextual information makes it difficult to identify and prioritize the most serious incidents. Also, resource shortages and skills gaps cause security teams to struggle with deeply investigating all alerts.
At Intezer, we’re on a mission to make this dream a reality. We believe that by providing the right tools and resources, we can empower security teams to work more efficiently and effectively. Scaling a SOC team to keep up with more and more alerts is a challenge, which “intelligent” security operations automation can help solve.
To better deliver on our promise of helping our customers stay focused on what matter most, in addition to reducing noise and false positives — Intezer highlights critical incidents that require user attention and action. While Intezer already helps with automated investigation of every endpoint (EDR) alert and automatically resolving false positives, Threat Escalations allows team to prioritize response.
Intezer already uses alert triage notes or comments to communicate an alert analysis, but escalations helps security teams that use additional communication channels like email, ticketing systems, or even phone calls which are expected to be used according to the severity or urgency level of the alert. While teams can still review our triage assessment for every true-positive alert (and the false positives alerts too), our Threat Escalations helps you configure notifications and tickets that fit into your regular workflows for urgent incident response.
Customizing Threat Escalations from Your Automated Investigations
To address the challenges of prioritizing serious incidents, we’ve developed Threat Escalations from Intezer. This feature includes two main capabilities:
- Alert Reports: A comprehensive analysis of an entire incident, offering a verdict and suggested actions based on all the evidence that was collected and analyzed from the original alert fired by your security tool. Instead of manually interpreting multiple individual analyses, this feature enables your team to get an enriched, clear picture for each alert and understand what to do next.
- Threat Escalations Notifications: Notification for alerts based on determined severity following Intezer’s investigation. Notifications can be sent via email, and any webhook-supported system (such as your SOAR, ServiceNow, Jira, PagerDuty, other case management systems, even designated Slack channels). This enables you to ensure that high-priority, confirmed threats are escalated appropriately from Intezer when your team needs to take action.
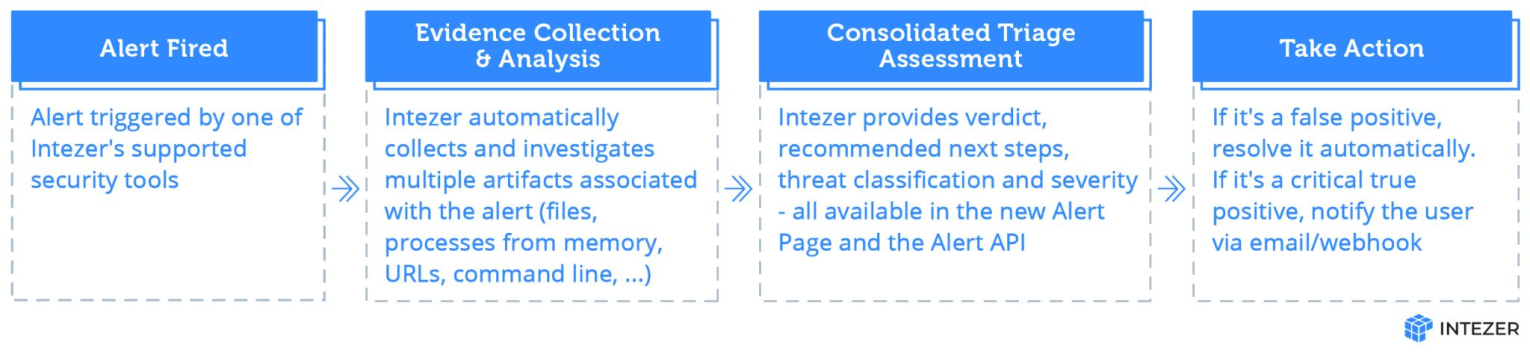
Here’s a quick look at Intezer’s native incident response process, for alert triage and escalation:
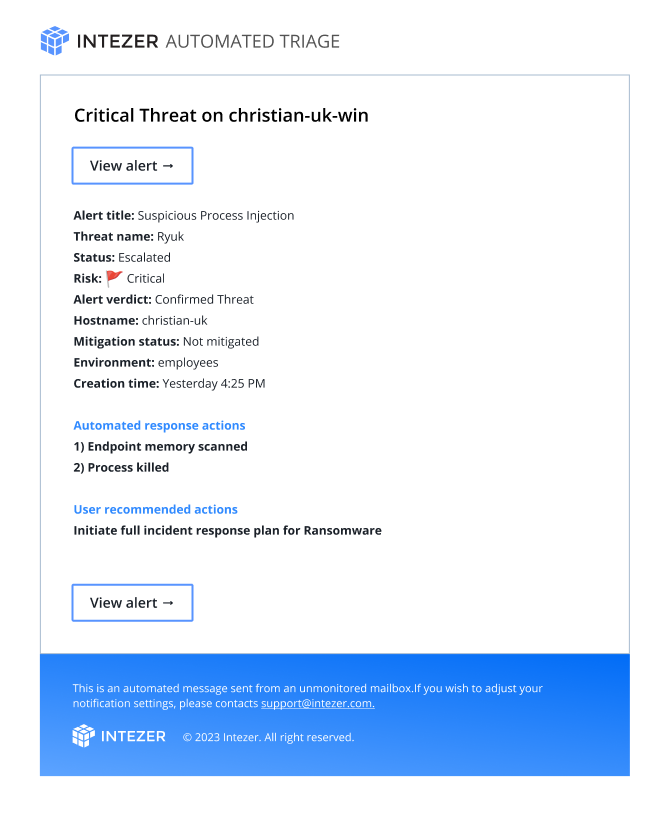
Here’s an example of a threat escalation notification about an unmitigated, critical alert that Intezer investigated:
Alert Notifications That You Control
By default, we send a notification only for high-severity threats (such as ransomware) and for any threat that was not mitigated by your existing security tools and requires action from your team. On average, we find Intezer only needs to escalate about 4% of the alerts that it investigates.
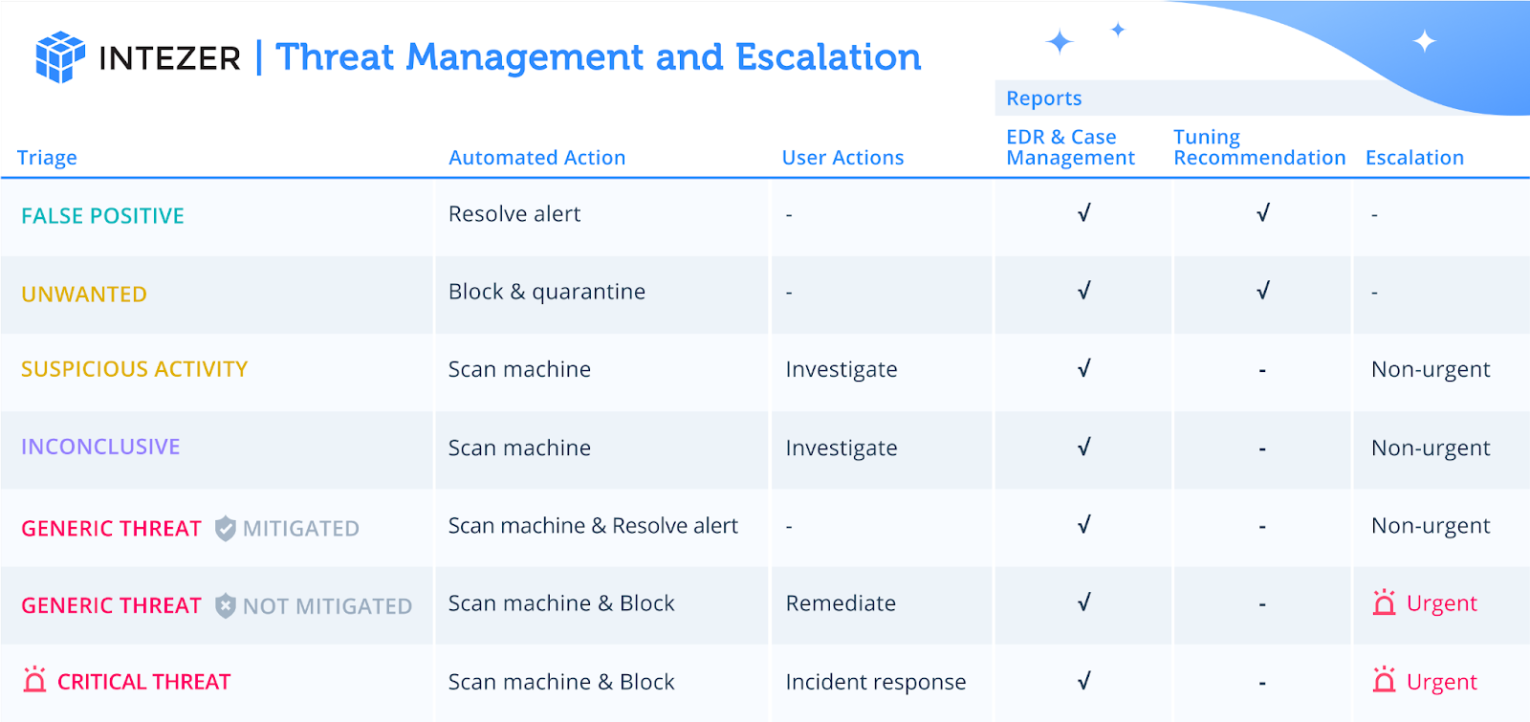
However, you can customize the notification settings to fit your needs. The table below showcases the different types of triage assessments and severity levels, as explained in our documentation, and details what automated actions are taken for each type. For each type of triage assessment, you can completely control if and how you want to get notified, both by webhooks and by email.
This allows you to create tickets in a system like ServiceNow for every alert that Intezer analyzes from your endpoint security tool, or customize it to escalate only a specific triage category like urgent threats about your investigated phishing emails.
The Impact of Escalating Critical Threats
Threat Escalations is more than just a new feature – it’s a game-changer for your security operations. By automatically resolving false positives, providing context for each alert to accelerate investigations, and now – escalating high-severity alerts to your system of choice – you can focus only on the alerts that matter most, without having yet another “pane of glass” to look at 24/7.
This escalation capability can directly help your team cut through the noise and quickly take action to mitigate risks.
Learn More about Escalating Investigation Findings
For a walkthrough of the Threat Escalations feature, we invite you to watch our recorded webinar video, starting at the 10:22 timestamp here. You can also refer to our documentation for more information.
Also, feel free to talk to us to set up a quick online trial to test this feature as well as Intezer’s full automated triage experience.
We’re excited to see how Threat Escalations will transform your security operations and we’re here to support you every step of the way.





