Learn more about Intezer’s capabilities for automating user-reported phishing investigations and sign up to try for free here.
At Intezer, we’re committed to enhancing security operations efficiency and effectiveness. Earlier in 2023, we were thrilled to announce the launch of our new features for Automated Phishing Investigations. These capabilities are designed to automate the analysis and classification of suspected phishing emails (commonly, employee-reported phishing), saving your organization valuable time and resources.
The Challenge of Investigating User-Reported Phishing Emails
Investigating employee-reported phishing is one of the most time-consuming tasks for the majority of organizations. It requires significant resources and can distract from other critical security tasks. These emails often contain attachments like PDFs and innocent looking documents, or malicious links hidden in a QR code image embedded in the email body.
However, phishing remains the leading infection vector and a key place to detect and quickly respond to cyber attacks, particularly targeted attacks. With the rise of sophisticated phishing attacks, it’s more important than ever to investigate these reports thoroughly and promptly.
Introducing Automated Phishing Investigations
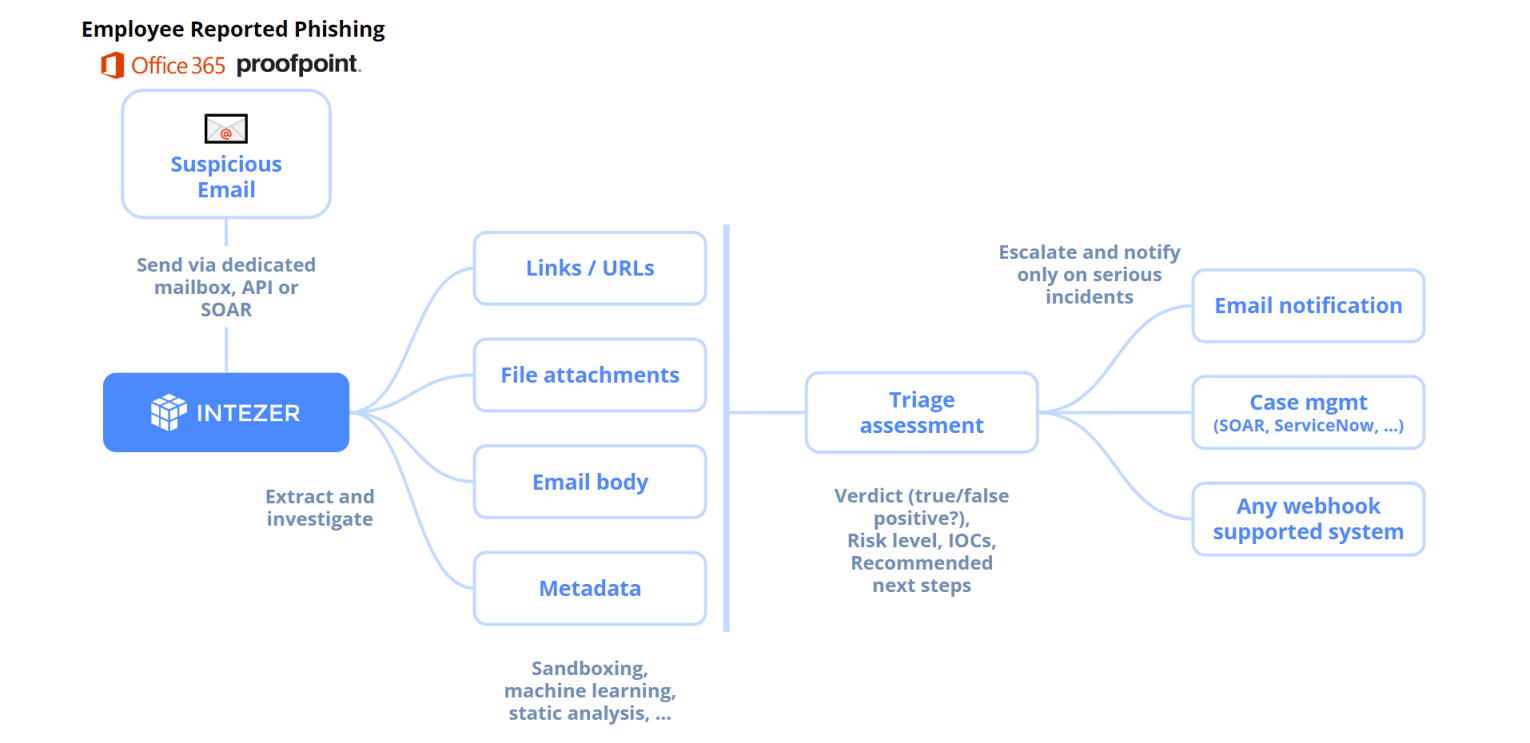
Intezer’s Automated Phishing Investigation features address this challenge head-on. By integrating into any employee reported phishing workflows, such as a dedicated mailbox, Office 365 Report Phishing add-in and Proofpoint’s PhishAlarm, or any other way your employees report suspicious emails — Intezer streamlines the investigation of suspicious emails. This means your team can get notified only about items that require your attention.
For each suspicious email, Intezer provides a clear verdict, priority, classification (malware family or threat actor), and context. This allows you to quickly understand the nature of the phishing threat and take appropriate action.

How Intezer Handles User-Reported Phishing Emails
Automated Phishing Investigation works by parsing raw email data, scanning attachments, analyzing URLs, and using Large Language Models (LLM) to detect phishing manipulations within the email body. Each piece of evidence is investigated separately using our robust analysis engine. The results are then summarized into a single, clear, all-encompassing assessment for the entire email.
After the automatic investigation, we send notifications to your system of choice (email, SOAR, case management system and any system that supports webhooks) only on things that require attention. This ensures that you’re not overwhelmed with alerts and can focus on the most significant threats.
Intezer keeps a full history about every investigated email, so you can always look at the full analysis report about any serious threats or email triaged as “safe.” This ensures you’re able to understand the full context of Intezer’s verdicts, how many false positive alerts have been automatically triaged, and help you calculate improved response times.
AI Insights into Suspicious Emails Reported by Employees
For text-based content in emails, Intezer uses Generative AI to enhance your phishing investigation experience. Intezer generates AI Insights about phishing emails based on its analysis of email body text and HTML. Our Generative AI also checks for hidden elements in email HTML, ensuring robust protection against sophisticated phishing attempts. This allows Intezer to triage questionable emails even in cases without phishing links or attachments, mirroring human investigations by reading and interpreting email content.
Intezer also uses AI Insights to extract and investigate scripts, macros, and other text-based threats, which might be used as part of a phishing attack.
Analyzing URLs and QR Codes in Emails
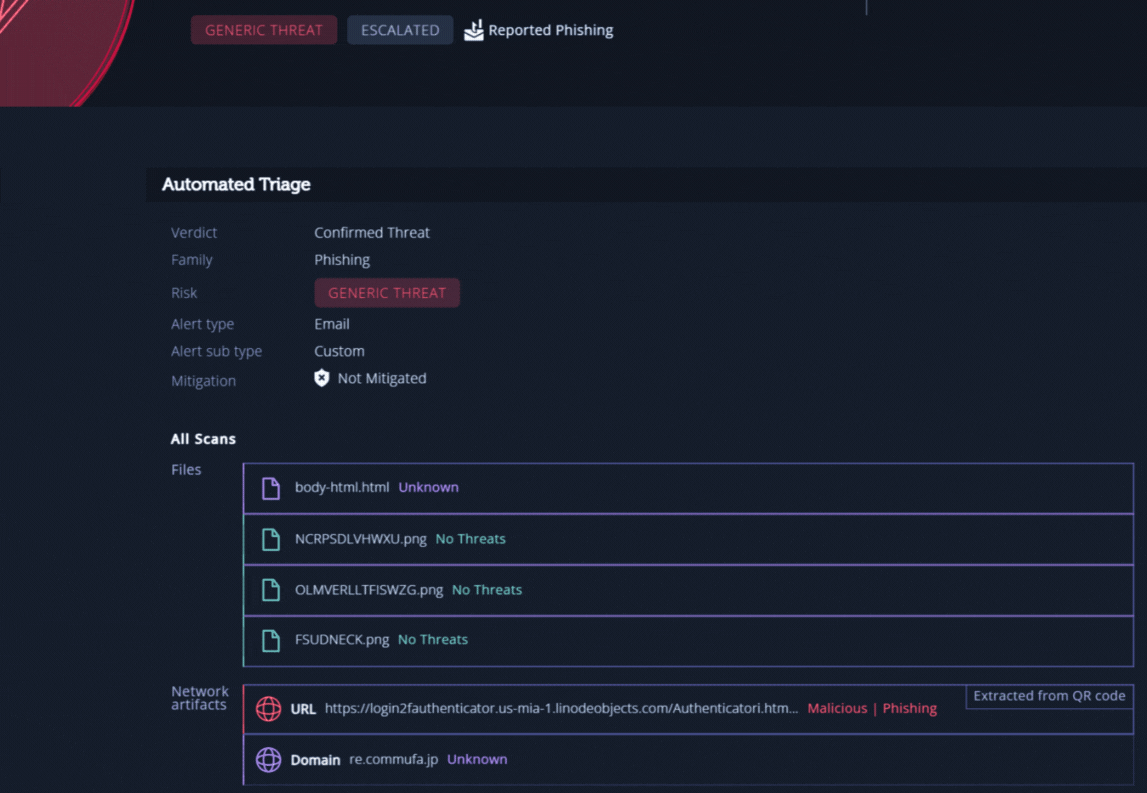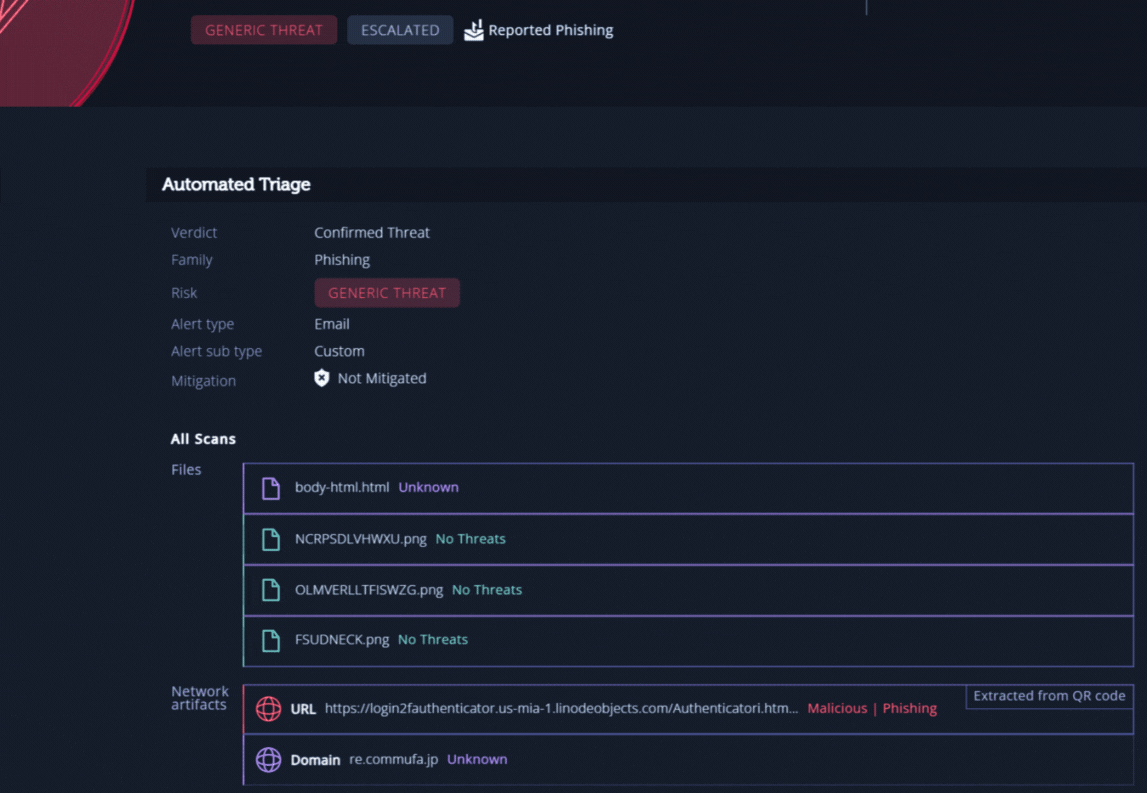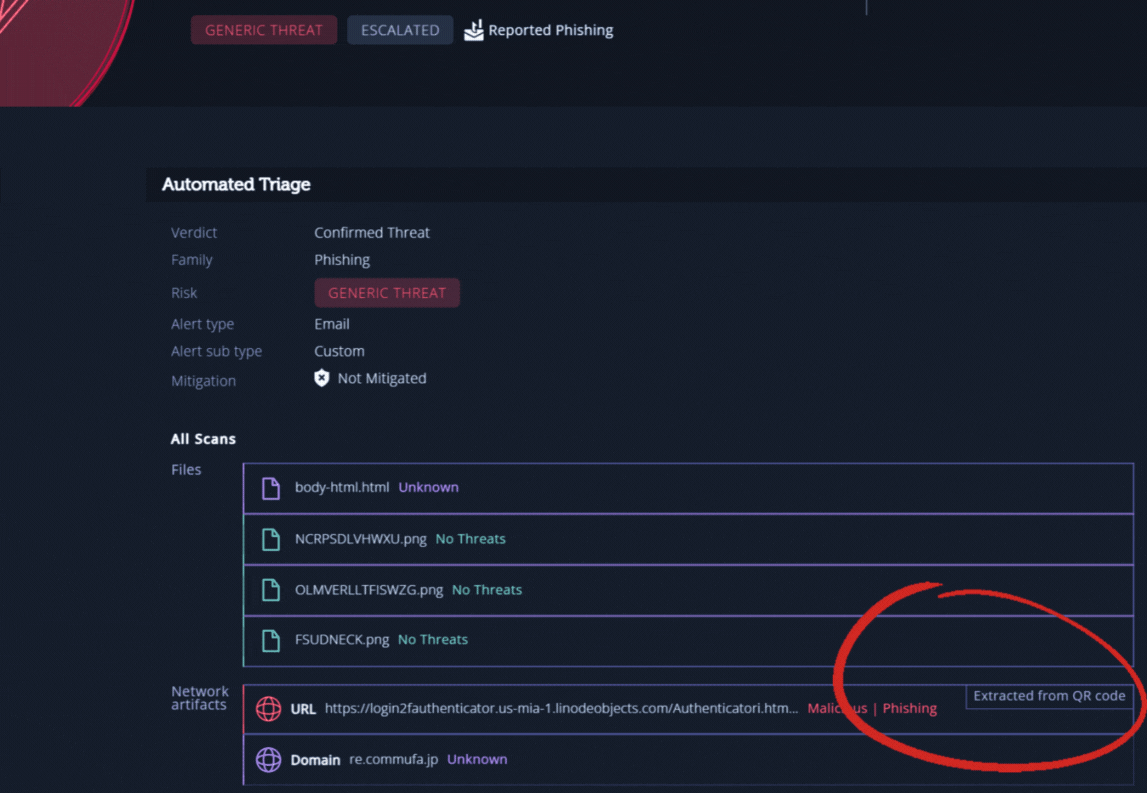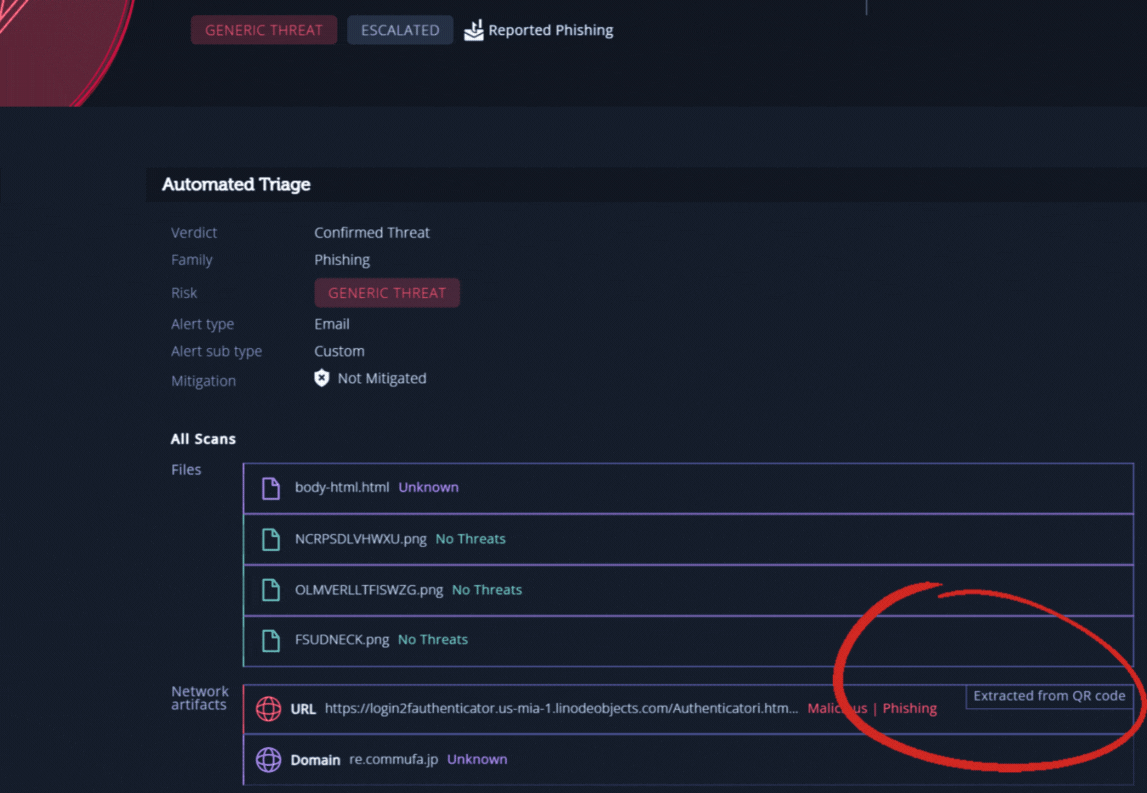
Intezer’s automated triage process extracts and investigates all evidence from the suspicious email, including URLs and links obscured with QR codes. As you can see in the following example, this URL was extracted by Intezer from a QR Code image that was attached to the email (note the “Extracted from QR Code” tag near the bottom):
Securely Triaging Email Attachments & Infected Endpoints
Intezer automatically collects file attachments, privately analyzing them to ensure sensitive information and data in your emails are protected. Intezer supports analysis for the file types most frequently used in phishing attacks, like Microsoft Office files and PDFs, in addition to many other file formats. Intezer combines traditional sandboxing methods with proprietary genetic code analysis technology to quickly investigate malware-related incidents.
If an endpoints could have been infected in a targeted phishing attack, Intezer’s endpoint scanner can perform live memory analysis. This allows Intezer to find any traces of advanced in-memory threats such as malicious code injections, packed and fileless malware, or any unrecognized code. This gives your team comprehensive memory analysis reports, ensuring you can quickly investigate and triage any endpoints that could might be infected during a phishing attack.
Easy Integration and Customizable Notifications
We’ve made it easy to integrate Automated Phishing Investigation into your existing processes, by offering three different options:
- Dedicated Phishing Mailbox: You can set up a dedicated mailbox that forwards all suspected phishing emails to Intezer. This method also works for integrating with third-party mailboxes from email security solutions like Proofpoint, Abnormal Security, or Mimecast. For example, Intezer can automatically collect emails to investigate from Microsoft Office 365’s dedicated mailbox from the Report Phishing add-in.
- Intezer’s API or Python SDK: Submit raw phishing emails (.msg or .eml) directly through our API or via our Python SDK.
- SOAR Playbook for Phishing Incident Response: Submit the suspicious email via Intezer’s SOAR integrations (Splunk SOAR, XSOAR, Chronicle SOAR, Azure Sentinel, etc.).
ServiceNow, Jira, and Other Solutions for Case Management or Escalation
Intezer can connect with the tools your security operations team uses to create tickets or escalate alerts, like ServiceNow or Jira. Intezer typically escalates a small fraction of the total alerts investigated, if you configure Intezer to escalate urgent threats to your team via a specific channel or queue. This enables teams to prioritize incidents that are confirmed as a phishing attacks which requires human intervention.
You can also configure the system to send information and notifications even for emails that weren’t marked as escalated by Intezer. Intezer marks these alerts as “No Action Needed”, but provides full analysis reports for your team to review. This gives you the flexibility to tailor the system to your specific requirements based on Intezer’s investigation results, such as for false positive/benign alerts, or confirmed phishing attacks.
Gaining Insights from Phishing Emails: Shaping Your Security Strategy
One of the most powerful aspects of our Automated Phishing Investigation is the ability to gain periodic insights from the phishing emails reported by your employees. By automatically classifying every suspicious email, you can identify trends in the threat landscape that may otherwise go unnoticed.
These insights can be invaluable in shaping your security strategy. For instance, you might notice an increase in phishing attempts related to a particular malware family or threat actor. This could indicate a targeted attack on your organization or an emerging threat in your industry. With this information, you can take proactive measures to strengthen your defenses and educate your employees about the specific threats they’re likely to encounter.
Furthermore, by understanding the tactics, techniques, and procedures (TTPs) used in these phishing attempts, you can better prepare your organization to recognize and respond to future threats. This proactive approach to security can significantly reduce your risk of a successful phishing attack.
In essence, the Automated Phishing Investigation feature doesn’t just help you respond to phishing attempts—it helps you anticipate them. By providing clear visibility into the threat landscape, it empowers you to stay one step ahead of the attackers.
Start Automating Investigations for User-Reported Phishing
Intezer’s Automated Phishing Investigation is a powerful tool that can significantly streamline your security operation processes, especially when paired with the automated endpoint alert triage. By automating the investigation process, it allows you to focus on the most significant threats and take action quickly, as well as gain insights to improve your security posture overtime.
Existing customers can easily get started. Please refer to our documentation to learn about the options for setting up your automated phishing investigation pipeline or reach out for support getting started.
New customers can see automated phishing investigation in action by booking a demo with us today or signing up for a free account.





