Validating your Software Supply Chain for Tampering
SolarWinds, Codecov and now Kaseya are the latest supply chain attacks we know about. In this post you will find a genetic code analysis of the attack against Kaseya customers as well as our recommendations for software consumers and vendors.REvil Use Case
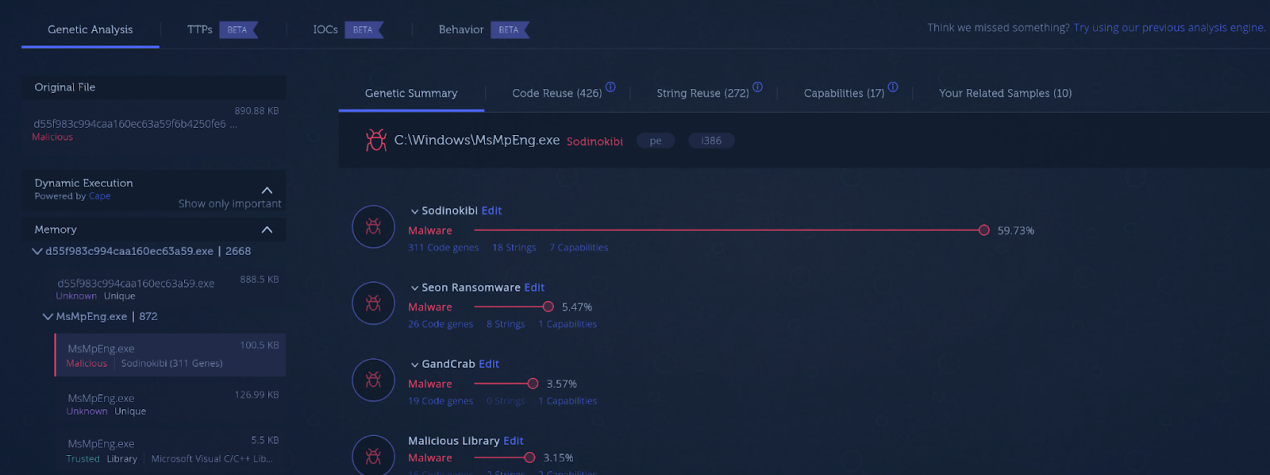
The REvil ransomware gang gained access to the infrastructure of Kaseya, a company that provides IT management software for Managed Service Providers (MSPs) and IT Teams. The attack leveraged a zero-day vulnerability in Virtual Server Agent (VSA) servers to deploy a variant of the REvil ransomware to machines managed by the service. While Kaseya has reported that a small number of their customers were affected, many of these customers are MSPs with large customer bases, essentially resulting in a multiplier effect. The ransom demanded by the group is between $50,000 to $5 million, or $70 million to recover all victims of the attack. So far about 200 companies are reportedly affected by the attack. The supply chain attack is a new infection vector adopted by the REvil gang while using existing malware variants. The shift towards this highly effective infection vector is part of an ongoing trend of attackers delivering their malware through supply chain attacks. Unlike the SolarWinds attack, the REvil group is financially motivated and this attack might be part of a wider campaign. We uploaded the binaries from the attack to Intezer Analyze to check for code reuse and shared capabilities with other malware variants. This is what one of the samples from the attack looks like (Figure 1). The file was dynamically unpacked and executed in a sandbox enabling us to extract and classify all processes and memory dumps relevant to the malware. Intezer Analyze inspected the code that was loaded into memory, detecting the file as malicious and classifying it as REvil ransomware (also known as Sodinokibi).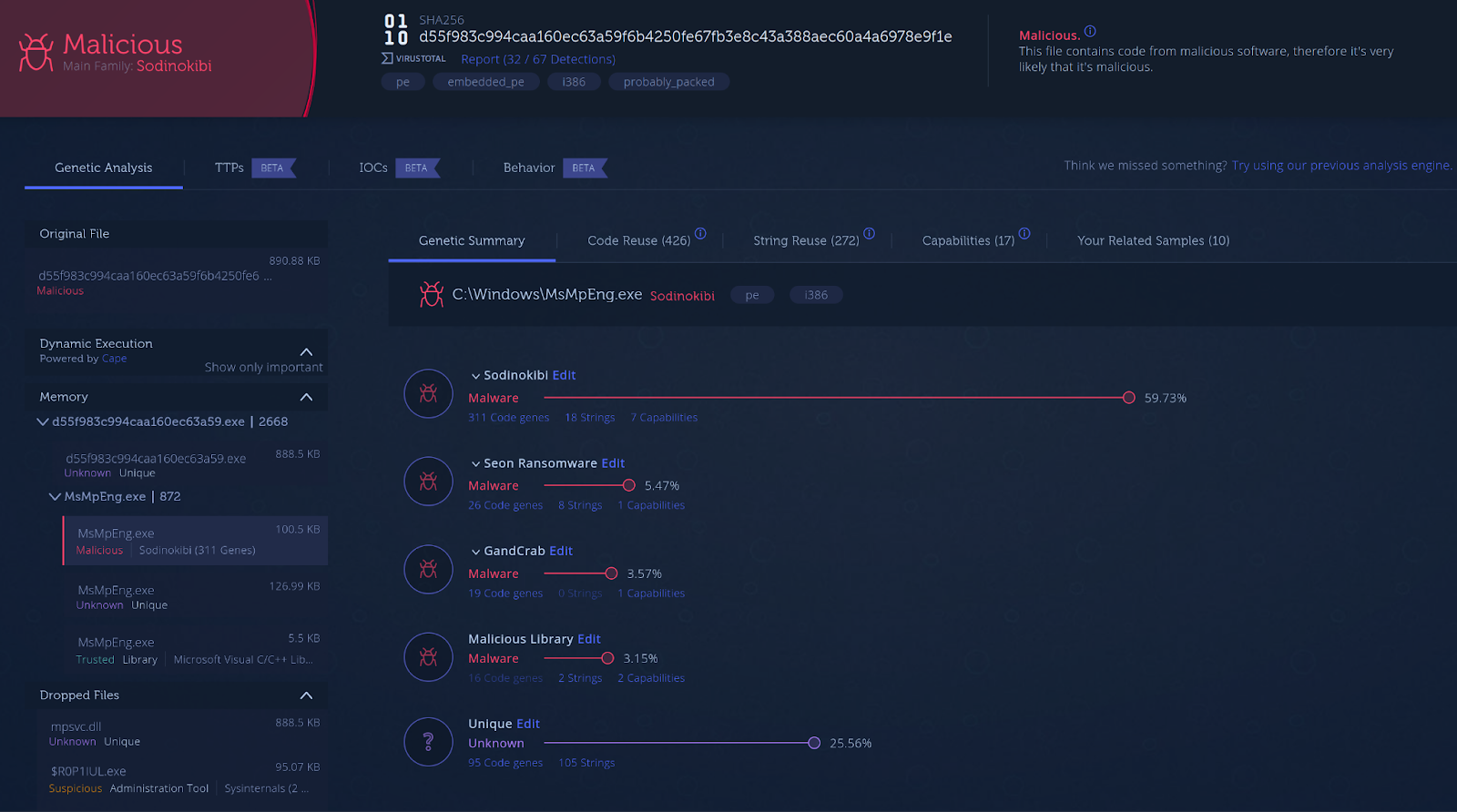
Figure 1: Analysis of one of the binaries in Intezer Analyze.
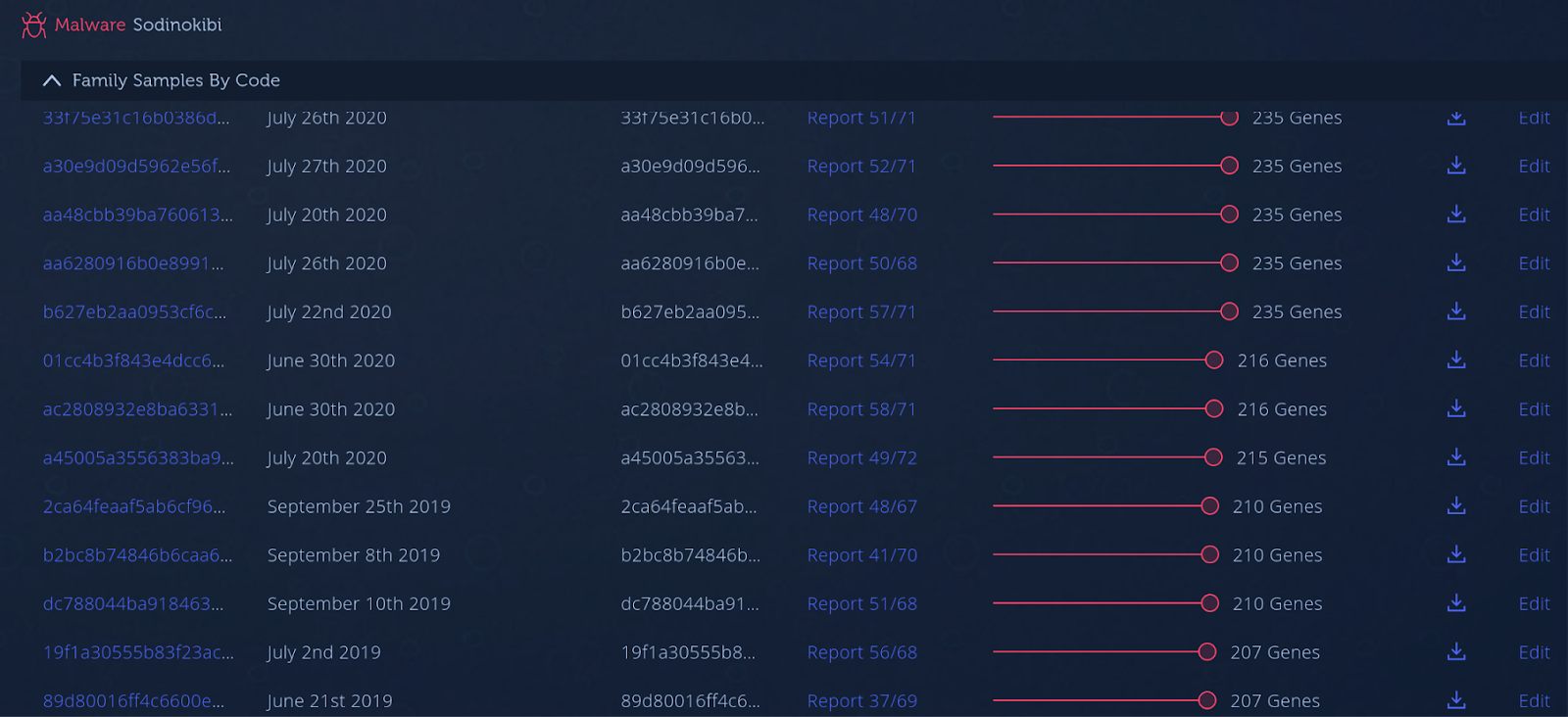
Figure 2: Binary from the Kaseya attack shares code with REvil samples dating back to 2019.
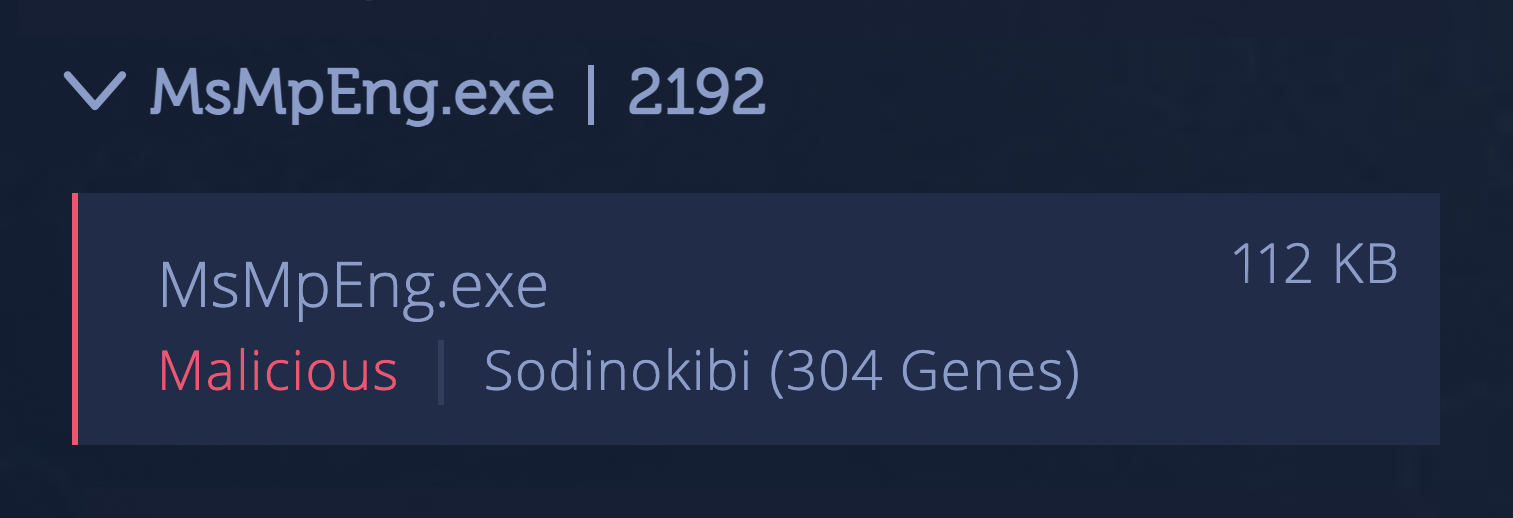
Figure 3: Intezer Analyze picks up the legitimate process name containing Sodinokibi code.

Figure 4: Techniques and capabilities of the malware.
Prepare for the Next Supply Chain Attack
For Third-Party Software Users
- Identifying malicious code and suspicious newly added capabilities to the latest version of the software you are using is the best way to verify that the code was not tampered with. We recommend scanning third-party software and updates before running them in your organization. Learn more about how Intezer Analyze can help you scan your supply chain software for backdoors.
- As demonstrated by this attack and past ransomware supply chain attacks such as NotPetya through the MeDoc software, a company’s first line of defense is only as good as the weakest link of its supply chain security. It is crucial to have a multi-layered Defense in depth (DiD) strategy that will protect your organization if the first line of defense fails. As part of this Defense in depth strategy, use endpoint protection and runtime security on servers and cloud workloads, like Intezer Protect.
- Fileless malware is an imminent threat as it is still one of the most effective ways to bypass malware protection products. Ensure that your malware detection products can handle fileless malware in-memory. Intezer Analyze is one such tool.
- Having backups of data and methods for quickly restoring operations from this data is essential.
For Software Vendors
- Scan software releases for tampering and backdoors before delivering to customers or deploying to production. Learn more on how Intezer can help you release your software with peace of mind.
- Use advanced threat protection and runtime security tools for development and build environments like Intezer Protect.
- Scan your third-party code dependencies for threats.
- Apply strict access control to development and build environments.